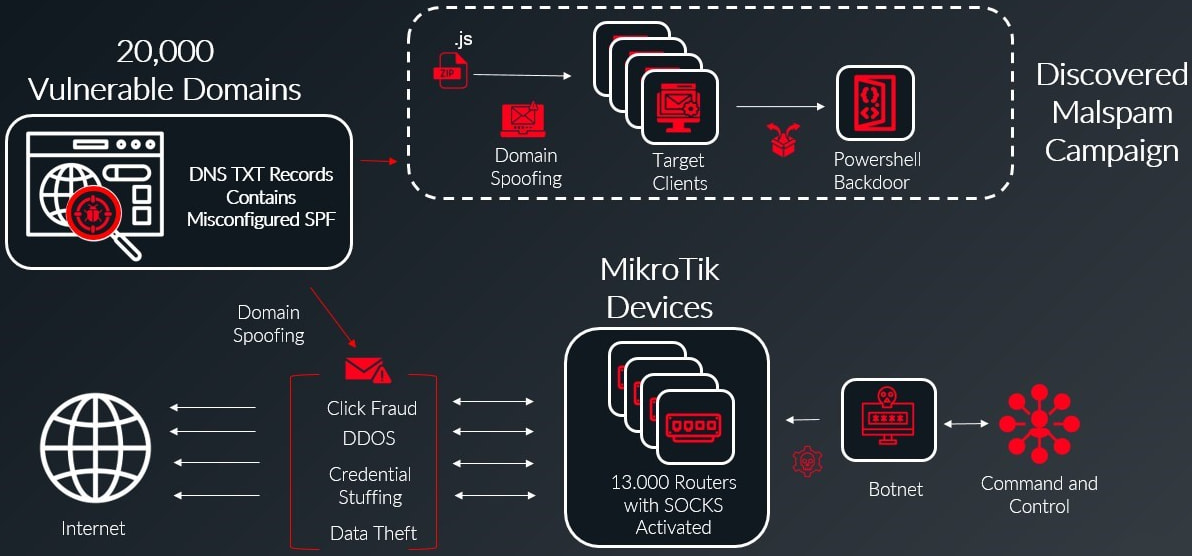
A newly found botnet of 13,000 MikroTik gadgets makes use of a misconfiguration in area title server data to bypass e mail protections and ship malware by spoofing roughly 20,000 net domains.
The risk actor takes benefit of an improperly configured DNS file for the sender coverage framework (SPF) used for itemizing all of the servers licensed to ship emails on behalf of a site.
Misconfigured SPF file
In accordance with DNS safety firm Infoblox, the malspam marketing campaign was lively in late November 2024. A few of the emails impersonated DHL Specific transport firm and delivered pretend freight invoices with a ZIP archive containing a malicious payload.
Contained in the ZIP attachment there was a JavaScript file that assembles and runs a PowerShell script. The script establishes a connection to the risk actor’s command and management (C2) server at a site beforehand tied to Russian hackers.
“The headers of the many spam emails revealed a vast array of domains and SMTP server IP addresses, and we realized we had uncovered a sprawling network of approximately 13,000 hijacked MikroTik devices, all part of a sizeable botnet,” explains Infoblox.
Infoblox explains that SPF DNS data for about 20,000 domains had been configured with the overly permissive “+all” possibility, which permits any server to ship emails on behalf of these domains.
“This essentially defeats the purpose of having an SPF record, because it opens the door for spoofing and unauthorized email sending” – Infoblox
A safer alternative is utilizing the “-all” possibility, which limits e mail sending to the servers specified by the area.
Supply: Infoblox
MikroTik powering one more botnet
The compromise technique stays unclear however Infoblox says they “saw a variety of versions impacted, including recent [MikroTik] firmware releases.”
MikroTik routers are identified for being highly effective and risk actors focused them to create botnets able to very highly effective assaults.
Simply final summer time, cloud providers supplier OVHcloud blamed a botnet of compromised MikroTik gadgets for a large denial-of-service assault that peaked at a file 840 million packets per second.
Regardless of urging MikroTik machine homeowners to replace the methods, lots of the routers stay susceptible for prolonged durations of time due to a very gradual patch price.
The botnet on this case configured the gadgets as SOCKS4 proxies to launch DDoS assaults, ship phishing emails, exfiltrate information, and customarily assist masks the origin of malicious site visitors.
“Even though the botnet consists of 13,000 devices, their configuration as SOCKS proxies allows tens or even hundreds of thousands of compromised machines to use them for network access, significantly amplifying the potential scale and impact of the botnet’s operations,” feedback Infoblox.
MikroTik machine homeowners are suggested to use the newest firmware replace for his or her mannequin, change the default admin account credentials, and shut distant entry to regulate panels if not wanted.
