Microsoft’s Digital Crimes Unit (DCU) has seized 240 domains utilized by clients of ONNX, a phishing-as-a-service (PhaaS) platform, to focus on corporations and people throughout america and worldwide since at the very least 2017.
Based on Microsoft’s Digital Protection Report 2024, ONNX (beforehand often known as Caffeine) was the highest Adversary within the Center (AitM) phishing service by quantity of phishing messages throughout the first half of 2024. Tens to tons of of hundreds of thousands of phishing emails focused Microsoft 365 accounts every month and clients of assorted different tech corporations.
“These ‘do it yourself’ kits make up a significant portion of the tens to hundreds of millions of phishing messages observed by Microsoft each month and the fraudulent ONNX operation was a top 5 supplier in the first half of 2024,” Microsoft advised BleepingComputer.
“The fraudulent ONNX operation offered phishing kits designed to target a variety of companies across the technology sector, including Google, DropBox, Rackspace, and Microsoft.”
ONNX promoted and offered the phish kits on Telegram utilizing a number of subscription fashions (Fundamental, Skilled, and Enterprise), starting from $150 to $550 month-to-month.
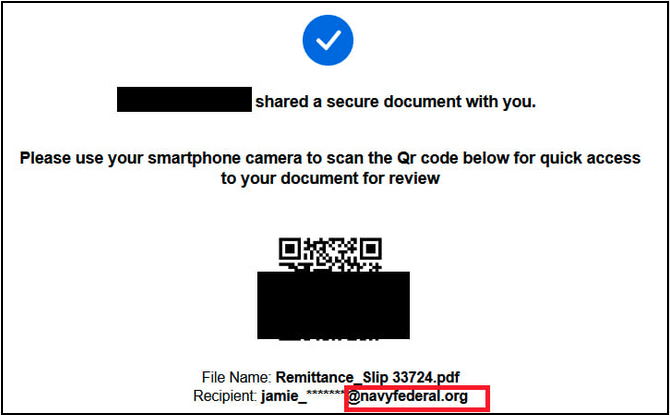
The assaults, additionally managed through Telegram bots, got here with built-in two-factor authentication (2FA) bypass mechanisms and most not too long ago focused monetary corporations’ staff (at banks, credit score union service suppliers, and personal funding corporations) utilizing QR code phishing (also referred to as quashing) techniques.
These emails included PDF attachments containing malicious QR codes that redirected potential victims to pages resembling reliable Microsoft 365 login pages and requested them to enter their credentials.
“Threat actors leverage quishing attacks because victims will typically scan QR codes on their personal mobile devices (which the victim may use for business purposes, as part of their firms’ Bring Your Own Device (BYOD) program),” U.S. securities business regulator FINRA additionally warned in a latest alert. “As a result, these attacks are exceptionally difficult to monitor with typical endpoint detection.”
Cybercriminals utilizing ONNX have been notably efficient in finishing up their assaults because the phishing kits assist bypass two-factor authentication (2FA) by intercepting 2FA requests. In addition they use bulletproof internet hosting providers that delay phishing domains’ takedowns and encrypted JavaScript code that decrypts itself throughout web page load, including an additional layer of obfuscation to evade detection by anti-phishing scanners.
“These attacks present a unique challenge for cybersecurity providers as they appear as an unreadable image to security and scanning features,” stated Steven Masada, Assistant Normal Counsel at Microsoft’s Digital Crimes Unit, right now.
ONNX operations abruptly stopped in June after Darkish Atlas safety researchers found and disclosed its proprietor’s identification, Abanoub Nady (additionally identified on-line as MRxC0DER).
“Through a civil court order unsealed today in the Eastern District of Virginia, this action redirects the malicious technical infrastructure to Microsoft, severing access of threat actors, including the fraudulent ONNX operation and its cybercrime customers, and permanently stopping the use of these domains in phishing attacks in the future,” Masada added.
“Our goal in all cases is to protect customers by severing malicious actors from the infrastructure required to operate and to deter future cybercriminal behavior by significantly raising the barriers of entry and the cost of doing business. We are joined by co-plaintiff LF (Linux Foundation) Projects, LLC, the trademark owner of the actual registered ‘ONNX’ name and logo.”
Yow will discover the entire checklist of 240 domains seized within the motion within the unsealed criticism appendixes.
In October, Microsoft and the Justice Division additionally disrupted Russian ColdRiver FSB hackers’ assault infrastructure by seizing over 100 domains utilized in spear-phishing assaults towards U.S. authorities staff and Russian nonprofit organizations.
Final December, the corporate’s Digital Crimes Unit additionally took motion towards a serious cybercrime-as-a-service supplier (Storm-1152) that registered over 750 million fraudulent Microsoft electronic mail accounts and raked in hundreds of thousands by promoting them to different cybercriminals.
