A safety vulnerability in Ariane Allegro Lodge Examine-In Kiosks uncovered visitor information and doubtlessly compromised room entry. Nonetheless, a patch has been developed and is now obtainable to deal with this challenge, enhancing the safety of the system
Pentagrid, a Swiss cybersecurity agency, lately uncovered a vulnerability in Ariane Allegro State of affairs Participant, a extensively used software program program in resort check-in kiosks. The vulnerability may enable somebody to exit the kiosk’s meant use (kiosk mode) and entry the underlying Home windows Desktop OS.
The software program vendor, Ariane Techniques, is a world chief in self-check-in and out options, serving 3,000 inns and 500,000 rooms in over 25 international locations.
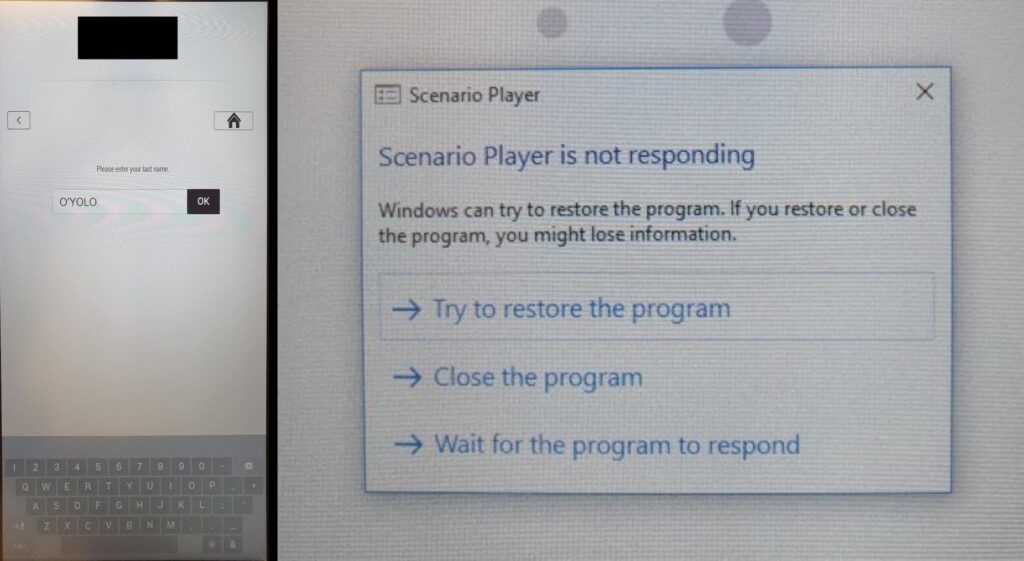
Throughout a risk modelling workshop at a hospitality model in Liechtenstein and Switzerland, Pentagrid’s Martin Schobert revealed that the app crashed in Kiosk mode after getting into a single quote character into the visitor search.
The resort model makes use of this check-in terminal, doubtless a sort Ariane Duo 6000 collection, for smaller areas to facilitate room reserving/check-in, provoke cost through a POS terminal, provision RFID transponders to open the booked resort room, and print invoices.
Schobert discovered that company/customers must seek for room reservations by getting into reserving code or surname. If the title accommodates a single-quote, reminiscent of “O’YOLO,” the applying hangs, the Home windows OS prompts the consumer to attend or cease the duty, and choosing cease terminates the kiosk mode utility.
When stopped, the Home windows OS turns into accessible, which can have antagonistic penalties. reminiscent of permitting resort community assaults, entry to information saved on the terminal, together with PII, reservations, and invoices, and RFID transponder permitting room keys to be created for different rooms. Nonetheless, to use the flaw, the consumer will need to have bodily entry to the system, and the terminal should be in a self-service state, which inns usually allow throughout particular instances.
A CVE for the vulnerability is but to be assigned whereas Kiosk Mode Bypass severity has been given as 6.3 (Medium). The vulnerability, found in March 2024, was promptly communicated to the seller.
Ariane Techniques clarified that these are “legacy systems,” through which the USB ports are disabled and “no PII or exploitable data can be retrieved from the kiosk.” Furthermore, it believed the resort should be utilizing an outdated model of the software program. Nonetheless, Pentagrid asserted that the system’s design lets “the kiosk produces and keeps accessible invoice files.”
Nonetheless, Ariane Techniques confirmed the problem has been mounted. Nonetheless, the precise model fixing the problem isn’t publicly recognized. Hackread suggests contacting the seller straight for clarification and putting in the most recent model instantly to remain protected.
John Bambenek, President of Cybersecurity and Menace Intelligence Consulting agency Bambenek Consulting commented on the problem emphasising the risks of the potential entry to victims’ rooms in home violence circumstances, theft of bank card information attributable to terminals doubling as POS units.
“The most important danger entails numerous home violence and stalking eventualities the place undesirable company may get keys to open a sufferer’s room. As these units are additionally used as POS terminals to facilitate funds of resort rooms, presumably the largest danger there’s stolen bank card info.“
“The underlying issue seems to be that the specific terminals at this specific location had the vulnerability (albeit, a very simple one to find) and later versions did not. Kiosks tend to be “set and forget” units which implies operators could not know they have to be up to date on a routine foundation…or if they’re up to date in any respect,“ he added.
“These units in all probability can’t be fully remoted from the principle resort community as a part of the purpose is to challenge keys and deal with room administration, nonetheless, the units needs to be restricted to sending solely required machines and ports with every little thing else filtered,“ Bambenek suggested.