A just lately disclosed Microsoft SharePoint distant code execution (RCE) vulnerability tracked as CVE-2024-38094 is being exploited to realize preliminary entry to company networks.
CVE-2024-38094 is a high-severity (CVSS v3.1 rating: 7.2) RCE flaw impacting Microsoft SharePoint, a extensively used web-based platform functioning as an intranet, doc administration, and collaboration device that may seamlessly combine with Microsoft 365 apps.
Microsoft mounted the vulnerability on July 9, 2024, as a part of the July Patch Tuesday package deal, marking the difficulty as “important.”
Final week, CISA added CVE-2024-38094 to the Recognized Exploited Vulnerability Catalog however didn’t share how the flaw was exploited in assaults.
A brand new report from Rapid7 this week sheds mild on how attackers exploit the SharePoint flaw, stating it was utilized in a community breach they have been introduced to research.
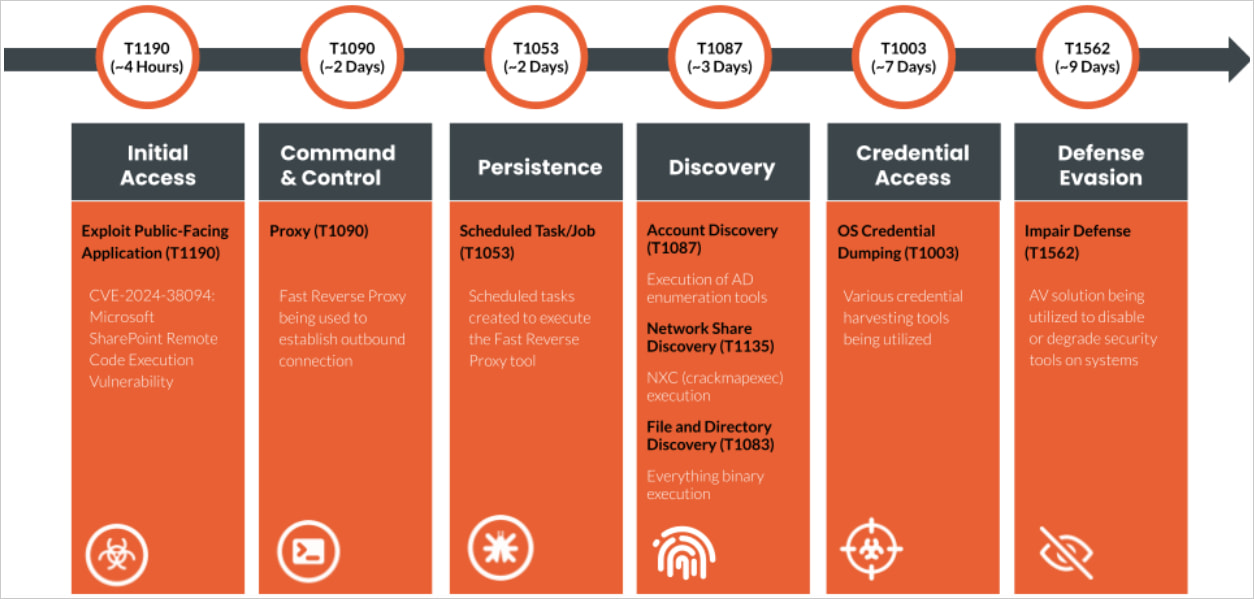
“Our investigation uncovered an attacker who accessed a server without authorization and moved laterally across the network, compromising the entire domain,” reads the associated report.
“The attacker remained undetected for two weeks. Rapid7 determined the initial access vector to be the exploitation of a vulnerability, CVE 2024-38094, within the on-premise SharePoint server.”
Utilizing AVs to impair safety
Rapid7 now reviews that attackers used CVE-2024-38094 to realize unauthorized entry to a susceptible SharePoint server and plant a webshell. The investigation confirmed that the server was exploited utilizing a publicly disclosed SharePoint proof-of-concept exploit.
Leveraging their preliminary entry, the attacker compromised a Microsoft Trade service account with area administrator privileges, gaining elevated entry.
Subsequent, the attacker put in the Horoung Antivirus, which created a battle that disabled safety defenses and impaired detection, permitting them to put in Impacket for lateral motion.
Particularly, the attacker used a batch script (‘hrword set up.bat’) to put in Huorong Antivirus on the system, arrange a customized service (‘sysdiag’), execute a driver (‘sysdiag_win10.sys’), and run ‘HRSword.exe’ utilizing a VBS script.
This setup precipitated a number of conflicts in useful resource allocation, loaded drivers, and lively companies, inflicting the corporate’s authentic antivirus companies to crash being rendered powerless.
Supply: Rapid7
Within the following stage, the attacker used Mimikatz for credential harvesting, FRP for distant entry, and arrange scheduled duties for persistence.
To keep away from detection, they disabled Home windows Defender, altered occasion logs, and manipulated system logging on the compromised techniques.
Extra instruments akin to the whole lot.exe, Certify.exe, and kerbrute have been used for community scanning, ADFS certificates technology, and brute-forcing Energetic Listing tickets.
Third-party backups have been additionally focused for destruction, however the attackers failed of their makes an attempt to compromise these.
Though trying to erase backups is typical in ransomware assaults, to forestall straightforward restoration, Rapid7 didn’t observe information encryption, so the kind of the assault is unknown.
With lively exploitation underway, system directors who haven’t utilized SharePoint updates since June 2024 should accomplish that as quickly as attainable.
