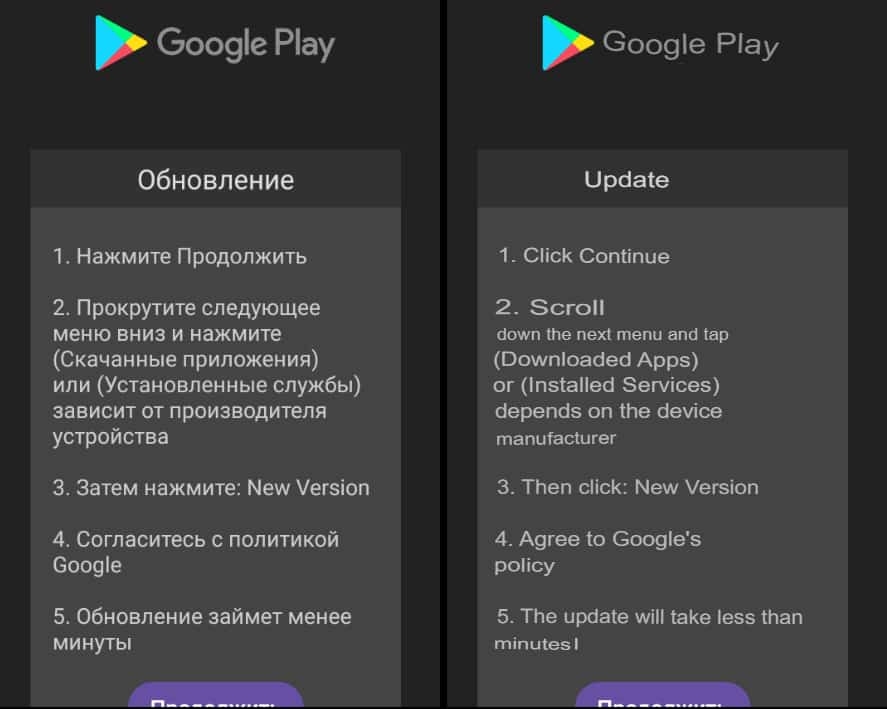
Cyber safety researchers at Cyble have found a brand new and complicated Android malware pressure dubbed “Antidot.” This malware disguises itself as a pretend Google replace, tricking unsuspecting customers into downloading it onto their gadgets. As soon as put in, Antidot targets delicate banking info, posing a major menace to monetary safety.
Modus Operandi of Antidot
The malware operates by distributing itself via phishing campaigns together with SMSishing during which customers obtain SMS messages or notifications that seem like from Google, urging them to replace their software program or safety measures. These messages typically comprise malicious hyperlinks that, when clicked, obtain the Antidot malware disguised as a reliable Google replace package deal (APK).
Upon set up, Antidot seeks to realize administrative privileges on the machine. If profitable, it grants the attacker full management over the machine, permitting them to steal numerous types of delicate information, together with:
- Contact lists
- SMS messages
- Bank card info
- Two-factor authentication codes
- Login credentials for banking apps and on-line accounts.
In keeping with Cyble’s evaluation, Antidot exploits vulnerabilities throughout the Android working system to realize persistence and evade detection. The malware additionally employs strategies to obfuscate its code and communication channels, making evaluation and mitigation tougher.
The danger posed by Antidot is critical. Focusing on banking info makes it a first-rate software for cybercriminals to steal funds. Moreover, management over the contaminated machine permits attackers to launch additional assaults or set up further malware, compromising the person’s privateness and total safety.
“The newly surfaced “Antidot” Banking Trojan stands out for its multifaceted capabilities and stealthy operations. Its utilization of string obfuscation, encryption, and strategic deployment of faux replace pages exhibit a focused method geared toward evading detection and maximizing its attain throughout various language-speaking areas.”
Cyble
Suggestions for Customers and Organizations
Android customers ought to stay vigilant towards the Antidot malware. Listed here are some key factors to remember: Firstly, train warning with unsolicited messages by refraining from clicking on hyperlinks or downloading attachments from unknown senders, even when they appear to originate from respected sources like Google.
Secondly, make sure the authenticity of apps by downloading them solely from official shops just like the Google Play Retailer. Earlier than set up, scrutinize the developer info, opinions, and permissions requested by the app.
Thirdly, improve your account safety by enabling two-factor authentication, which offers a further layer of safety towards unauthorized entry, even within the occasion of credential theft.
Furthermore, often replace your Android machine’s working system and put in apps to mitigate potential vulnerabilities exploited by attackers. Lastly, keep your machine’s defences by putting in a trusted cell safety resolution, which might proactively detect and thwart malware threats earlier than they compromise your machine.
Organizations, then again, ought to contemplate safety consciousness coaching for his or her staff to coach them about phishing ways and the significance of cybersecurity hygiene. Moreover, implementing cell machine administration (MDM) options can present centralized management over gadgets and implement safety insurance policies.
RELATED TOPICS
- Large Head Ransomware Present in Pretend Home windows Updates
- New Vishing Assault Spreading FakeCalls Android Malware
- FakeUpdates Malware Marketing campaign Targets WordPress Websites
- Pretend pockets replace steals 1400BTC ($16M) from Electrum person
- Android Malware Poses as WhatsApp and Instagram to Steal Information