A brand new Android malware known as Trojan Ajina.Banker is focusing on Central Asia – Uncover how this malicious malware disguises itself as reliable apps to steal banking data and intercept 2FA messages. Study in regards to the ways utilized by the attackers and the right way to shield your self from this rising menace.
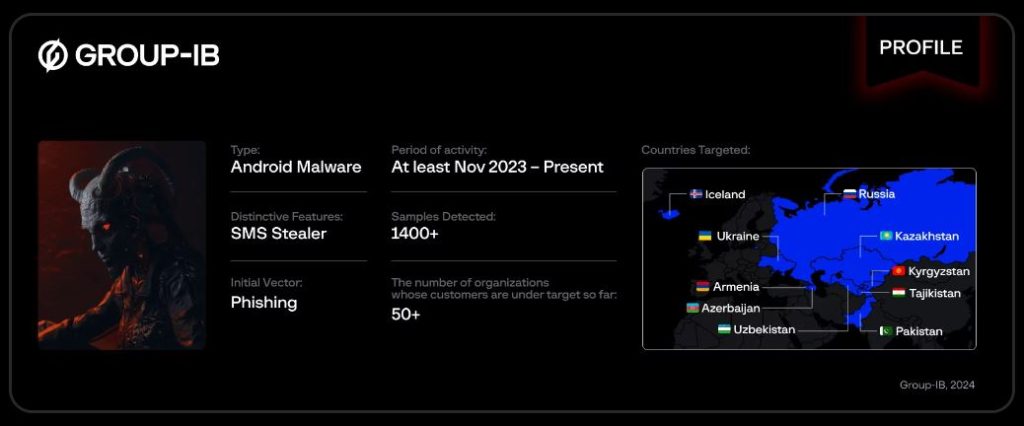
Central Asia has turn into the goal of a malicious new marketing campaign distributing Android malware dubbed “Ajina.Banker.” Found by Group-IB in Could 2024, Ajina.Banker has been wreaking havoc since November 2023 and round 1,400 distinctive variants of the malware had been recognized by researchers.
The malware is known as after a malevolent Uzbek legendary spirit identified for deception, shape-shifting, and chaos. Ajina.Banker targets unsuspecting customers by masquerading as trusted purposes like banking companies, authorities portals, and on a regular basis utilities “to maximize infection rates and entice people to download and run the malicious file, thereby compromising their devices.”
The malware primarily spreads by means of social engineering tactic on messaging platforms like Telegram. Attackers create quite a few accounts to distribute malicious hyperlinks and recordsdata disguised as attractive affords, promotions, and even native tax authority apps. Customers lured by the promise of “lucrative rewards” or “exclusive access” unknowingly obtain and set up the malware, compromising their units.
The attackers additionally make use of a multi-pronged strategy, sending messages with simply the malicious file connected, exploiting person curiosity. Moreover, they share hyperlinks to channels internet hosting the malware, bypassing safety measures in place on some group chats.
Ajina used themed messages and localized promotion methods to create a way of urgency and pleasure in regional group chats, urging customers to click on on hyperlinks or obtain recordsdata with out suspecting malicious intent. These campaigns had been performed throughout a number of accounts, typically concurrently, indicating a coordinated effort.
Whereas primarily focusing on customers in Uzbekistan, Ajina.Banker’s attain extends past borders. The malware collects data on put in monetary purposes from varied nations, together with Armenia, Azerbaijan, Iceland, and Russia. Moreover, it gathers SIM card particulars and intercepts incoming SMS messages, doubtlessly capturing 2FA codes for monetary accounts.
The malware reveals a regarding stage of adaptability. The evaluation reveals two distinct variations – com.instance.smshandler and org.zzzz.aaa – suggesting ongoing improvement. Newer variations showcase further functionalities, together with the power to steal user-provided cellphone numbers, financial institution card particulars, and PIN codes.
Group-IB’s investigation suggests Ajina.Banker operates on an associates program mannequin. A core group manages the infrastructure, whereas a community of associates handles distribution and an infection chains, seemingly incentivized by a share of the stolen funds.
To guard your self and your units from Ajina.Banker and related threats, be cautious of unsolicited messages and downloads, follow trusted app shops like Google Play Retailer, scrutinize app permissions, set up safety software program, and keep up to date on the most recent malware threats and greatest practices for cellular safety.
Rocky Cole, Co-Founder and COO of cellular machine safety firm iVerify shared his feedback about this crafty new marketing campaign with Hackread.com:
“Credential theft is the number one action being taken by threat actors. It’s so easy to steal credentials on phones where smaller screens, lower attention spans, lack of training, and the mixing of personal and professional use cases put people at risk. This new Android malware is just a continuation of that trend and a prime example of why phones should be running EDR platforms to detect malicious APKs and social engineering attempts.”
RELATED TOPICS
- Hackers utilizing Google Websites to unfold banking malware
- Google reveals spy ware assault on Android, iOS, and Chrome
- Scylla Advert Fraud on iOS, Android Customers Halted by Apple, Google
- V3B Phishing Equipment Steals Logins and OTPs from EU Banking Customers
- Android Banking Malware FjordPhantom Steals Through Virtualization