The NCA, FBI, and Europol have revived a seized LockBit ransomware information leak web site to trace at new data being revealed by legislation enforcement this Tuesday.
On February 19, a legislation enforcement operation known as Operation Cronos took down LockBit’s infrastructure, together with 34 servers internet hosting the info leak web site and its mirrors, information stolen from the victims, cryptocurrency addresses, 1,000 decryption keys, and the affiliate panel.
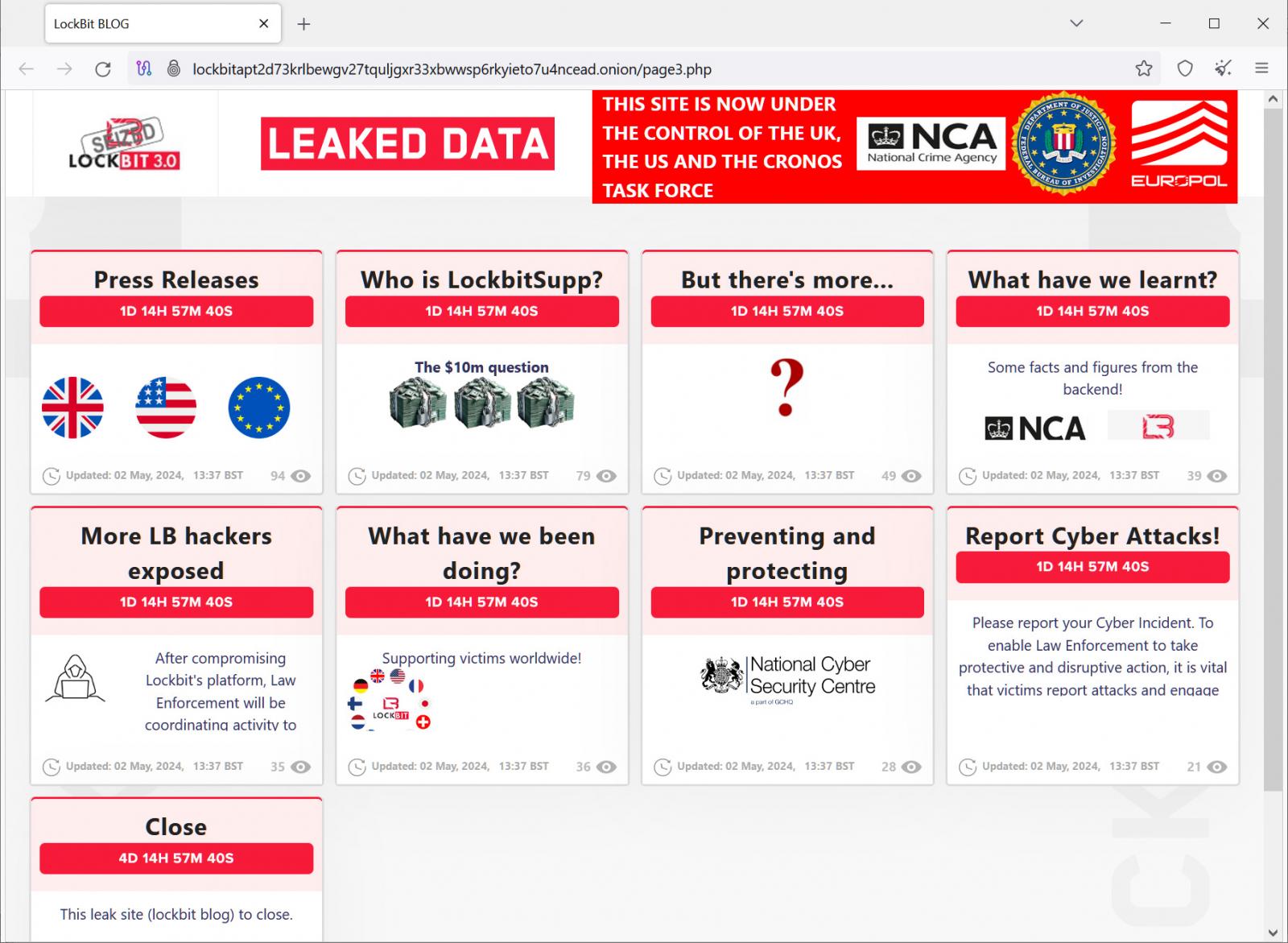
As a part of this disruption, the police transformed one of many information leak websites right into a press launch web site, the place the UK’s Nationwide Crime Company (NCA), the FBI, and Europol shared details about what they discovered in the course of the operation, a listing of associates, and the way LockBit lies to victims by not at all times deleting stolen information after a ransom is paid.
One of many bulletins had the title “Who is LockBitSupp?” hinting that legislation enforcement would reveal details about who was operating the ransomware operation.
Nonetheless, after days of ready, the weblog publish merely acknowledged, “We know who he is. We know where he lives. We know how much he is worth. LockBitSupp has engaged with Law Enforcement :).”
Legislation enforcement finally shut down the web site a number of days later, with many seeing the “LockBitSupp” publish as a blunder by legislation enforcement for hyping the announcement and revealing nothing and a win for LockBitSupp, who continued to stay nameless.
On Sunday, worldwide legislation enforcement revived LockBit’s information leak/press launch web site, this time with seven new weblog posts which might be all going reside on the identical time, on Tuesday at 14:00:00 UTC (10 AM EST).
Supply: BleepingComputer
These weblog posts tease titles like “What have we learnt?,” “More LB hackers exposed,” “What have we been doing?,” and what many hope to be the coup de grâce on the diminished ransomware operation, one other weblog publish titled “Who is LockBitSupp?”.
For now, we should wait to see if legislation enforcement will really reveal something substantial about LockBit’s operator or if that is as soon as once more going to be a letdown.
Because the legislation enforcement operation, LockBit has been struggling to return to prior exercise ranges, with associates having turn into cautious that the operation is now compromised and being watched too carefully by legislation enforcement.
Nonetheless, that doesn’t imply the ransomware gang is completed, as disruptive assaults proceed and the operation remains to be a danger to the enterprise worldwide.
