Organizations seeking to undertake or enhance an AppSec program typically encounter challenges when attempting to harmonize amongst varied safety scans and instruments. And amassing, collating, and filtering safety scan information is barely half the battle—we additionally must empower growth and DevOps groups to take motion to mitigate discovered vulnerabilities and dangers as a way to develop an efficient safety technique.
Typically, info safety and growth groups have differing aims; InfoSec groups intention to implement safety controls to reduce threat as a lot as potential, whereas dev groups attempt to deal with safety necessities with the bottom impression and energy with out jeopardizing software stability or new options. And until vulnerabilities are recognized early within the growth course of, implementing needed safety controls can lead to important delays, irritating each groups within the course of.
With Checkmarx One™, organizations can cut back friction amongst AppSec and growth groups by simplifying, optimizing, and expediting the identification and remediation of safety vulnerabilities, all inside a single software earlier within the software program growth course of.
Checkmarx One contains a number of scan engines, together with (Static Software Safety Testing (SAST), Software program Composition Evaluation (SCA), and Infrastructure-as-Code (IaC) safety, all on a single platform with easy-to-read, correlated scan experiences.
SCA Information Middle
Checkmarx One SCA engine indexes and analyzes software program parts sure to the scanned software via imported packages and/or dependencies. Third-party software program can introduce further sudden vulnerabilities in an software and our SCA scan engine will help builders and data safety groups perceive and remediate these vulnerabilities.
When an software is scanned, Checkmarx One SCA identifies packages concerned within the dependency tree of the applying, along with Provide Chain Safety (SCS) dangers, licensing info, recognized vulnerabilities, and packages linked to software program containers.
The principle outcome for a given package deal, discovered throughout a Checkmarx One SCA engine’s scan, permits the consumer to gather all of the related information to triage the discovering and rework this info right into a remediation motion:
Checkmarx SCA suggests the latest model of the part, based mostly on all the data collected in the course of the scan and the historical past of releases of a given package deal, when it comes to safety fixes and updates.
Upgrading to the newest model of a part would wish a correct analysis of impacts not solely on software safety, but in addition the useful capabilities inside the software; thus, the method of resolution could trigger friction amongst Improvement and InfoSec groups.
As on this instance, upgrading a part three main variations forward could disrupt options, end in incompatibilities, or require further growth effort.
Often, an software safety program is customized to the chance of the applying that wants mitigation, and there are some alternatives for negotiation to stability the wants of InfoSec with these of Builders: mitigate dangers as a lot as potential, with out breaking any current software performance.
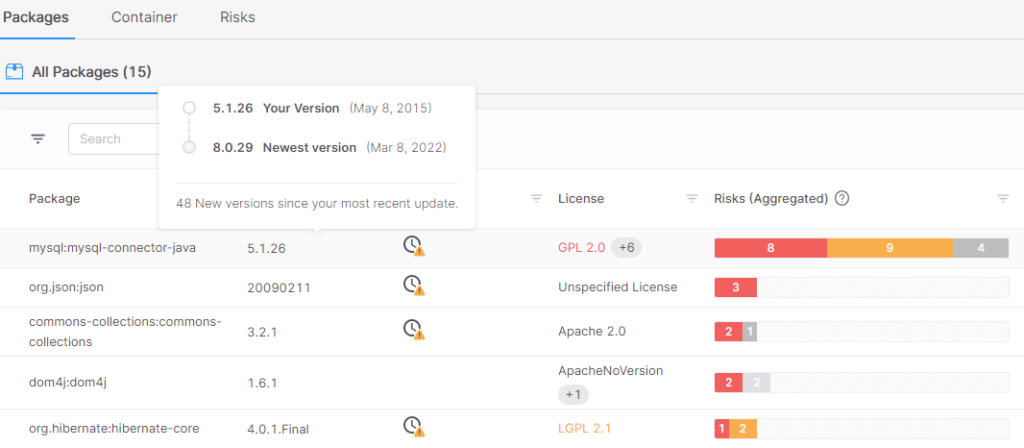
Checkmarx’s AppSec Information Middle assists on this purpose by figuring out and illustrating the historical past of releases of a given package deal, to assist in that negotiation:
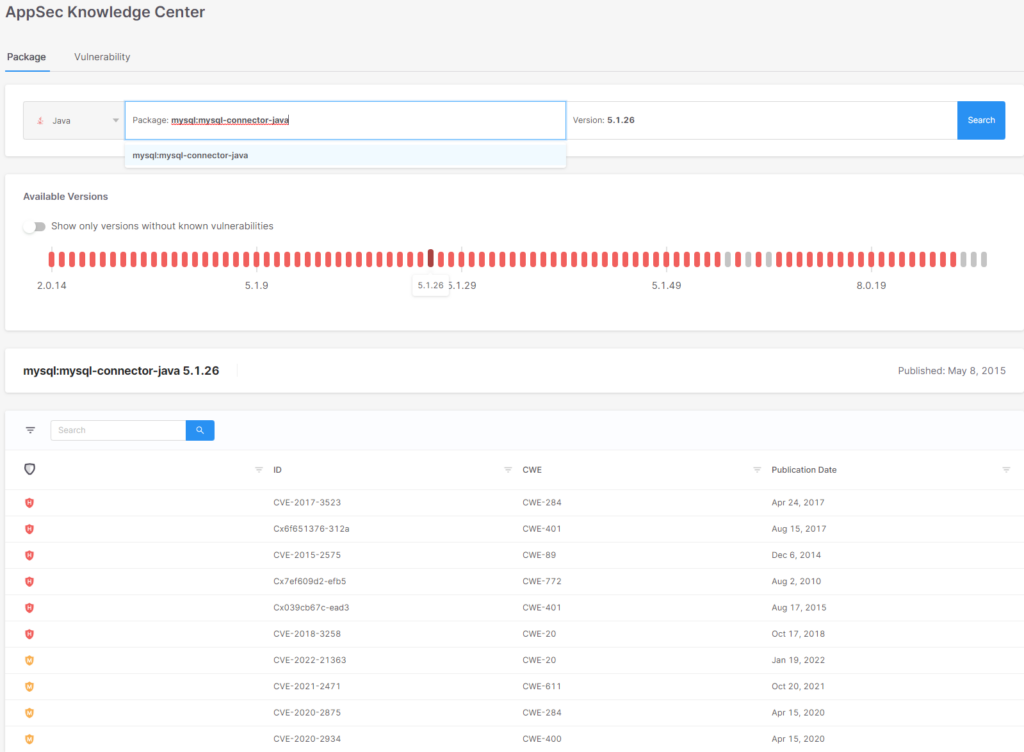
By searching the change record, the consumer can determine essentially the most appropriate improve, permitting organizations to decrease threat whereas minimizing impression.
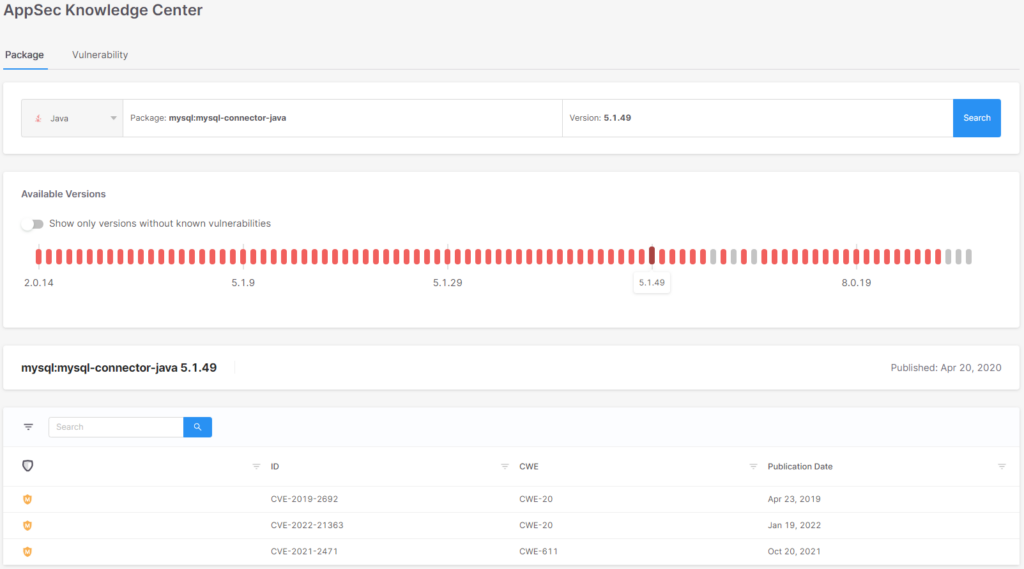
Within the instance above, there’s a model of the mysql-connector-java package deal (5.1.49) which is appropriate for decreasing the chance from Excessive to Medium whereas not altering the most important model of the package deal:
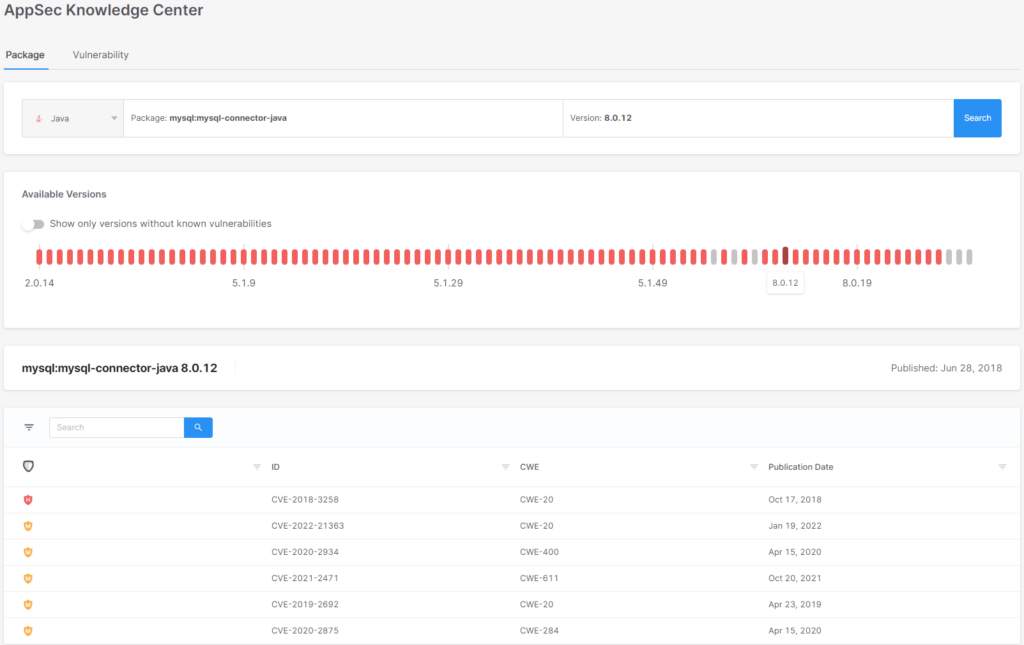
As a aspect notice, the model slider can even assist determine much less efficient upgrades; for instance, the next main model is just not at all times essentially the most appropriate alternative (model 8.0.12 nonetheless has excessive vulnerabilities):
With the help of Checkmarx One’s SCA know-how, InfoSec groups and Builders can implement a prioritized remediation program addressing even essentially the most complicate dependency construction, with the chance of drilling down every particular dependency and model improve advice.
Managing a number of vulnerabilities
Checkmarx One provides a number of engines, together with Software program Part Evaluation, API Safety, IaC Safety, and the well-known SAST engine.
Checkmarx One SAST has the duty of executing the supply code evaluation for an software, supporting numerous programming languages and frameworks.
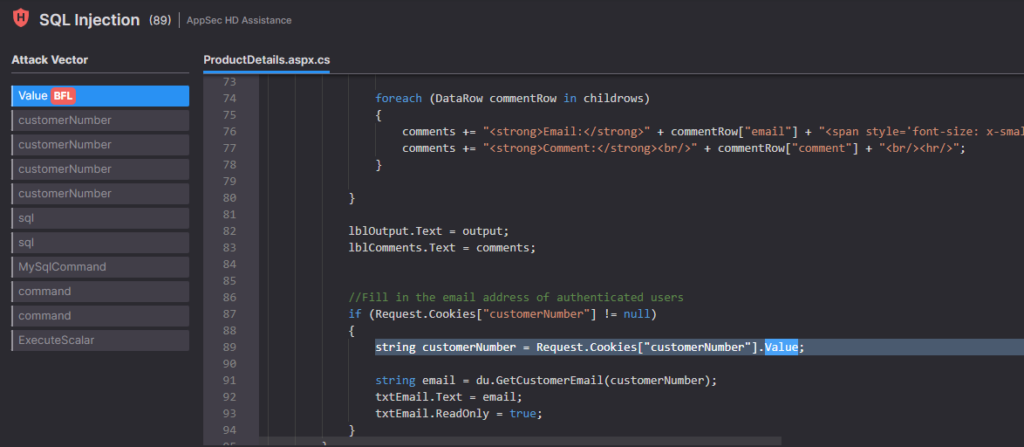
Usually, safety vulnerabilities are detected utilizing particular patterns and the proof of every result’s proven via an assault vector or a knowledge stream.
For instance, injection vulnerabilities (resembling XSS, SQL Injection) are demonstrated if a dataflow is detected from an untrusted supply of information (e.g., user-controllable enter), generally known as a supply, and a sink, which is a location within the code the place the untrusted information “flows” to a vacation spot level of impression (e.g., a Database operation, an HTML response), and not using a sanitizer (e.g., parametric queries, correct encoding).
Because of the nature of purposes and their modularity, typically a number of assault vectors have information flows in frequent: the identical user-controllable supply may affect a number of sinks, or a single sink is the vacation spot of a number of user-controllable sources.
Checkmarx One is commonly capable of determine the Greatest Repair Location (BFL) and might spotlight the particular line quantity inside the particular file the place the vulnerability will be addressed, saving each InfoSec groups and builders effort and time.
To assist prioritize findings for each InfoSec and growth groups, a number of filtering methods will be leveraged for Checkmarx One SAST outcomes, permitting groups to use main and secondary groupings.
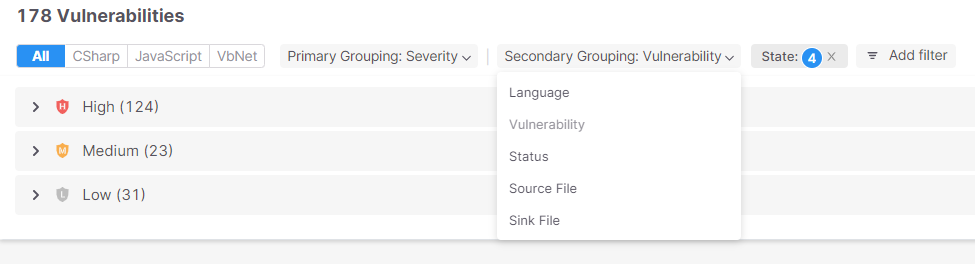
Filters will be utilized by:
- Grouping all of the languages concerned
- Grouping outcomes by severity
- Grouping outcomes by Sink File (vacation spot of assault vectors)
Leveraging filtering, InfoSec and growth groups can determine pertinent safety scan outcomes and correctly prioritize mitigation actions.
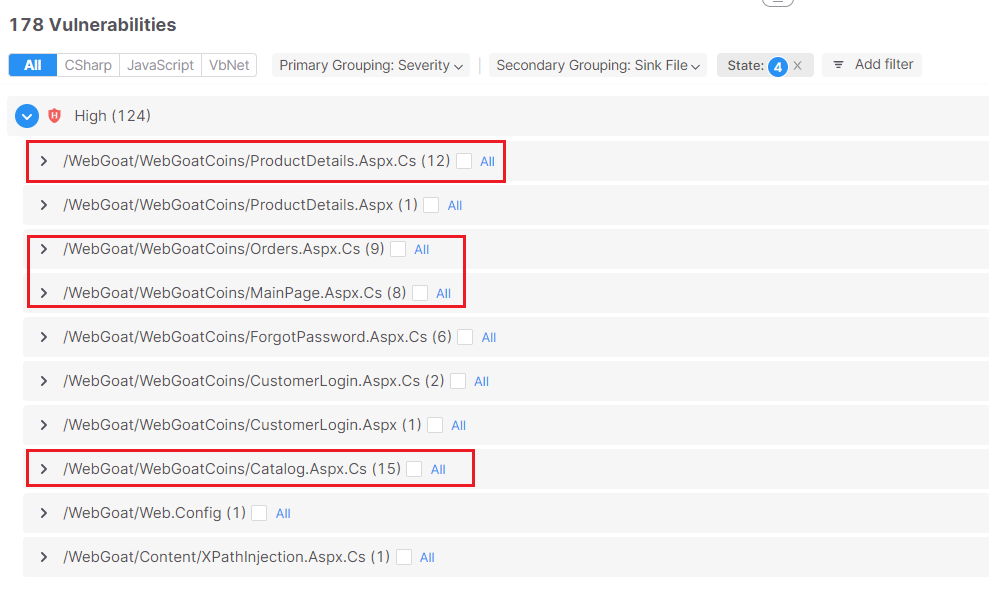
For instance, within the determine beneath, we will see the recordsdata which might be essentially the most impacted by safety vulnerabilities, because the recordsdata symbolize a number of assault vectors colliding in the identical sink: analyzing these recordsdata will assist builders resolve a bigger variety of ends in one single evaluation:
In distinction, we will determine which recordsdata are most uncovered to user-controllable enter by grouping per supply file:
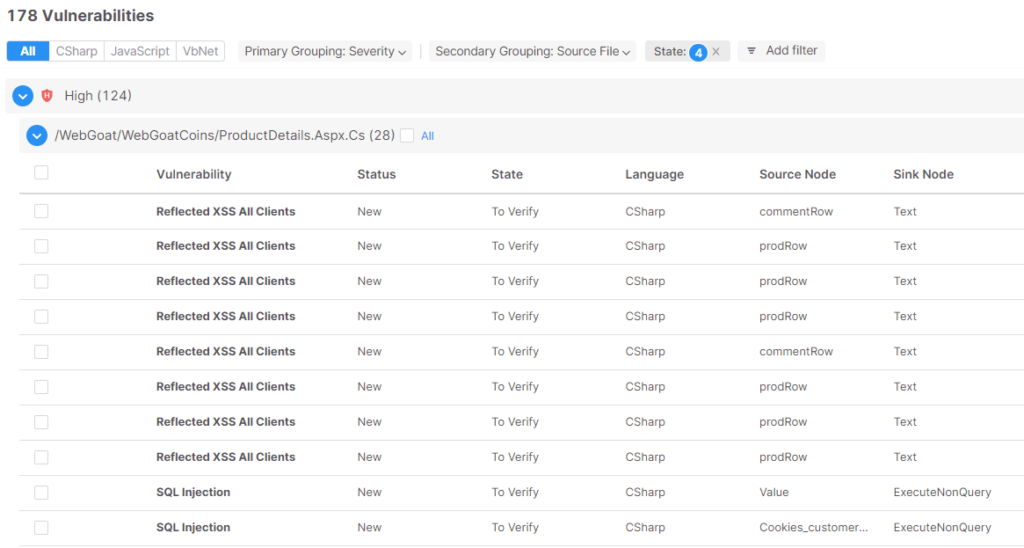
Within the case of a related variety of outcomes, it’s a main precedence for InfoSec groups to decrease the trouble wanted to investigate outcomes. Then again, it’s a main precedence for growth groups to handle essentially the most punctual (and ultimately much less quite a few) areas within the code to use the correct mitigations.
That is the important thing to a profitable AppSec Program.
Evaluating the safety posture
On the whole, purposes are made up of a lot of modules, which can be tied in a single repository or widespread in a number of repositories. Moreover, software modules could also be owned by completely different growth groups.
A company will be very diversified and one of many aims of InfoSec groups is to judge the safety posture of their property from views that may differ a lot from the technical group of modules and repositories, as seen by builders.
Checkmarx One provides the chance to group completely different modules of purposes (or completely different purposes) below the identical entity, to combination outcomes, and to have a notion of the final safety posture of a given group of property.
Each AppSec program has an related threat degree for every asset concerned; due to this fact, this can be very vital to replicate the identical logic on the unified safety software.
Inside Checkmarx One, the consumer can create an software group, which aggregates scans from completely different initiatives, optionally giving grouping standards via tags, and giving a “Criticality Level” to the group itself, as illustrated within the determine beneath:
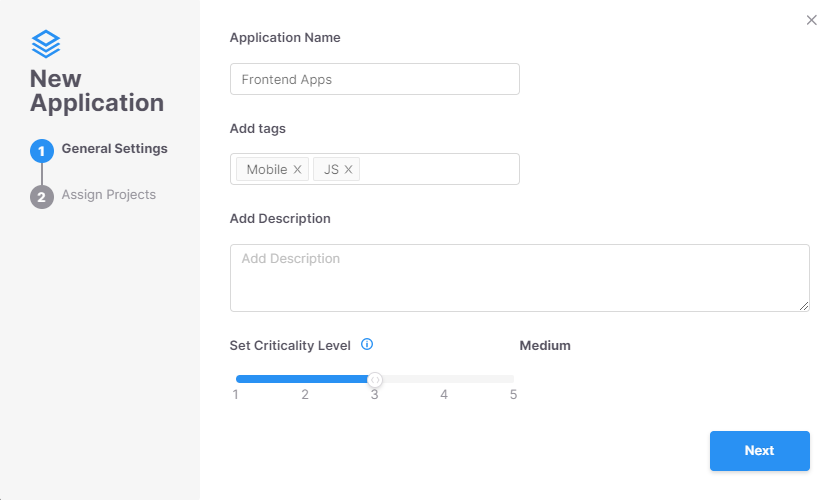
By filtering initiatives by tag, initiatives will be assigned to an software group, robotically.
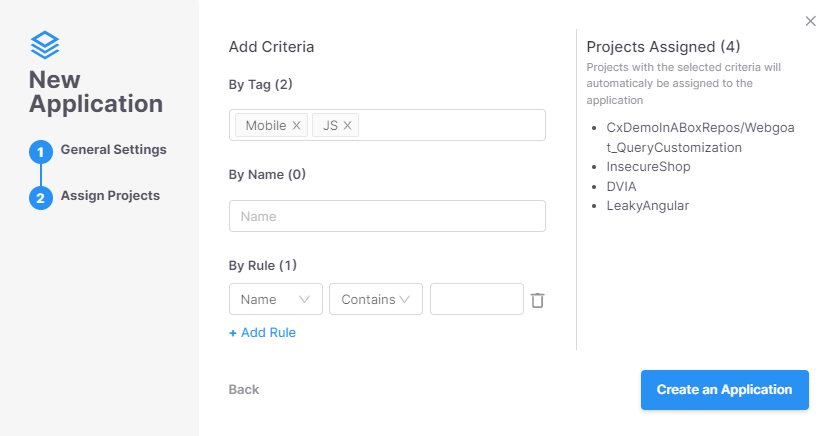
From an inventory of initiatives to application-wise safety posture in only a few clicks!
Scanned initiatives correspond to particular repositories, modules, languages, microservices, or monolithic purposes:
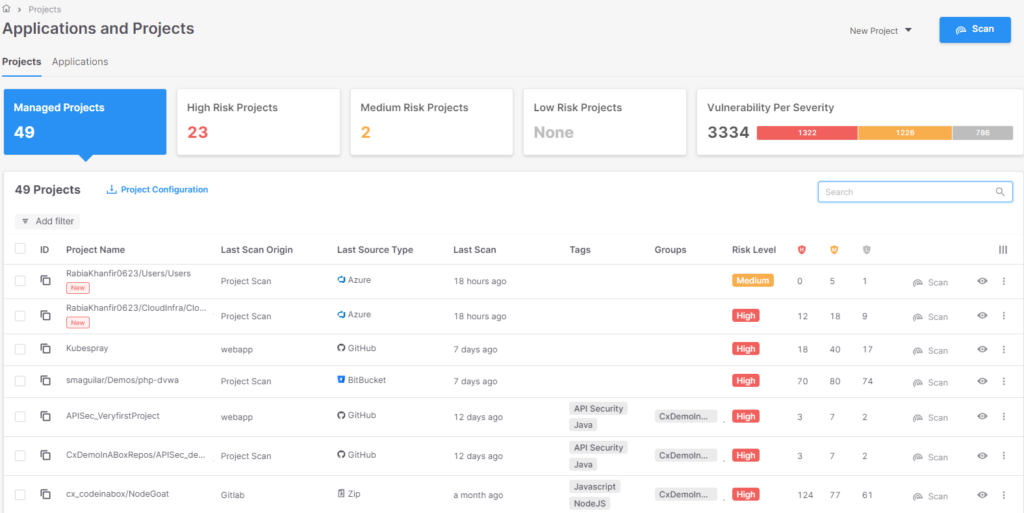
Grouping them by a given standards will present the bigger image of the logical entity “Front End Apps:”
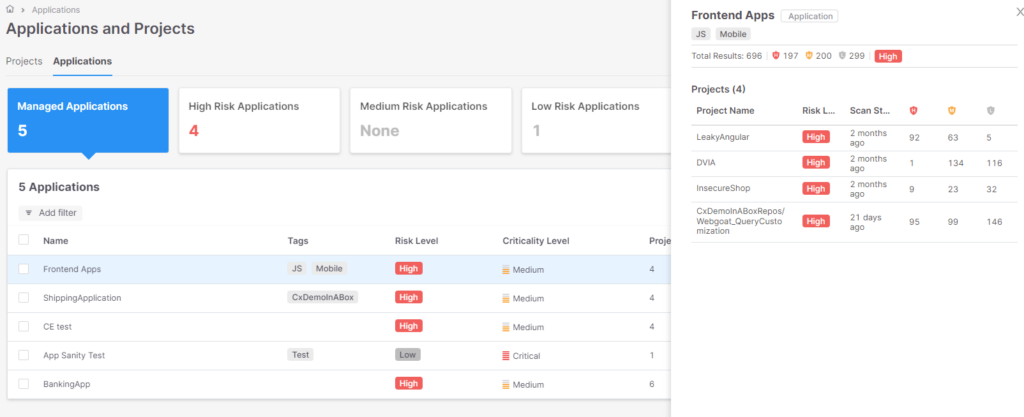
InfoSec workforce can then see the actual safety posture of a gaggle of property:
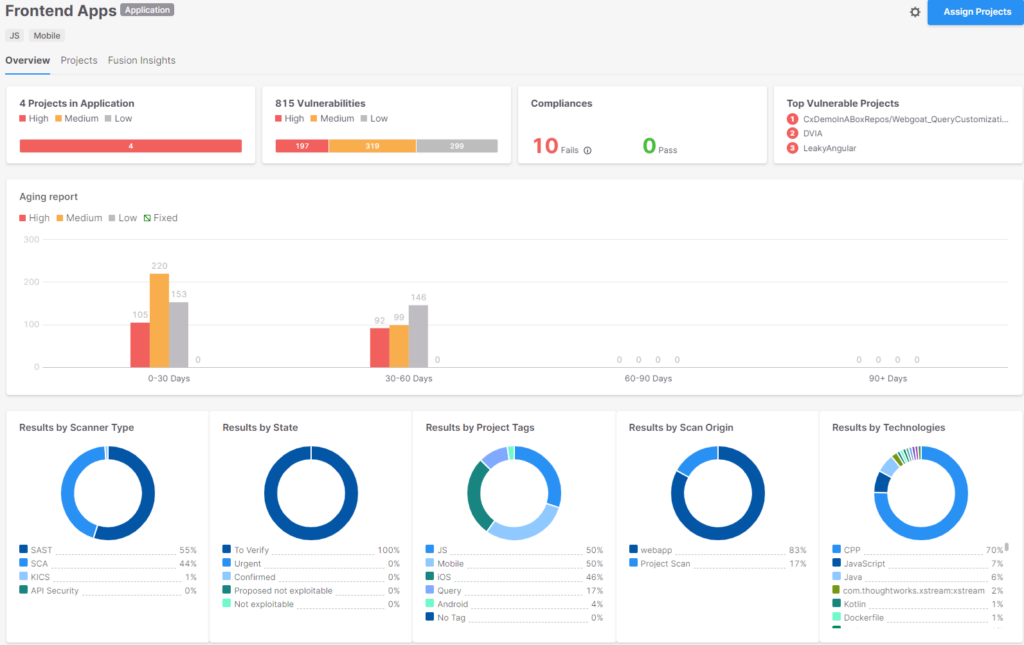
Having the ability to combination outcomes throughout completely different units of findings will assist InfoSec groups consider the general safety posture of a multipart software, drive selections towards extra targeted mitigating actions, and help builders with extra correct employment of their efforts.
Conclusion
Checkmarx One is a strong platform, designed to execute numerous scan operations on purposes in a really brief time-frame. The outcomes will be managed and built-in with a number of issue-tracking environments. And since we combination outcomes from a number of scan engines inside a single platform, we enhance developer productiveness, foster higher collaboration amongst InfoSec and growth groups, and assist organizations enhance their general safety posture via focused steering and prioritization.
Harmonizing the visibility of all of the actors concerned will assist rework outcomes from a safety platform right into a prioritized, possible, correct, and efficient mitigation program.
To see for your self, join a free trial or attain out to a gross sales workforce as we speak!