Throughout an investigation into the actions of a menace group offering area identify system (DNS) infrastructure for illicit on-line playing websites, menace researcher Renée Burton found one thing utterly novel: Covert site visitors proof against China’s government-run firewall utilizing open DNS resolvers and mail data to speak.
The China-linked group — dubbed Muddling Meerkat — has demonstrated its capability to get particular DNS packets by the Nice Firewall, one of many applied sciences separating China’s Web from the remainder of the world, Burton, vp of menace analysis at community safety agency Infoblox, wrote in an evaluation printed this week.
Whereas most requests for restricted domains return a seemingly random IP handle, Muddling Meerkat is ready to get DNS mail (MX) data with random-looking prefixes in response to sure requests, even when the area has no mail service.
The aim of the potential stays unclear — most definitely it is for reconnaissance or establishing the foundations of a DNS denial-of-service assault, Burton says — however the demonstrated experience and skill to pierce the GFW deserves extra analysis, she says.
“We have a deliberate, very cunning use using very detailed knowledge of DNS — this is not your average cybercriminal; this is not your average teenager; these people are experts in DNS,” Burton says. “So we have something that has been going on for four and a half years at this point, which isn’t observable in any one location, but is deliberate and constant — and that combination of things, to me, is worrisome.”
The menace analysis comes because the governments of the US and different nations have warned that China’s navy has infiltrated vital infrastructure networks with a aim of pre-positioning their cyber operators for potential future conflicts. Whereas many menace researchers have famous China-linked hacking teams’ experience in discovering and exploiting zero-days in edge units reminiscent of firewalls and digital personal community (VPN) home equipment, the present analysis underscores their capabilities in using the area identify system (DNS) for their very own functions.
Nice Chinese language Firewall: “Operator on the Side”
The Chinese language Communist Occasion prevents its residents from going to content material that the federal government considers inappropriate or unlawful — not by blocking the site visitors, however by returning faux responses to DNS queries that forestall a person in China from connecting to the specified website. The strategy, dubbed the Nice Firewall (GFW), isn’t an inline site visitors filter nor a platform that alters DNS responses on the fly, however moderately an “operator on the side” that points a response that competes with any packet from the unique supposed vacation spot, says Burton.
Whereas the Nice Firewall doesn’t intercept site visitors, China does function one other system — sometimes called the Nice Cannon (GC) — that takes the adversary-in-the-middle (AitM) strategy, modifying packets en path to their vacation spot, she wrote within the report.
“In combination, the GFW and GC create a lot of noise and misleading data that can hinder investigations into anomalous behavior in DNS,” the report stated. “Muddling Meerkat operations are complex and demonstrate that the actor has a strong understanding of DNS, as well as internet savvy.”
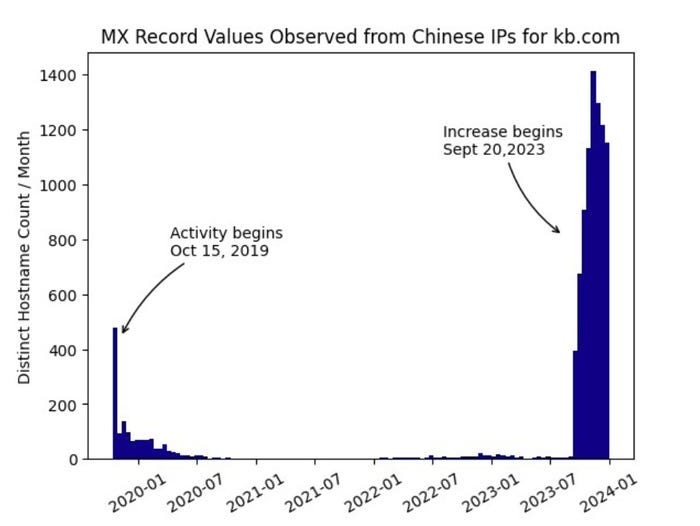
Mail (MX) data from kb.com, despite the fact that the area has no mail service. Supply: Infoblox
Usually, researchers can see the Nice Firewall in operation. After they ship a DNS request to a website thought-about to be out of bounds by the Chinese language authorities, the GFW will return a seemingly random IP handle. After they ask for a non-existent service for that area, reminiscent of a mail (MX) file, the GFW nonetheless sends an IP handle. Nonetheless, Infoblox researchers and their trade companions as an alternative noticed mail data for domains that had no mail providers, and every MX data had a seemingly random, albeit quick, host identify.
Kb.com, for instance, has no MX data, however the researchers have seen numerous mail responses, seemingly from the area for servers with names reminiscent of “pq5bo[.]kb[.]com” and “uff0h[.]kb[.]com”.
Covert Widespread DNS Visitors
The unexplained Web site visitors — which was initially detected way back to Oct. 15, 2019 — may very well be some type of reconnaissance that makes use of open resolvers and “super-aged” domains that foil many DNS block lists, says Burton.
“It’s super under the radar, right? So that’s kind of a recon-y looking thing,” she says. “The other thing about it, though, is it has that DNS denial-of-service aspect. There are concerns that the Chinese are positioning themselves for operations against critical infrastructure, and here they’ve positioned themselves in DNS in a really weird way.”
Mixed with the latest announcement by the US Cybersecurity and Infrastructure Safety Company (CISA) that China is pre-positioning itself inside different organizations’ infrastructures, Infoblox resolve to go public with what the corporate and its nameless companions had found.
Infoblox collaborated with different organizations, which the corporate declined to call as a result of worries of retribution and the potential lack of entry to the DNS exercise information. Whereas the Muddling Meerkat operation seems just like some “slow drip” DNS denial-of-service assaults, figuring out the aim of the site visitors will possible require extra analysis contributors, Burton says.
“I don’t believe there’s anyone who can see this operation in totality,” she says. “Every single piece is seen individually, and then what we did was we brought a bunch of different pieces together, so we could see the whole thing. This is a complete mystery … but it definitely is there.”