A big-scale malvertising marketing campaign distributed the Lumma Stealer info-stealing malware via pretend CAPTCHA verification pages that immediate customers to run PowerShell instructions to confirm they aren’t a bot.
The marketing campaign leveraged the Monetag advert community to propagate over a million advert impressions every day throughout three thousand web sites.
The malicious operation, dubbed “DeceptionAds” by Guardio Labs and Infoblox researchers, is believed to be carried out by the menace actor often called “Vane Viper.”
Evolving the ClickFix tactic
DeceptionAds could be seen as a more moderen and extra harmful variant of the “ClickFix” assaults, the place victims are tricked into working malicious PowerShell instructions on their machine, infecting themselves with malware.
ClickFix actors have employed phishing emails, pretend CAPTCHA pages on pirate software program websites, malicious Fb pages, and even GitHub points redirecting customers to harmful touchdown pages.
What GuardioLabs found is completely different from earlier operations because it makes use of large-scale promoting on a professional advert community to take unsuspecting customers casually shopping the online on to pretend CAPTCHA pages.
Particularly, the menace actors use the Monetag advert community to serve pop-up adverts selling pretend provides, downloads, or companies, that typically enchantment to the viewers of the host websites, usually pirate streaming and software program platforms.

Supply: GuardioLabs
As soon as the sufferer clicks on the advert, obfuscated code checks whether or not they’re an precise particular person and, if validated, redirects the customer to a pretend CAPTCHA web page via the BeMob cloaking service.
Though BeMob is used for professional functions like advert efficiency monitoring, in “Deception Ads,” it is used solely for evasion.
“By supplying a benign BeMob URL to Monetag’s ad management system instead of the direct fake captcha page, the attackers leveraged BeMob’s reputation, complicating Monetag’s content moderation efforts,” explains Nati Tal, head of Guardio Labs.
.jpg)
Supply: GuardioLabs
The CAPTCHA web page features a JavaScript snippet that silently copies a malicious PowerShell one-line command to the consumer’s clipboard with out them realizing it.
Subsequent, the web page gives directions to the sufferer on how you can paste the “CAPTCHA solution” into the Home windows Run dialog and execute it. This step runs the PowerShell command, which downloads Lumma Stealer from a distant server and executes it on the sufferer’s system.

Supply: GuardioLabs
Lumma Stealer is a complicated information-stealing malware that steals cookies, credentials, passwords, bank cards, and shopping historical past from Google Chrome, Microsoft Edge, Mozilla Firefox, and different Chromium browsers.
The malware may also steal cryptocurrency wallets, non-public keys, and textual content recordsdata more likely to comprise delicate data, similar to these named seed.txt, go.txt, ledger.txt, trezor.txt, metamask.txt, bitcoin.txt, phrases, pockets.txt, *.txt, and *.pdf.
This knowledge is collected into an archive and despatched again to the attacker, the place they will use the knowledge in additional assaults or promote it on cybercrime marketplaces.
GuardioLabs reported the large-scale abuse to each Monetag and BeMob. The primary responded by eradicating 200 accounts utilized by the menace actor in eight days, whereas the latter acted to cease the marketing campaign in 4 days.
Though this successfully disrupted the malicious operation, GuardioLabs noticed a resurgence on December 11, indicating that the menace actors tried to renew operations via a special advert community.
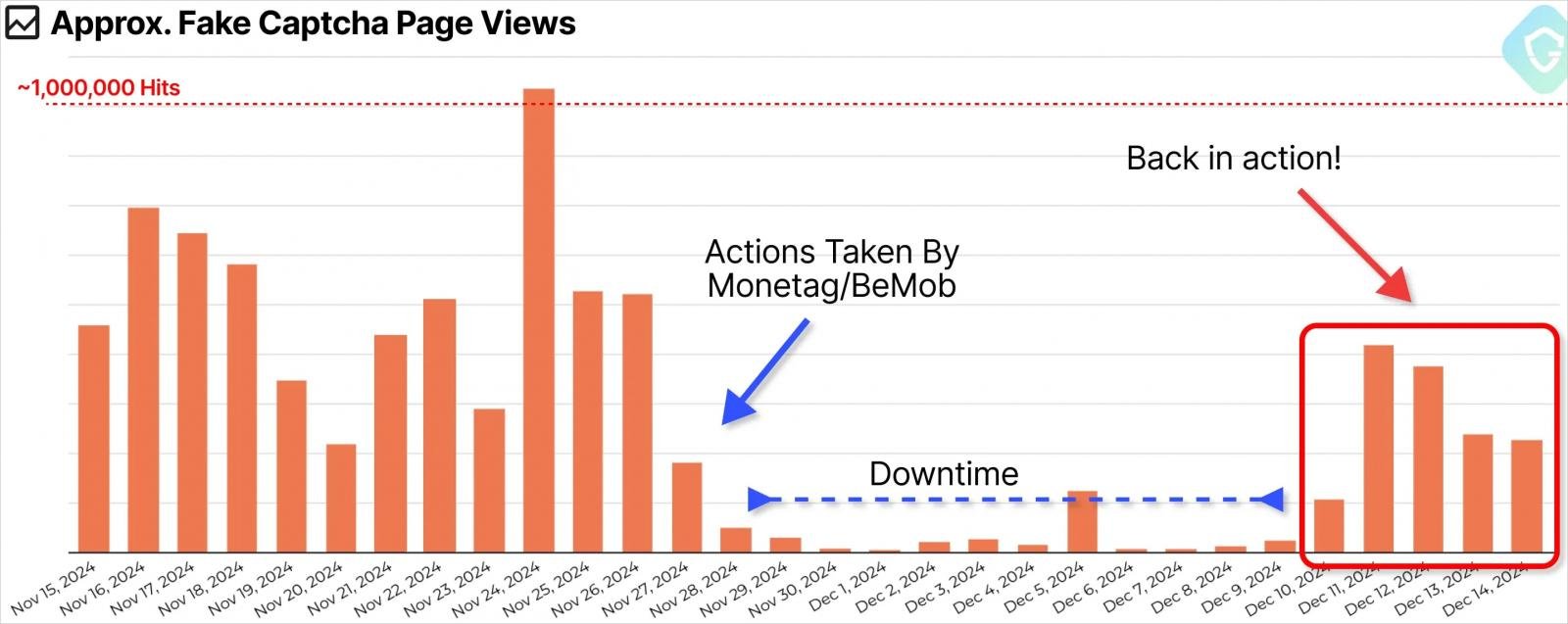
Supply: GuardioLabs
Infostealer campaigns have turn into a huge world operation over the previous yr and could be devastating for customers and organizations, resulting in monetary fraud, privateness dangers, knowledge breaches, and full-blown ransomware assaults.
In Could, menace actors used credentials stolen by infostealers to conduct the huge SnowFlake account breaches, which impacted quite a few firms, together with Ticketmaster, AT&T, and Advance Auto Components.
To remain clear from infostealer infections, don’t ever execute any instructions prompted by web sites, particularly these pretending to be fixes or captchas.
Additionally, utilizing pirated software program or unlawful streaming websites will increase the probability of such infections, as advert networks serving them have a extra lax coverage, and the positioning house owners largely care about quickly monetizing their house and site visitors reasonably than constructing a repute for trustworthiness.
