Challenge administration platform Monday.com has eliminated its “Share Update” function after risk actors abused it in phishing assaults.
Monday.com is a cloud-based challenge administration platform that permits groups to prepare and handle their work utilizing automated workflows and dashboards. The platform is used by 225,000 clients, together with Coca-Cola, Canva, LionsGate, Oxy, Compass, and Zippo.
On Tuesday, Monday.com clients informed BleepingComputer they have been involved that the corporate was compromised after receiving phishing emails from its electronic mail accounts.
These emails have been despatched utilizing SendGrid and got here from notifications@monday.com, passing SPF, DMARC, and DKIM authentication.
The phishing emails pretended to come back from a “Human Resources” division, asking customers to both acknowledge the “organization’s workplace sex policy” or submit suggestions as a part of a “2024 Employee Evaluation.”
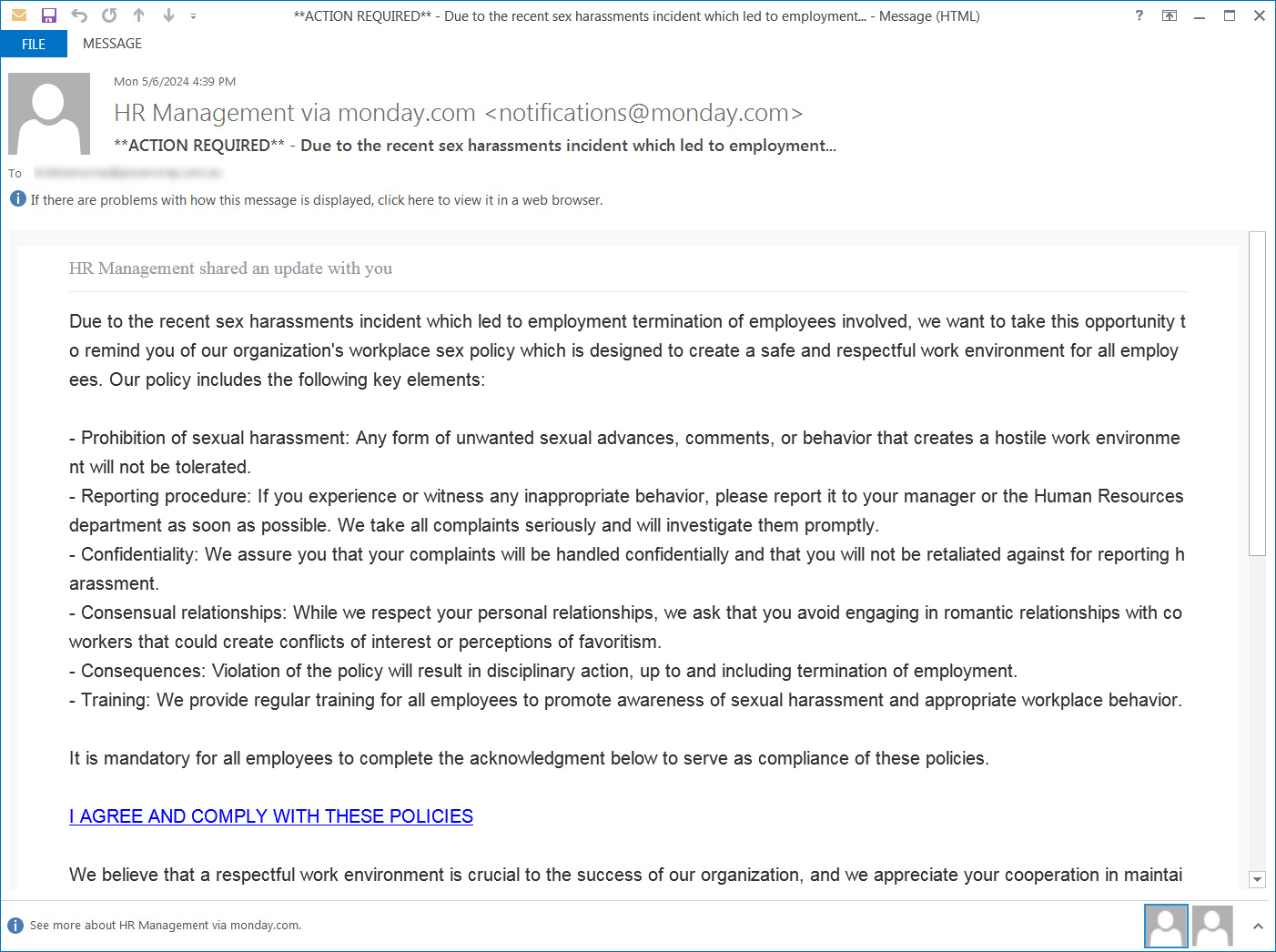
Supply: BleepingComputer
Embedded within the emails have been hyperlinks containing shortened URLs, corresponding to tinyurl.com, that led to phishing types on formstack.com. The types related to these phishing campaigns have since been disabled, so BleepingComputer doesn’t know what info was being collected.
After contacting Monday.com in regards to the phishing assaults earlier this week, they informed BleepingComputer at this time that the assaults have been carried out by their ‘Share Replace’ function.
“We were made aware of the misuse of a monday.com feature named “Share Replace,” which allows users to share an update with someone who isn’t a member of their account,” a Monday.com spokesperson informed BleepingComputer.
“Unfortunately, a user misused this feature by sending a phishing message. We promptly suspended this user and removed the feature.”
“This feature has no connection to data hosted on monday.com or access to any customer accounts or data. We have reached out and shared precautions with the email recipients of the phishing message.”
Monday.com says that the risk actor abused this function by inputting an inventory of electronic mail addresses to which a notification ought to be despatched, which may embody folks outdoors of their group.
When requested how many individuals obtained an electronic mail, they declined to reply for safety causes however stated they contacted all recipients to warn them of the phishing emails.
For individuals who used the ‘Share Replace’ function, Monday.com informed BleepingComputer that it’s beneath overview and can’t present a timeline for when or if the function can be restored.
