Microsoft says it is going to enhance safety throughout Entra tenants the place safety defaults are enabled by making multifactor authentication (MFA) registration necessary.
This transfer is a part of the corporate’s Safe Future Initiative, launched in November 2023, to spice up cybersecurity safety throughout its merchandise.
“We’re removing the option to skip multifactor authentication (MFA) registration for 14 days when security defaults are enabled. This means all users will be required to register for MFA on their first login after security defaults are turned on,” mentioned Microsoft’s Nitika Gupta on Wednesday.
“This will help reduce the risk of account compromise during the 14-day window, as MFA can block over 99.2% of identity-based attacks.”
This transformation will have an effect on all newly created tenants beginning on December 2nd, 2024, and can start rolling out to current tenants beginning in January 2025.
Microsoft Entra safety defaults is a setting that robotically allows varied safety features to guard organizations from frequent assaults, reminiscent of password sprays, replay, and phishing.
Since October 22, 2019, new tenants have robotically had safety defaults enabled, and older tenants have had it robotically enabled over time if they don’t seem to be utilizing conditional entry, have premium licenses, or are utilizing legacy authentication purchasers.
To allow safety defaults, you could check in to the Microsoft Entra admin middle (at the least as a Safety Administrator), browse to Identification > Overview > Properties, and choose Handle safety defaults. From there, set “Security defaults” to Enabled and click on Save.
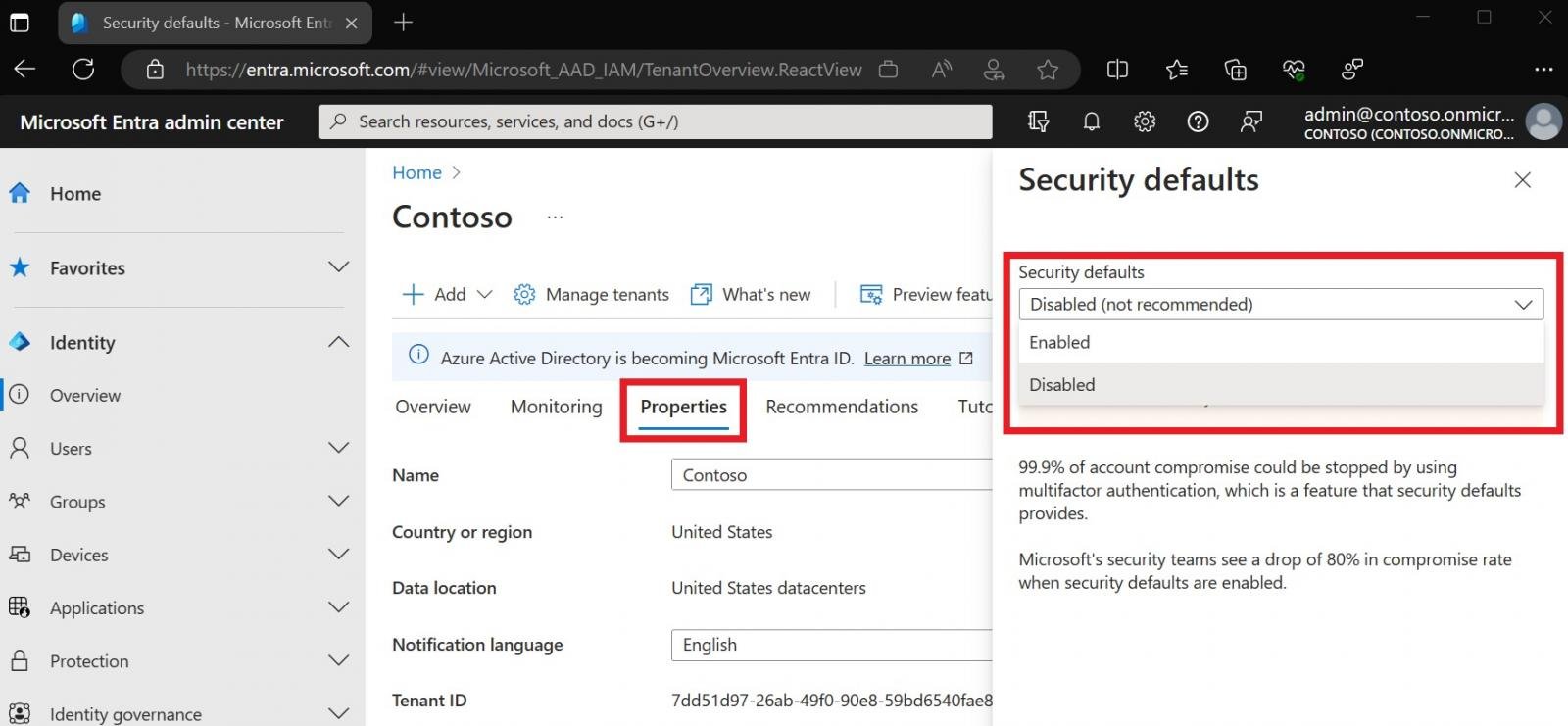
Admins not utilizing Conditional Entry are suggested to allow safety defaults for his or her group as a result of they supply a easy and efficient method to defend customers and sources from frequent threats.
Nevertheless, though safety defaults supply a superb safety posture baseline, they do not permit for the customization supplied by Conditional Entry insurance policies that complicated organizations require.
In August, Microsoft additionally warned Entra international admins to allow MFA for his or her tenants till October fifteenth to make sure customers do not lose entry to admin portals. By implementing necessary MFA for all Azure sign-in makes an attempt, Microsoft goals to guard Azure accounts towards hijacking and phishing makes an attempt.
The corporate additionally introduced in November that it will roll out Conditional Entry insurance policies requiring MFA for all admins signing into Microsoft admin portals (e.g., Entra, Microsoft 365, Change, and Azure), for customers on all cloud apps, and high-risk sign-ins.
In January, Microsoft-owned GitHub additionally started implementing two-factor authentication (2FA) for all energetic builders as a part of the corporate’s ongoing effort to spice up MFA adoption.
