Microsoft has revealed a “Cyber Signals” report sharing new details about the hacking group Storm-0539 and a pointy rise in reward card theft as we strategy the Memorial Day vacation in america.
The FBI beforehand warned about Storm-0539’s (aka “Ant Lion”) actions earlier this month, highlighting the risk group’s superior methods in conducting reward card theft and fraud, stating that their ways resemble state-sponsored hackers and complicated cyberespionage actors.
Microsoft warns that the risk actors improve their exercise earlier than a main vacation, seeing a 60% improve in Storm-0539 exercise throughout final 12 months’s winter holidays (Christmas) and a notable 30% rise between March and Might 2024.
Within the newly launched Cyber Indicators report, Microsoft corroborates that the risk actors goal organizations that difficulty reward playing cards quite than finish customers, whereas additionally revealing large-scale abuse of cloud service suppliers for low-cost operations.
Storm-0539 profile and modus operandi
Storm-0539 is a Moroccan financially motivated risk group lively since 2021, primarily specializing in reward card and cost card fraud.
The risk actors are infamous for his or her reconnaissance efforts and custom-crafted e-mail and SMS phishing messages, which goal staff of focused organizations, usually reward card issuers.
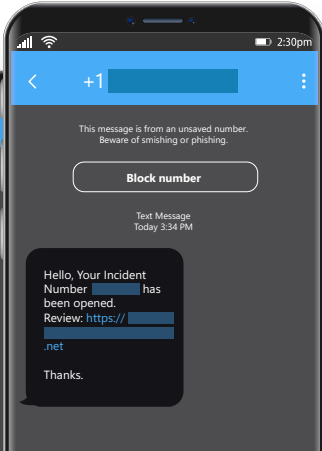
Supply: Microsoft
As soon as they acquire entry to the goal atmosphere utilizing stolen accounts, they register their very own units with the corporate’s multi-factor authentication (MFA) platforms for persistence after which transfer laterally by compromising digital machines, VPNs, SharePoint, OneDrive, Salesforce, and Citrix environments.
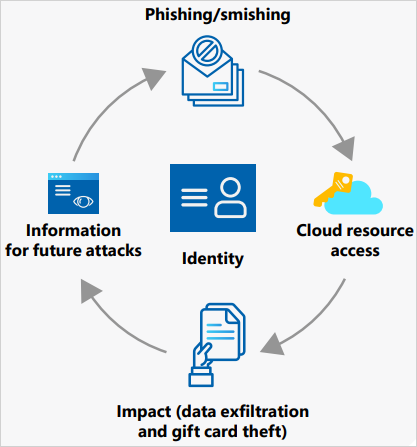
Supply: Microsoft
Finally, Storm-0539 will get entry to credentials that enable them to create new reward playing cards to redeem on darkish internet markets, in shops, or by cashing them out utilizing cash mules.
“Typically, organizations set a limit on the cash value that can be issued to an individual gift card. For example, if that limit is $100,000, the threat actor will issue a card for $99,000 then send themselves the gift card code and monetize them,” explains Microsoft’s Cyber Indicators report.
“Their primary motivation is to steal gift cards and profit by selling them online at a discounted rate.”
“We’ve seen some examples where the threat actor has stolen up to $100,000 a day at certain companies.”
To create new infrastructure for his or her assaults, the risk actors create web sites impersonating non-profit organizations, which are used to enroll with cloud service suppliers. These accounts be a part of “pay as you go” or “free trial” tiers, which they abuse in large-scale operations for little to no price.
“Storm-0539’s reconnaissance and ability to leverage cloud environments are similar to what Microsoft observes from state-sponsored threat actors, showing how techniques popularized by espionage and geopolitical-focused adversaries are now influencing financially motivated criminals,” explains Microsoft.
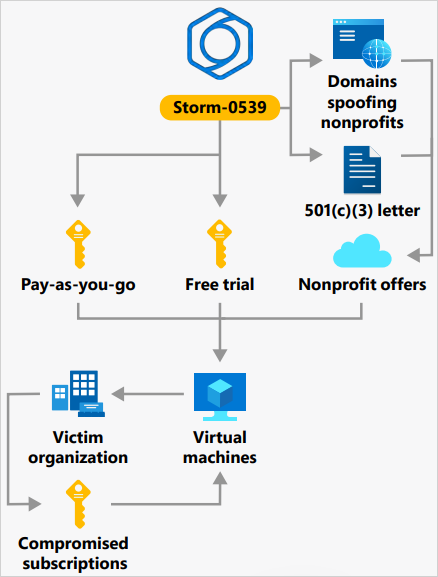
Supply: Microsoft
Protection suggestions
Microsoft means that reward card issuing portal operators continually monitor for anomalies and implement conditional entry insurance policies that would forestall a single, probably hijacked account from producing an unusually massive variety of playing cards.
Moreover, organizations are suggested to implement token replay safety measures, implement least privilege entry, and use FIDO2 safety keys to guard high-risk accounts.
Retailers also can play an important function in disrupting the revenue chain for Storm-0539 and related risk actors by recognizing and rejecting orders that carry suspicious indicators.
Though these assaults don’t affect vacation buyers, web customers making ready for Memorial Day ought to keep elevated warning in opposition to scams, pretend outlets, and malvertising.
