A malware botnet named ‘Pumpkin Eclipse’ carried out a mysterious harmful occasion in 2023 that destroyed 600,000 workplace/house workplace (SOHO) web routers offline, disrupting prospects’ web entry.
In keeping with researchers at Lumen’s Black Lotus Labs, who noticed the incident, it disrupted web entry throughout quite a few Midwest states between October 25 and October 27, 2023. This left homeowners of the contaminated units with no possibility however to exchange the routers.
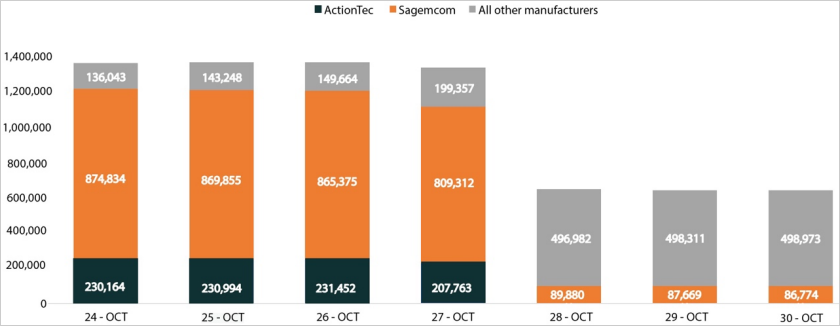
Though large-scale, the incident had a targeted impression, affecting a single web service supplier (ISP) and three fashions of routers utilized by the agency: the ActionTec T3200s, ActionTec T3260s, and Sagemcom F5380.
Black Lotus Labs says the actual ISP serves weak communities in the USA and suffered a 49% discount in working modems because of the ‘Pumpkin Eclipse’ incident.
Supply: Black Lotus Labs
Whereas Black Lotus didn’t title the ISP, it bears a hanging resemblance to a Windstream outage that occurred throughout the identical timeframe.
Beginning on October 25, 2023, Windstream prospects started reporting on Reddit that their routers had been not working.
“So I’ve had a T3200 modem for a while now, but today, something happened that I’ve never experienced before. The internet light is showing solid red. What does it mean, and how do I fix it?,” reported a consumer within the Winstream subreddit.
“Mine went down about 9PM last night, ignored until I had time to troubleshoot this afternoon. After going through the chatbot (and the T3200 not responding to the factory reset), it was pretty clear the router was the problem,” mentioned one other consumer.
Subscribers impacted by the Windstream outage had been instructed they wanted to exchange the routers with a brand new one to revive their web entry.
When contacted in regards to the incident, Windstream instructed BleepingComputer that they don’t have a remark.
Pumpkin Eclipse assault
Quick ahead seven months and a new report by Black Lotus might lastly shed some gentle on the incident, explaining {that a} botnet was accountable for bricking 600,000 routers throughout the midwest states at a single ISP in October 2023.
“Lumen Technologies’ Black Lotus Labs identified a destructive event, as over 600,000 small office/home office (SOHO) routers were taken offline belonging to a single internet service provider (ISP). The incident took place over a 72-hour period between October 25-27, rendered the infected devices permanently inoperable, and required a hardware-based replacement. Public scan data confirmed the sudden and precipitous removal of 49% of all modems from the impacted ISP’s autonomous system number (ASN) during this time period.”
❖ Black Lotus Labs
The researchers could not discover the vulnerability used for preliminary entry, so the attackers both used an unknown zero-day flaw or exploited weak credentials together with an uncovered administrative interface.
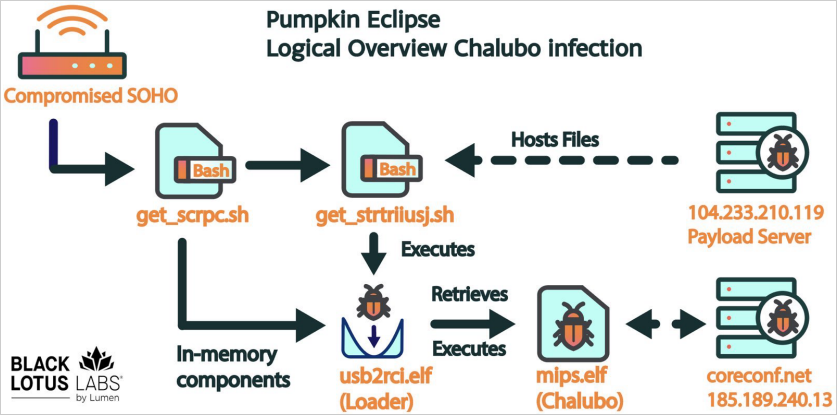
The primary stage payload is a bash script named “get_scrpc,” which executes to fetch a second script referred to as “get_strtriiush,” which is accountable for retrieving and executing the first bot payload, ‘Chalubo’ (“mips.elf”).
Chalubo is executed from reminiscence to evade detection and makes use of ChaCha20 encryption when speaking with command and management (C2) servers to guard the communication channel, whereas it wipes all information from the disk and adjustments the method title as soon as it is operating.
The attacker can ship instructions to the bot via Lua scripts, which allow information exfiltration, downloading of further modules, or introducing new payloads on the contaminated machine.
Supply: Black Lotus Labs
Upon execution, which features a 30-minute delay to evade sandboxes, the bot collects host-based info such because the MAC deal with, machine ID, machine kind, machine model, and native IP deal with.
Chalubo has distributed denial of service (DDoS) performance, indicating Pumpkin Eclipse’s operational targets. Nevertheless, Black Lotus Labs didn’t observe any DDoS assaults from the botnet.
The analysts observe that Chalubo misses a persistence mechanism, so rebooting the contaminated router disrupts the bot’s operation.
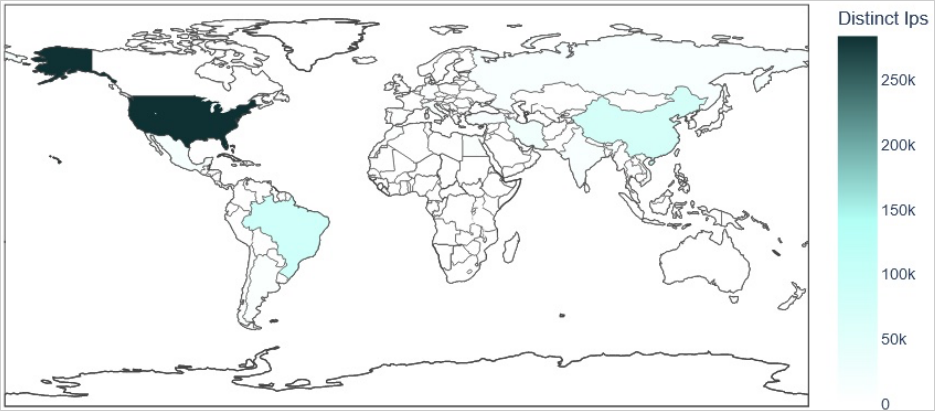
Black Lotus Labs says its telemetry information signifies that Chalubo operates 45 malware panels speaking over 650,000 distinctive IP addresses from October 3 to November 3, most based mostly in the USA.
Supply: Black Lotus Labs
Solely one in every of these panels was used for the harmful assault and it targeted on a selected American ISP, inflicting Black Lotus researchers to imagine that the attacker bought the Chalubo panel for the particular objective of deploying the harmful payload on routers.
“The second unique aspect is that this campaign was confined to a particular ASN. Most previous campaigns we’ve seen target a specific router model or common vulnerability and have effects across multiple providers’ networks. In this instance, we observed that both Sagemcom and ActionTec devices were impacted at the same time, both within the same provider’s network. This led us to assess it was not the result of a faulty firmware update by a single manufacturer, which would normally be confined to one device model or models from a given company. Our analysis of the Censys data shows the impact was only for the two in question. This combination of factors led us to conclude the event was likely a deliberate action taken by an unattributed malicious cyber actor, even if we were not able to recover the destructive module.” – Black Lotus
Sadly, the researchers couldn’t discover the payload used to brick the routers, so that they had been unable to find out the way it was completed or for what objective.
Black Lotus Labs notes that that is the primary time, other than the “AcidRain” incident, {that a} botnet malware was ordered to destroy its hosts and trigger large-scale monetary harm by imposing {hardware} replacements.