American semiconductor provider Microchip Know-how Integrated has confirmed that worker data was stolen from techniques compromised in an August cyberattack, which was later claimed by the Play ransomware gang.
Headquartered in Chandler, Arizona, the chipmaker has round 123,000 prospects from a number of business sectors, together with industrial, automotive, shopper, aerospace and protection, communications, and computing markets.
On August 20, Microchip Know-how disclosed that operations at a number of manufacturing services had been affected by a cyberattack found on August 17. The incident impacted the corporate’s means to fulfill orders and compelled it to close down a few of its techniques and isolate the affected ones to comprise the breach.
In a Wednesday submitting with the U.S. Securities and Change Fee, Microchip Know-how revealed that its operationally crucial IT techniques at the moment are again on-line, with operations “substantially restored” and the firm processing buyer orders and transport merchandise for over every week.
Microchip Know-how added that the attackers had stolen some worker knowledge from its techniques however it has but to search out proof that buyer data was additionally exfiltrated through the breach.
“While the investigation is continuing, the Company believes that the unauthorized party obtained information stored in certain Company IT systems, including, for example, employee contact information and some encrypted and hashed passwords. We have not identified any customer or supplier data that has been obtained by the unauthorized party,” Microchip Know-how mentioned.
“The Company is aware that an unauthorized party claims to have acquired and posted online certain data from the Company’s systems. The Company is investigating the validity of this claim with assistance from its outside cybersecurity and forensic experts.”
Assault claimed by Play ransomware
Microchip Know-how continues to be evaluating the extent and influence of the cyberattack with assist from exterior cybersecurity specialists. It is also nonetheless restoring IT techniques that had been impacted within the incident. Regardless of nonetheless engaged on restoration after the assault, the corporate says it has been processing buyer orders and transport merchandise for over every week.
Regardless that Microchip Know-how continues to be investigating the character and scope of the cyberattack, the Play ransomware gang claimed duty on August 29, when it added the American chipmaker to its knowledge leak web site on the darkish net.
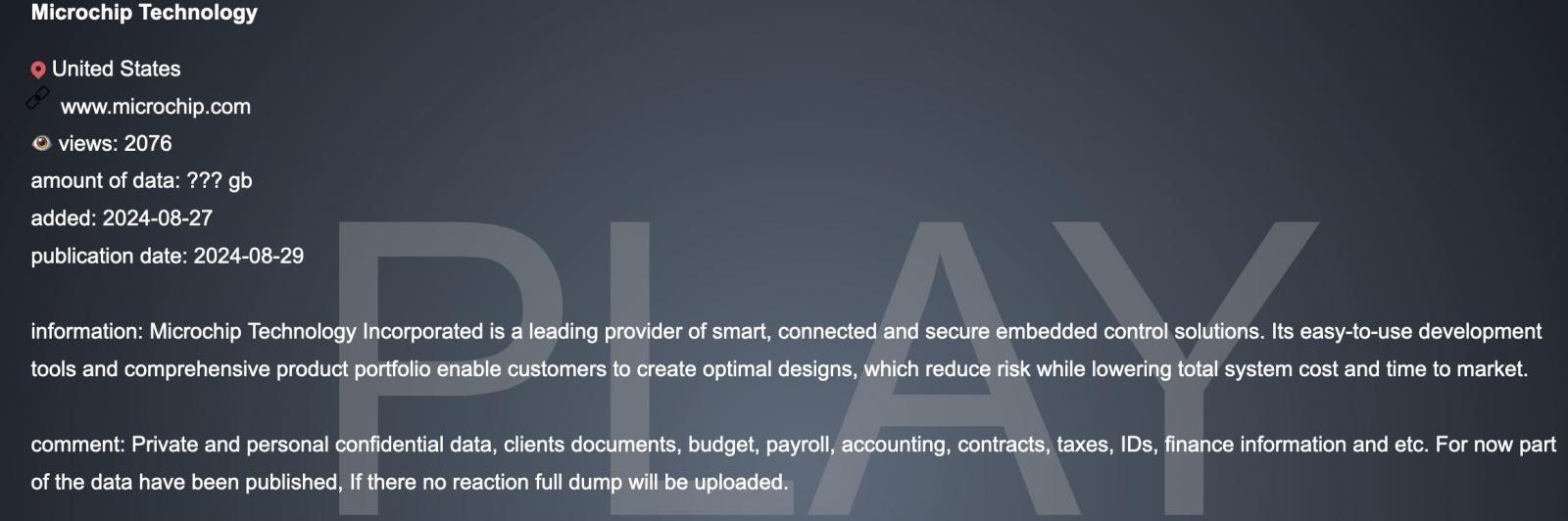
They claimed to have stolen a variety of knowledge from Microchip Know-how’s compromised techniques, together with “private and personal confidential data, clients documents, budget, payroll, accounting, contracts, taxes, IDs, finance information,” and extra.
The ransomware gang has since partially leaked the allegedly stolen knowledge and threatened to leak the remainder of it if the corporate would not react to the leak.
Play ransomware emerged in June 2022, with preliminary victims searching for assist by BleepingComputer’s boards. Play operators steal delicate knowledge from compromised techniques to make use of in double-extortion schemes, placing strain on victims to pay a ransom in the event that they need to keep away from having their knowledge leaked on-line.
Notable Play ransomware victims embody cloud computing firm Rackspace, automobile retailer big Arnold Clark, the Belgian metropolis of Antwerp, the Metropolis of Oakland in California, and, most not too long ago, Dallas County.
In collaboration with CISA and the Australian Cyber Security Centre (ACSC), the FBI additionally issued a joint advisory in December warning that this ransomware group had breached round 300 organizations globally as of October 2023.
