B-SIDES LAS VEGAS – Las Vegas – Wednesday, Aug. 7 – Organizations that use the Identified Exploited Vulnerabilities (KEV) catalog to prioritize patching are possible lacking silent modifications to the checklist that would point out that a difficulty’s severity has modified, in accordance with an evaluation introduced on the BSides Las Vegas convention on Aug. 7.
The KEV catalog — which presently consists of greater than 1,140 vulnerabilities which might be recognized to have been exploited within the wild — tracks software program flaws by their Frequent Vulnerabilities and Exposures (CVE) identifier, information the date when the vulnerability was confirmed within the wild and has a flag that signifies whether or not ransomware teams are utilizing the safety points.
But, particular modifications to the information — equivalent to uncommonly quick occasions to remediate vulnerabilities and modifications to the ransomware standing — may give safety groups priceless data, the evaluation acknowledged.
Sadly, the Cybersecurity and Infrastructure Safety Company (CISA), which manages the checklist, doesn’t typically name out these modifications and outliers, says Glenn Thorpe, senior director of safety analysis and detection engineering at GreyNoise Intelligence.
“We who are not bound by its directives forget that this is actually a to-do list,” he says, including: “So, if folks are actually using this to prioritize remediation or some kind of process, they need to know [when] it is updated silently.”
The KEV catalog, launched in November 2021 with 290 exploited vulnerabilities, is maintained by CISA and provides organizations the knowledge essential to prioritize patching flaws which might be presently underneath assault. The checklist, nonetheless, doesn’t rank the severity of points, and vulnerabilities are sometimes not added till properly after the preliminary proof of exploitation involves mild.
Surge From a Cyber Battle
Whereas lower than 3 years outdated, the KEV catalog has already handed by way of three durations, Thorpe says. The unique catalog had 287 vulnerabilities, which had a median age — the time between the discharge of the CVE and the vulnerability’s addition to the KEV checklist — of 591 days. Then, throughout a 109-day interval in early 2022 and the preliminary months of Russia’s invasion of Ukraine, an enormous stockpile of vulnerabilities was exploited, encompassing 396 points with a median age of 1,898 days.
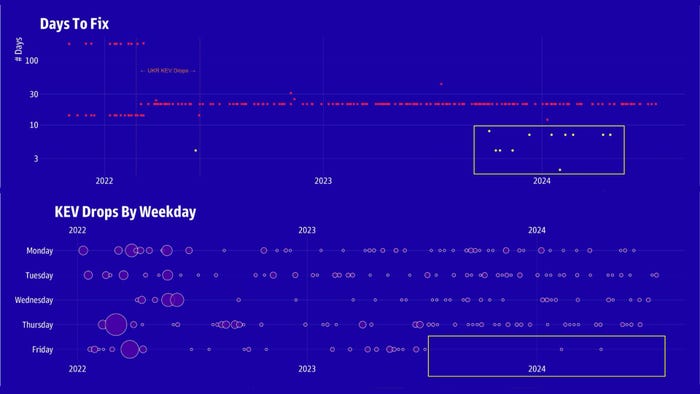
Beginning in mid- to late 2023, CISA began altering its insurance policies on the KEV catalog, offering further alerts as to the severity of a vulnerability. Supply: GreyNoise Intelligence
Since mid-2022, 453 newly exploited vulnerabilities have been found, with a median age of 567 days.
“There is this thought that maybe the numbers have gone down, because the Russia-Ukraine conflict has dragged on so long,” he says. “But I [feel that] when it ends, each side will looking for vulnerabilities and stockpiling once again.”
5 organizations — Microsoft, Apple, Cisco, Adobe, and Google — account for about half of all vulnerabilities on the checklist, demonstrating cyberattackers’ penchant for main software program platforms.
Pay Consideration to Friday Updates
Whereas any vulnerability within the KEV catalog ought to possible be patched as quickly as attainable, firms might need to prioritize these being utilized in ransomware campaigns. The checklist has a flag designating whether or not CISA has confirmed use of a selected flaw by ransomware gangs. Nonetheless, at the very least 41 occasions, that flag has been modified to “known” — indicating ransomware use — after the vulnerability’s addition to the checklist with out specific notification.
Maybe extra crucial for prioritization is the “due date” for fixing a vulnerability, which informs federal companies of the date by which the difficulty should be remediated. Whereas the overwhelming majority of vulnerabilities have a 21-day requirement, since late 2023, CISA has set shorter remediation deadlines for particular vulnerabilities. The shorter patching deadlines are sometimes for extra crucial home equipment which might be related to a networks, such because the extreme Ivanti vulnerabilities, in addition to points in Juniper routers and Cisco gadgets and Atlassian’s Confluence server, GreyNoise’s Thorpe says.
In reality, one other knowledge level means that CISA made different modifications to the way it handles KEV-catalog bulletins in late 2023. Across the identical time that CISA had assigned shorter deadlines, the company additionally started foregoing the discharge of any checklist updates on Fridays, besides in two particular circumstances, the evaluation discovered.
“Either there was a decision made to prioritize these a little differently, or they … were kind of figuring out how to prioritize these differently, because the list is getting big,” Thorpe says.
Organizations can use the coverage modifications inferred from the best way CISA updates the KEV catalog to grasp which points the company considers most important. A KEV replace launched on a Friday needs to be thought-about important, as ought to a vulnerability with a due date lower than 21 days away. Lastly, Thorpe says, updates to the recognized ransomware utilization area are one other sign that safety groups ought to take note of.