A brand new ransomware-as-a-service (RaaS) operation is impersonating the reputable Cicada 3301 group and has already listed 19 victims on its extortion portal, because it shortly attacked corporations worldwide.
The brand new cybercrime operation is known as after and makes use of the identical brand because the mysterious 2012-2014 on-line/real-world recreation named Cicada 3301 that concerned elaborate cryptographic puzzles.
Nonetheless, there is not any connection between the 2, and the reputable venture has issued an announcement to surrender any affiliation with the menace actors and condemned the ransomware operation’s actions.
“We do not know the identity of the criminals behind these heinous crimes, and are not associated with these groups in any way,” reads the assertion from the Cicada 3301 group.
Launched in early June
The Cicada3301 RaaS first started selling the operation and recruiting associates on June 29, 2024, in a discussion board publish to the ransomware and cybercrime discussion board often known as RAMP.
Nonetheless, BleepingComputer is conscious of Cicada assaults as early as June 6, indicating that the gang was working independently earlier than making an attempt to recruit associates.
Supply: Truesec
Like different ransomware operations, Cicada3301 conducts double-extortion techniques the place they breach company networks, steal knowledge, after which encrypt units. The encryption key and threats to leak stolen knowledge are then used as leverage to scare victims into paying a ransom.
The menace actors function a knowledge leak website that’s used as a part of their double-extortion scheme.
Supply: BleepingComputer
An evaluation of the brand new malware by Truesec revealed vital overlaps between Cicada3301 and ALPHV/BlackCat, indicating a doable rebrand or a fork created by former ALPHV’s core group members.
That is based mostly on the truth that:
- Each are written in Rust.
- Each Use the ChaCha20 algorithm for encryption.
- Each make use of an identical VM shutdown and snapshot-wiping instructions.
- Each use the identical person interface command parameters, the identical file naming conference, and the identical ransom notice decryption methodology.
- Each use intermittent encryption on bigger recordsdata.
For context, ALPHV carried out an exit rip-off in early March 2024 involving faux claims about an FBI takedown operation after they stole a large $22 million cost from Change Healthcare from one in every of their associates.
Truesec has additionally discovered indications that the Cicada3301 ransomware operation could accomplice with or make the most of the Brutus botnet for preliminary entry to company networks. That botnet was beforehand related to global-scale VPN brute-forcing actions focusing on Cisco, Fortinet, Palo Alto, and SonicWall home equipment.
It is value noting that the Brutus exercise was first noticed two weeks after ALPHV shut down operations, so the hyperlink between the 2 teams nonetheless stands when it comes to timelines.
Yet one more menace to VMware ESXi
Cicada3301 is a Rust-based ransomware operation with each Home windows and Linux/VMware ESXi encryptors. As a part of Truesec’s report, the researchers analyzed the VMWare ESXi Linux encryptor for the ransomware operation.
Like BlackCat and different ransomware households, equivalent to RansomHub, a particular key should be entered as a command line argument to launch the encryptor. This key’s used to decrypt an encrypted JSON blob that comprises the configuration that the encryptor will use when encrypting a tool.
Truesec says that the encryptor checks for the validity of the important thing by utilizing it to decrypt the ransom notice and, if profitable, continues with the remainder of the encryption operation.
Its fundamental perform (linux_enc) makes use of the ChaCha20 stream cipher for file encryption after which encrypts the symmetric key used within the course of with an RSA key. The encryption keys are generated randomly utilizing the ‘OsRng’ perform.
Cicada3301 targets particular file extensions matching paperwork and media recordsdata and checks their measurement to find out the place to use intermittent encryption (>100MB) and the place to encrypt all the file contents (<100MB).
When encrypting recordsdata, the encryptor will append a random seven-character extension to the file title and create ransom notes named ‘RECOVER-[extension]-DATA.txt,’ as proven under. It ought to be famous that BlackCat/ALPHV encryptors additionally used random seven-character extensions and a ransom notice named ‘RECOVER-[extension]-FILES.txt.’
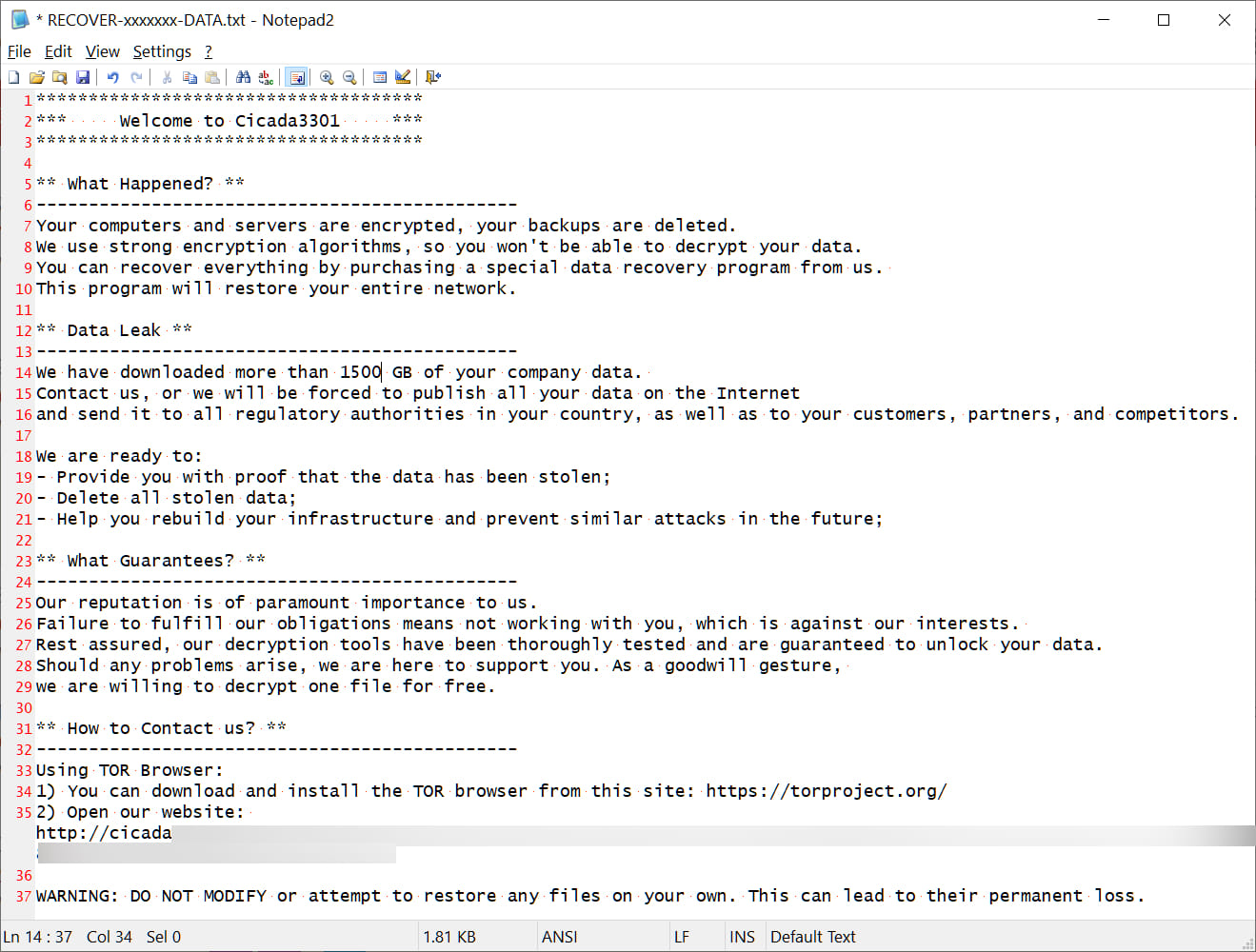
Supply: BleepingComputer
The ransomware’s operators can set a sleep parameter to delay the encryptor’s execution, doubtlessly to evade quick detection.
A “no_vm_ss” parameter additionally orders the malware to encrypt VMware ESXi digital machines with out making an attempt to close them down first.
Nonetheless, by default, Cicada3301 first makes use of ESXi’s ‘esxcli’ and ‘vim-cmd’ instructions to close down digital machines and delete their snapshots earlier than encrypting knowledge.
esxcli –formatter=csv –format-param=fields==”WorldID,DisplayName” vm course of checklist | grep -viE ”,(),” | awk -F ””*,”*” '{system(”esxcli vm course of kill –sort=drive –world-id=”$1)}’ > /dev/null 2>&1;
for i in `vim-cmd vmsvc/getallvms| awk '{print$1}’`;do vim-cmd vmsvc/snapshot.removeall $i & achieved > /dev/null 2>&1
Cicada3301’s actions and charge of success point out an skilled actor who is aware of what they’re doing, additional supporting the speculation of an ALPHV reboot or at the least using associates with prior ransomware expertise.
The brand new ransomware’s give attention to ESXi environments highlights its strategic design to maximise harm in enterprise environments that many menace actors now goal for profitable income.
By combining file encryption with the flexibility to disrupt VM operations and take away restoration choices, Cicada3301 ensures a high-impact assault that impacts complete networks and infrastructures, maximizing the strain positioned on victims.
