A brand new assault dubbed “TunnelVision” can route visitors exterior a VPN’s encryption tunnel, permitting attackers to eavesdrop on unencrypted visitors whereas sustaining the looks of a safe VPN connection.
The tactic, described intimately in a report by Leviathan Safety, depends on the abuse of Dynamic Host Configuration Protocol’s (DHCP) possibility 121, which allows the configuration of classless static routes on a shopper’s system.
The attackers arrange a rogue DHCP server that alters the routing tables so that every one VPN visitors is shipped straight to the native community or a malicious gateway, by no means coming into the encrypted VPN tunnel.
“Our technique is to run a DHCP server on the same network as a targeted VPN user and to also set our DHCP configuration to use itself as a gateway,” reads the report.
“When the traffic hits our gateway, we use traffic forwarding rules on the DHCP server to pass traffic through to a legitimate gateway while we snoop on it.”
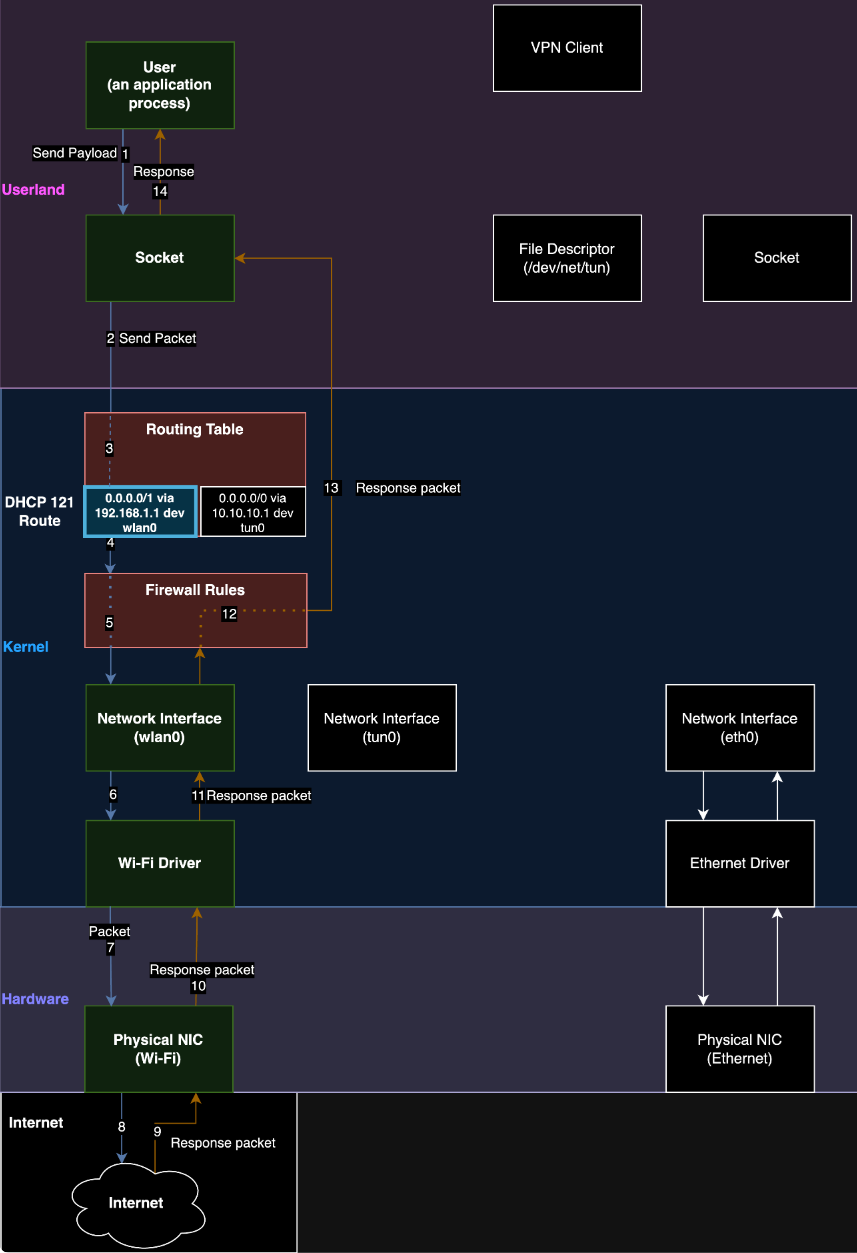
Supply: Leviathan
The difficulty lies in DHCP’s lack of an authentication mechanism for incoming messages that might manipulate routes, and was assigned the vulnerability identifier CVE-2024-3661.
The safety researchers observe that this vulnerability has been accessible for exploitation by dangerous actors since not less than 2002, however there are not any identified circumstances of energetic exploitation within the wild.
Leviathan has knowledgeable lots of the impacted distributors, in addition to CISA and the EFF. The researchers have now publicly disclosed the problem together with a proof-of-concept exploit to lift consciousness and compel VPN distributors to implement safety measures.
Mitigating TunnelVision assaults
Customers are extra apt to be impacted by “TunnelVision” assaults in the event that they join their gadget to a community that’s both managed by the attacker or the place the attacker has a presence. Doable eventualities would come with public Wi-Fi networks like these in espresso retailers, motels, or airports.
The VPN on the focused gadget should be vulnerable to routing manipulation, which Leviathan says is often the case with most VPN shoppers that use system-level routing guidelines with out anti-leak safeguards.
Lastly, computerized DHCP configuration on the goal gadget must be enabled, for the malicious DHCP configuration to be utilized throughout community connection. That is, once more, a generally seen configuration.
Nevertheless, it must be famous that for this assault to work, a consumer should connect with the rogue DHCP server earlier than the community’s reputable one.
The researchers say attackers can enhance the prospect their rogue servers will likely be accessed first in a number of methods, together with DHCP hunger assaults in opposition to the reputable server and ARP spoofing.
The TunnelVision CVE-2024-3661 flaw impacts Home windows, Linux, macOS, and iOS. Attributable to Android not having assist for DHCP possibility 121, it’s the solely main working system not impacted by TunnelVision assaults.
Leviathan proposes the next mitigations for VPN customers:
- Use community namespaces on Linux to isolate community interfaces and routing tables from the remainder of the system, stopping rogue DHCP configurations from affecting VPN visitors.
- Configure VPN shoppers to disclaim all inbound and outbound visitors that doesn’t use the VPN interface. Exceptions must be restricted to mandatory DHCP and VPN server communications.
- Configure techniques to disregard DHCP possibility 121 whereas related to a VPN. This will stop malicious routing directions from being utilized, although it would disrupt community connectivity beneath sure configurations.
- Join through private sizzling spots or inside digital machines (VM). This isolates the DHCP interplay from the host system’s major community interface, lowering the chance of rogue DHCP configurations.
- Keep away from connecting to untrusted networks, particularly when dealing with delicate knowledge, as these are prime environments for such assaults.
As for VPN suppliers, they’re inspired to reinforce their shopper software program to implement their very own DHCP handlers or combine extra safety checks that might block making use of dangerous DHCP configurations.
