McAfee Labs uncovers malicious GitHub repositories distributing Lumma Stealer malware disguised as recreation hacks and cracked software program. Discover ways to defend your self.
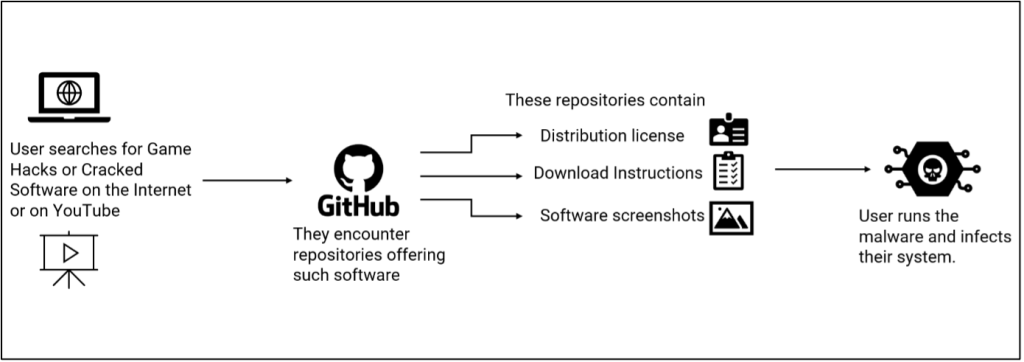
McAfee Labs, the risk analysis arm of cybersecurity big McAfee, has lately uncovered a disturbing pattern: the exploitation of well-liked platforms like GitHub to distribute malware. Their analysis reveals a community of malicious repositories providing seemingly reputable content material akin to recreation hacks, cracked software program, and free cryptocurrency instruments, all designed to lure unsuspecting customers into downloading and executing dangerous code.
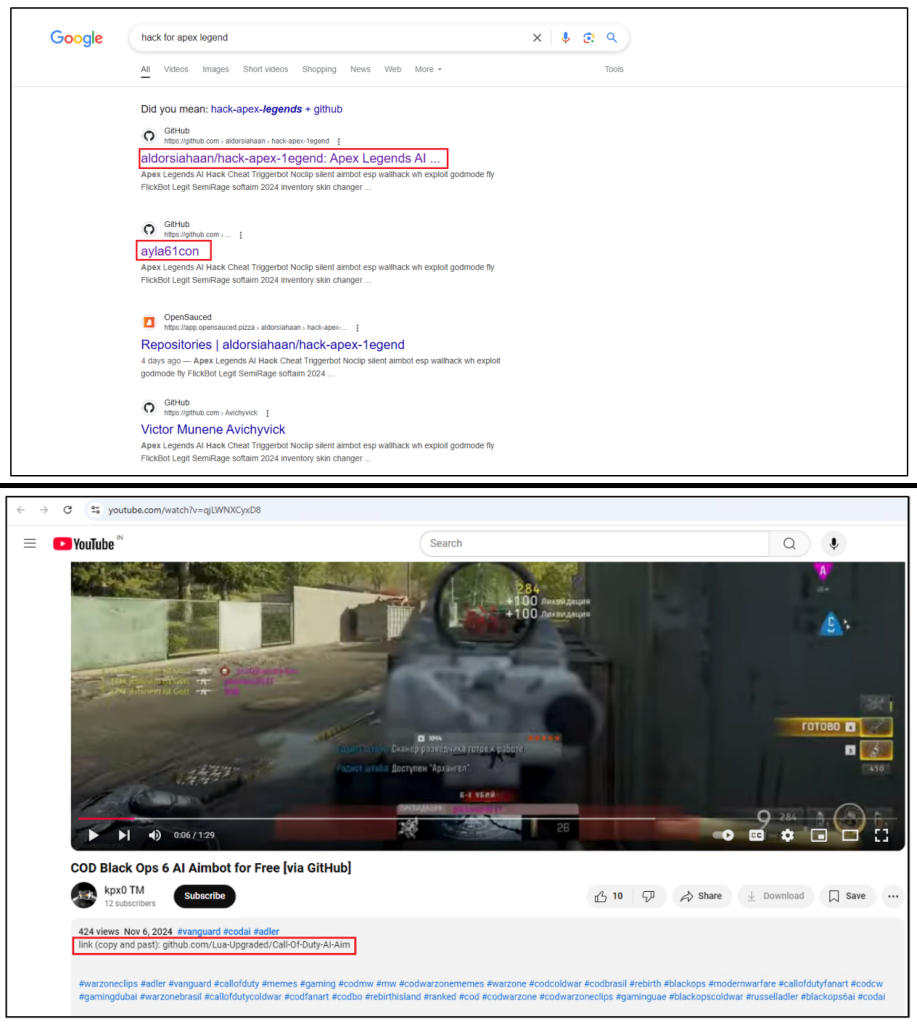
These repositories, typically disguised with professional-looking options like distribution licenses and screenshots, leverage the belief and accessibility of GitHub to deceive customers. Attackers strategically goal people searching for an edge in well-liked video games like Minecraft, Roblox, and Name of Responsibility, or these searching for free entry to premium software program like Spotify and Adobe Categorical.
The Lumma Stealer is the first kind of malware being distributed by means of these repositories. Guarantees of recreation hacks, cracked software program, or free cryptocurrency instruments lure customers. As soon as on the repository, they’re instructed to obtain and execute a file disguised because the promised software program.
The downloaded file is often a variant of the Lumma Stealer malware, which then collects delicate info, together with login credentials, cryptocurrency pockets info, browser historical past, cookies, and personally identifiable info, and extracts the stolen knowledge to command-and-control servers managed by the attackers.
“Every week, a new set of repositories with a new malware variant is released, as the older repositories are detected and removed by GitHub. These repositories also include distribution licenses and software screenshots to enhance their appearance of legitimacy,” McAfee’s Aayush Tyagi defined in a weblog put up.
To additional lure customers, these repositories typically instruct victims to disable their antivirus software program, claiming it can intervene with the downloaded program. This important step successfully disarms the consumer’s major line of defence, permitting the malware to function undetected and steal delicate info akin to login credentials, cryptocurrency pockets knowledge, and searching historical past.
Youngsters and younger adults, notably avid players, are prime targets for these assaults. The attract of recreation hacks, providing benefits like aimbots and velocity hacks, and that the package deal consists of a complicated Anti-Ban system to stop account suspension, are extremely interesting, making them extra prone to falling sufferer to those misleading techniques.
McAfee’s Response and Suggestions:
McAfee Labs is actively mitigating this risk by blocking malicious URLs, detecting and blocking downloaded malware, and offering complete safety options to guard customers. The corporate recommends enhancing your safety posture, akin to protecting antivirus and anti-malware software program up-to-date and practising cautious on-line behaviour. Common system updates with the most recent safety patches are additionally essential.
RELATED TOPICS
- Faux League of Legends Obtain Adverts Unfold Lumma Stealer
- Banshee Stealer Hits macOS Customers through Faux GitHub Repositories
- Hackers Use Excel Recordsdata to Drop Remcos RAT Variant on Home windows
- Faux OnlyFans Checker Instrument Infects Hackers with Lummac Stealer
- YouTube Channels Hacked, Drop Lumma Stealer through Cracked Software program