Group-IB has uncovered Lazarus group’s stealthy new trojan and strategy of hiding malicious code in prolonged attributes on macOS. Learn the way this superior persistent risk (APT) is evading detection and the steps you possibly can take to guard your self.
Cybersecurity researchers at Group-IB report that the North Korean state-backed APT Lazarus group, is now deploying a brand new macOS trojan known as “RustyAttr.” This malware, together with a brand new evasion approach, lets Lazarus perform its operations whereas remaining undetected.
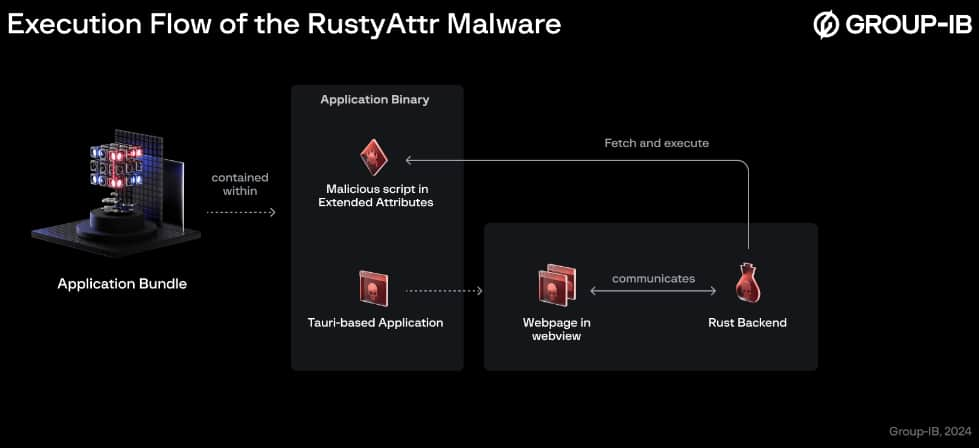
Since Might 2024, the Lazarus Group has been using a way that hides malicious code inside the prolonged attributes (EAs) of recordsdata on macOS programs, using the RustyAttr trojan. Prolonged attributes are hidden knowledge containers hooked up to recordsdata, enabling the storage of further data past normal attributes akin to dimension or creation date.
This methodology is especially tough as a result of these attributes are invisible by default in purposes like Finder or Terminal. Nonetheless, utilizing the .xattr command, attackers can simply entry and exploit this hidden knowledge.
In 2020, Bundlore adware used the same approach to cover its payload in useful resource forks which saved structured knowledge on older macOS programs, researchers famous within the weblog put up shared with Hackread.com.
The doable assault state of affairs includes a legitimate-looking malicious software, constructed utilizing the Tauri framework. It shows faux PDF recordsdata associated to job alternatives or cryptocurrency, a theme according to Lazarus.
In your data, the Tauri framework is a web-based software for creating light-weight desktop purposes, enabling builders to make use of HTML, CSS, JavaScript, and Rust for entrance and backend, respectively, to execute malicious scripts.
The shell scripts reveal two forms of decoys: one fetches a PDF file from a file internet hosting service, containing questions associated to recreation venture growth and funding, and the opposite shows a dialogue stating that the app doesn’t help the required model, whereas an online request to the staging server processes within the background. The malicious script is hidden inside a customized prolonged attribute named “test”.
The appliance leverages a JavaScript file named “preload.js” to work together with the hidden script. This JavaScript code, utilizing Tauri’s functionalities, retrieves the script from the prolonged attribute and executes it.
“Interestingly, the next behaviour is as follows – if the attribute exists, no user interface will be shown whereas, if the attribute is absent, the fake webpage will be shown,” the researchers revealed.
The malicious elements are hidden inside the prolonged attributes, making them invisible to antivirus scanners. The purposes had been initially signed with a leaked certificates (revoked by Apple now) however remained unnotarized, bypassing one other layer of doable detection.
Whereas the researchers haven’t recognized any confirmed victims but, they consider Lazarus could be experimenting with this system for future assaults. This discovery is essential as a result of it’s a very new tactic, not but documented within the MITRE ATT&CK framework, a normal reference for assault methods.
The Lazarus group’s sophistication and steady enlargement of techniques present their efforts to evade detection and compromise programs. To remain protected, confirm the supply and legitimacy of recordsdata earlier than downloading or executing them, and keep away from downloading innocent content material like PDFs with out checking even when it seems reliable.
Hold macOS Gatekeeper on because it prevents the execution of untrusted purposes. Lastly, make the most of superior risk intelligence options to stay conscious of rising threats and develop efficient safety methods.