In a latest wave of cyberattacks, IT professionals have turn out to be the goal of a crafty malvertising marketing campaign uncovered by Zscaler ThreatLabz researchers Roy Tay and Sudeep Singh.
In response to the corporate’s analysis, this marketing campaign leverages misleading on-line ads to distribute a beforehand unseen backdoor named “MadMxShell.” It began in March 2024, when Zscaler ThreatLabz found a menace actor utilizing look-alike domains to distribute MadMxShell, using DLL sideloading, DNS protocol abuse, and reminiscence forensics safety options.
Researchers consider the attackers have displayed a calculated method. Between November 2023 and March 2024, attackers registered a number of domains carefully resembling these of widespread IP scanner and community administration software program, together with Superior IP Scanner, Indignant IP Scanner, PRTG IP Scanner by Paessler, Handle Engine, and community admin duties associated to VLANs.
This tactic is called typosquatting. It creates a excessive likelihood that the domains will seem on prime searches and IT professionals would possibly click on on the malicious commercial by mistake.
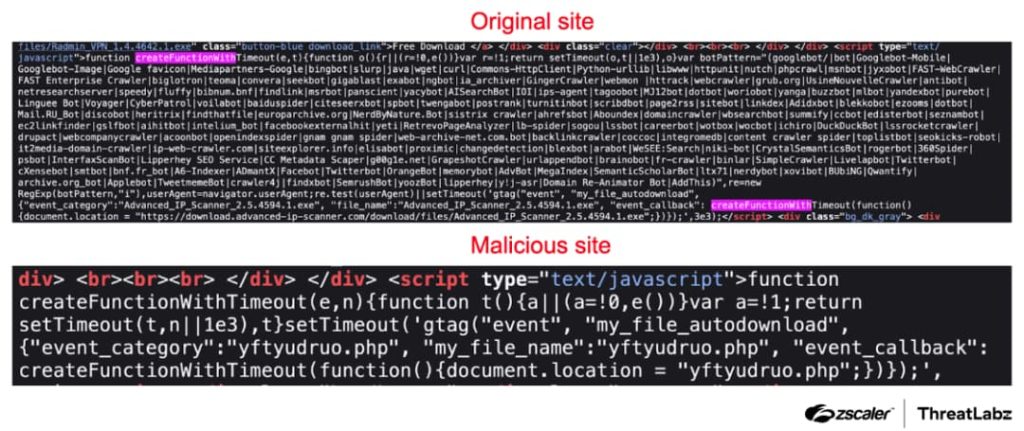
As soon as clicked, the advert redirects the consumer to a touchdown web page designed to appear like the real software program vendor’s web site. Right here, they’re offered with a downloadable file that, unbeknownst to them, harbours the MadMxShell backdoor.
New Backdoor with Evasive Methods
As per Zscaler’s weblog publish, the MadMxShell backdoor employs a multi-stage deployment course of designed to evade detection by conventional safety options. The preliminary payload leverages DLL sideloading, a method the place a legit program is tricked into loading a malicious library file. This malicious library then downloads extra elements that set up communication with the attacker’s command-and-control (C2) server.
One of the crucial regarding features of MadMxShell is its use of DNS MX report queries for C2 communication. This method leverages the usual Area Title System (DNS) protocol in an unconventional technique to masks communication with the attacker’s infrastructure. Moreover, MadMxShell employs anti-dumping methods to stop reminiscence evaluation, making it tough for safety researchers to know its inside workings.
Defending Your Methods:
To mitigate dangers, be cautious of unsolicited advertisements, allow pop-up blockers, keep sturdy safety software program, and educate workers concerning the risks of malvertising and social engineering ways.
Jason Soroko, Senior Vice President of Merchandise at Sectigo commented on the brand new marketing campaign. “Defenders don’t usually look for malicious control communications (C2) in email exchange DNS traffic, so the attackers in this case found a place to hide. The attackers also employ a technique that blocks the ‘dumping’ of memory for analysis by endpoint security solutions,” Jason defined.
“Malvertising isn’t new, nevertheless, the malware methods getting used right here show that the know-how pipeline of the attackers is deep and a substantial amount of thought has been put into hiding at nighttime corners of networking and working programs,“ he needed.
RELATED TOPICS
- Provocative Fb Adverts Ship NodeStealer Malware
- New VPN Malvertising Assault Drops OpcJacker Crypto Stealer
- Malvertising assault drops malicious Chrome extensions, backdoors
- Tens of millions of PornHub customers affected by a year-long malvertising assault
- Massive Head Ransomware Discovered in Malvertising, Faux Home windows Updates