Morphisec Menace Labs uncovers refined Lua malware focusing on scholar avid gamers and academic establishments. Find out how these assaults work and keep protected.
The cybersecurity researchers at Morphisec Menace Labs have uncovered and thwarted a number of variants of Lua malware particularly focusing on the academic sector. These assaults exploit the recognition of Lua-based gaming engine dietary supplements, that are broadly utilized by scholar avid gamers. Much more regarding, the malware campaigns have been noticed focusing on unsuspecting customers globally together with throughout North America, South America, Europe, Asia, and Australia.
The malware pressure was first reported in March 2024 (don’t confuse Lua malware with the notorious Luabot DDoS malware recognized in 2016). Over the previous months, the supply strategies of Lua malware have modified to develop into easier, probably to evade detection mechanisms. As an alternative of utilizing compiled Lua bytecode, which might simply increase suspicion, the malware is now steadily delivered by way of obfuscated Lua scripts.
Malicious ZIP Recordsdata
The malware is usually distributed within the type of an installer or a ZIP archive and infrequently disguised as recreation cheats or different gaming-related instruments, making it significantly profitable to college students who’re trying to find methods to reinforce their gaming expertise.
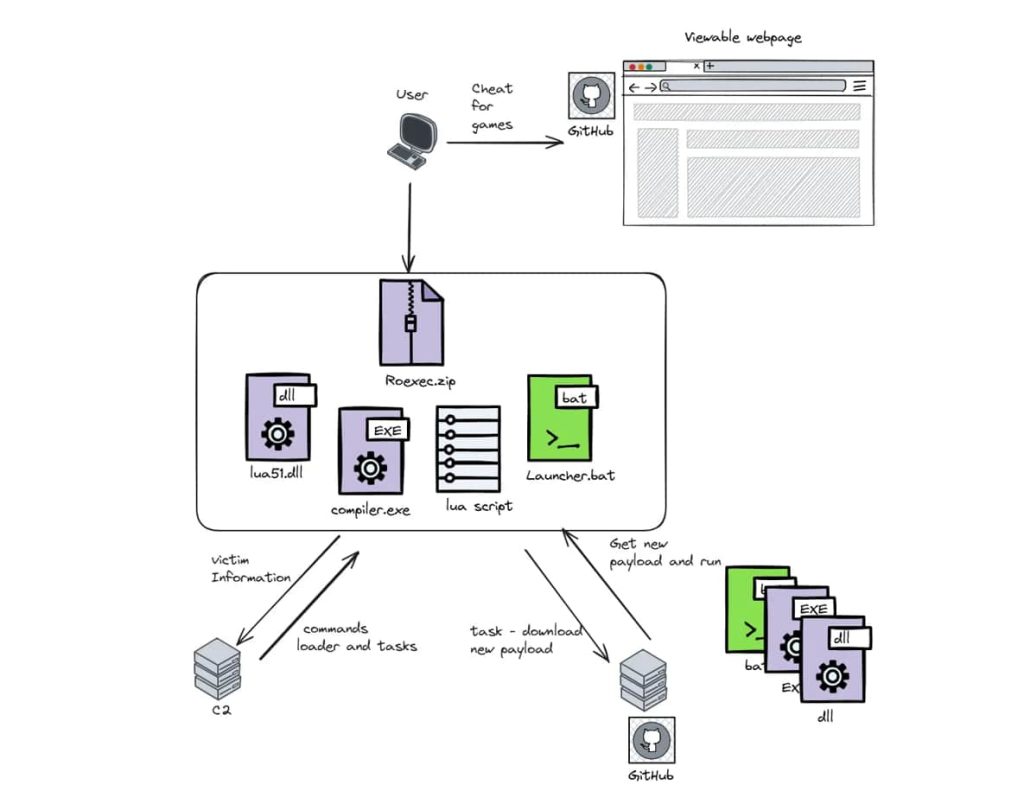
In accordance with Morphisec Menace Labs’ detailed technical weblog submit shared with Hackread.com forward of publishing on Tuesday, when a person downloads the contaminated file, usually from platforms like GitHub, they obtain a ZIP archive containing 4 key elements: Lua51.dll: A runtime interpreter for Lua, Compiler.exe: A light-weight loader, Obfuscated Lua Script: The malicious code and Launcher.bat: A batch file that executes the Lua script.
Upon execution, the batch file runs the Compiler.exe, which hundreds the Lua51.dll and interprets the obfuscated Lua script. This script then establishes communication with a Command and Management (C2) server, sending detailed details about the contaminated machine. The C2 server responds with duties, which may be categorized into two sorts: Lua Loader Duties: Actions akin to sustaining persistence or hiding processes. Activity Payloads: Directions to obtain and configure new payloads.
Lua Malware and search engine marketing Poisoning
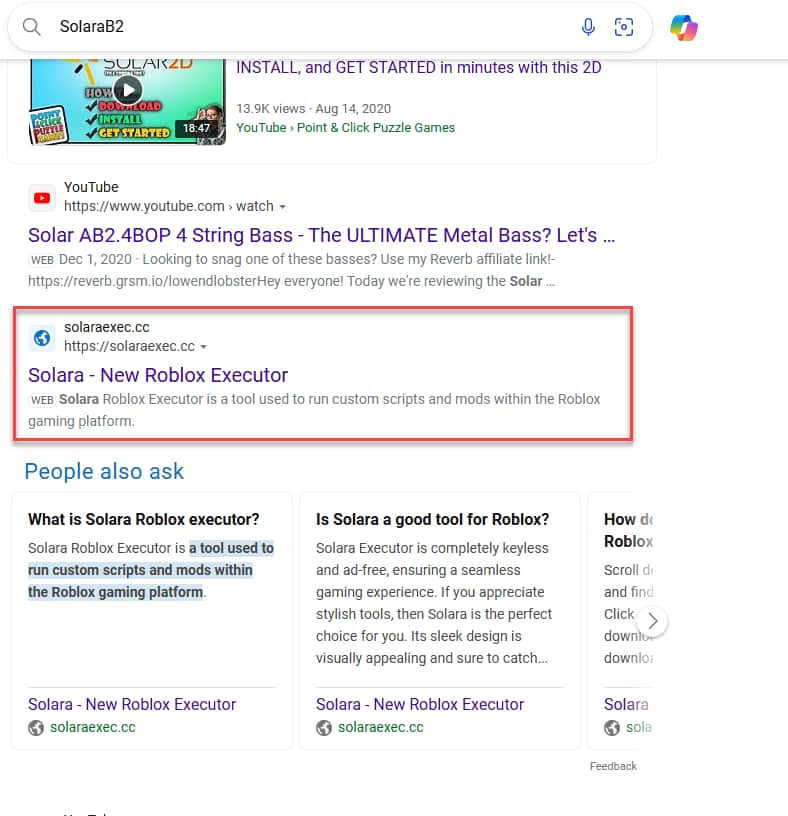
The supply methods utilized in these assaults embrace search engine marketing poisoning, the place search engine outcomes are manipulated to steer customers to malicious web sites. For example, commercials for standard dishonest script engines like Solara and Electron, usually related to Roblox, have been discovered to direct customers to GitHub repositories internet hosting numerous Lua malware variants. These repositories steadily use github.com/user-attachments push requests to distribute the malware.
Further InfoStealer Like Redline
The an infection chain doesn’t finish with Lua malware an infection. The malware in the end results in the deployment of infostealers, notably Redline Infostealers. To your info, infostealers like Redline, Vidar and Formbook are gaining prominence because the harvested credentials are offered on the darkish net particularly ChatGPT credentials, opening the door to extra assaults sooner or later.
Watch Out College students and Avid gamers
Avid gamers, instructional establishments, and college students must be cautious of Lua and different malware threats by avoiding downloads from untrustworthy sources. Protecting safety software program updated and informing customers concerning the cybersecurity dangers of downloading recreation cheats and unverified content material may help scale back the probabilities of these assaults.
RELATED TOPICS
- Pretend League of Legends Obtain Adverts Drop Lumma Stealer
- World malspam targets resorts, spreading Redline, Vidar stealers
- Pretend Home windows website dropped Redline malware as Home windows 11 improve
- Pretend CAPTCHA Verification Pages Spreading Lumma Stealer Malware
- Ransomware Hidden as a Sport: Kransom’s Assault By way of DLL Facet-Loading