SaaS Safety agency AppOmni has recognized misconfigurations in Microsoft Energy Pages that may result in extreme information breaches. Study in regards to the widespread points that expose delicate info and the best way to defend your information in SaaS functions.
A current discovery by AppOmni, a SaaS safety firm, revealed a safety vulnerability in Microsoft Energy Pages, a low-code platform over 250 million folks use month-to-month. This concern has led to the publicity of tens of millions of delicate information data throughout numerous organizations in private and non-private sectors, “spanning financial services, healthcare, automotive and more,” defined AppOmni’s chief of SaaS safety analysis, Aaron Costello in a report shared with Hackread.com.
This, in accordance with researchers, contains the UK’s Nationwide Well being Service (NHS), which leaked info for over 1.1 million NHS workers, together with electronic mail addresses, cellphone numbers, and residential addresses.
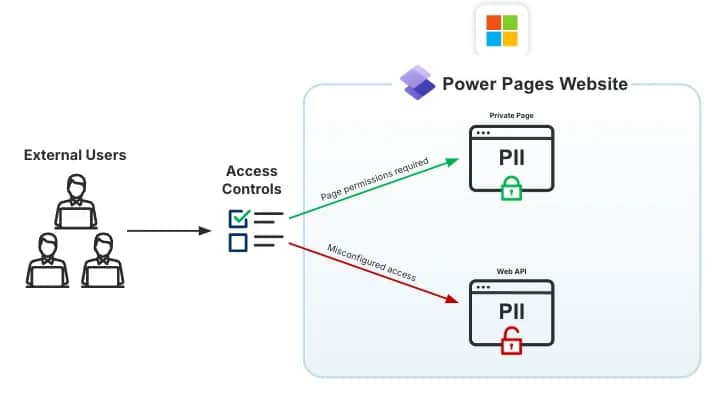
The foundation trigger of those information leaks lies in misconfigured entry controls inside Energy Pages for creating Dataverse-integrated functions like net portals. Nevertheless, its customizable nature can expose delicate information to the general public.
How Does It Occur?
Energy Pages, a robust device for constructing customized web sites, depends on a layered strategy to entry management. This contains site-level, table-level, and column-level permissions. Nevertheless, when organizations misconfigure these settings, they unintentionally expose delicate information to the general public web.
Organizations can enhance the potential assault floor by exposing extra columns than essential to the Net API. It could occur by setting the Webapi/<object>/fields worth to * permits entry to all columns inside a desk, making delicate info weak, AppOmni defined within the weblog put up.
Enabling open registration and exterior authentication can grant unauthorized customers entry to delicate information. That’s as a result of, upon deployment, a web site routinely permits self-registration and login by default, though these pages might not be seen on the platform. Customers can register and authenticate via APIs, with ‘Authenticated Users’ having extra permissions than ‘Anonymous Users’.
One other widespread mistake is granting international entry to nameless customers, permitting anybody to view and doubtlessly exploit delicate info. Failing to implement column safety, even when table-level permissions are accurately configured, can depart delicate columns weak to publicity. Lastly, not utilizing information masking methods can expose delicate info like PII in plain textual content.
“These exposures are significant – Microsoft Power Pages is used by over 250 million users every month, as well as industry-leading organizations and government entities, spanning financial services, healthcare, automotive and more,” mentioned Aaron.
“It’s clear that organizations need to prioritize security when managing external-facing websites, and balance ease of use with security in SaaS platforms – these are the applications holding the bulk of confidential corporate data today, and attackers are targeting them as a way into enterprise networks.”
The results of those misconfigurations may be extreme, as proven by the NHS information leak. By exposing delicate info, organizations threat compromising their fame, going through authorized repercussions, and doubtlessly exposing their techniques to additional assaults.
This vulnerability additionally reveals the dangers related to mismanaging entry controls in SaaS functions, particularly when coping with delicate information. Organizations ought to place correct safety measures to handle safety in SaaS platforms, which these days maintain the majority of confidential company information.
Moreover, usually auditing entry controls, limiting entry to delicate information, implementing robust authentication and authorization mechanisms, and staying up to date on rising safety threats and vulnerabilities can considerably cut back the danger of knowledge breaches and defend delicate info.
RELATED TOPICS
- Nespresso Area Hijacked to steal Microsoft Logins
- 250 million Microsoft consumer assist data leaked in plain textual content
- Microsoft Bookings Flaw Permits Account Hijack, Impersonate
- Microsoft Bing server leaked consumer search queries, location information
- Hackers Might Exploit Microsoft Groups on macOS to Steal Information