North Korean hackers from Lazarus Group exploited a zero-day vulnerability in Google Chrome to focus on cryptocurrency buyers with a misleading and pretend NFT sport. The attackers use social engineering and malicious software program to steal delicate information and doubtlessly deploy additional malware.
The notorious North Korean hacking group, Lazarus Group, has launched a classy assault marketing campaign concentrating on cryptocurrency buyers. This marketing campaign, uncovered by Kaspersky researchers, entails a multi-layered assault chain that leverages social engineering, a pretend sport web site, and a zero-day exploit in Google Chrome.
In keeping with the report, Kaspersky Complete Safety found a brand new assault chain in Could 2024 concentrating on an unnamed Russian nationwide’s private laptop utilizing the Manuscrypt backdoor.
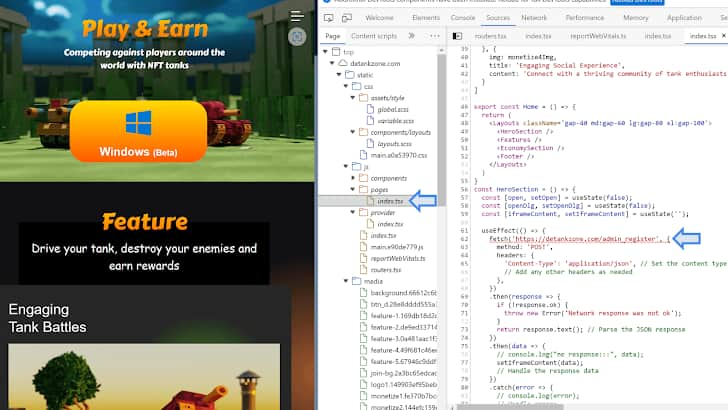
Kaspersky researchers Boris Larin and Vasily Berdnikov estimate that the marketing campaign began in February 2024. Delving deeper into the assault researchers discovered that the attackers have created a web site known as “detankzonecom” that seems to be a respectable platform for a “DeFiTankZone” sport.
This sport supposedly combines Decentralized Finance (DeFi) components with Non-Fungible Tokens (NFTs) inside a Multiplayer On-line Battle Enviornment (MOBA) setting. The web site even contains a downloadable trial model, additional enhancing the phantasm of legitimacy. Nonetheless, beneath the floor lies a malicious lure.
“Under the hood, this website had a hidden script that ran in the user’s Google Chrome browser, launching a zero-day exploit and giving the attackers complete control over the victim’s PC,” researchers wrote.
The exploit comprises code for 2 vulnerabilities: one permitting attackers to entry your complete tackle area of the Chrome course of from JavaScript (CVE-2024-4947) and the second permits bypassing the V8 sandbox to entry reminiscence exterior the bounds of the register array. Google patched CVE-2024-4947, a sort confusion bug within the V8 JavaScript and WebAssembly engine, in March 2024, nevertheless it’s unclear if the attackers found it earlier and weaponized it as a zero-day or exploited it as an N-day vulnerability.
An n-day vulnerability refers to a safety flaw or weak point that has already been found, publicly disclosed, and usually patched or mitigated by the software program vendor. The time period “n-day” signifies that the vulnerability has been recognized for “n” days, the place n represents the variety of days because the vulnerability was first disclosed or patched.
Following profitable exploitation, the attackers deploy a customized script (validator) to assemble system data and decide if the contaminated machine holds any helpful belongings price additional exploitation. The precise payload delivered after this stage stays unknown.
On this marketing campaign, Lazarus has focused influential figures within the cryptocurrency area, leveraging social media platforms like X (previously Twitter) and LinkedIn. They established a social media presence with a number of accounts on X, actively selling the pretend sport, and employed generative AI and graphic designers to create high-quality promotional content material for the DeTankZone sport. Moreover, the group despatched specifically crafted emails to people of curiosity, posing as blockchain corporations or sport builders searching for funding alternatives.
The DeTankZone web site itself seems to be constructed upon the stolen supply code of a respectable blockchain sport known as DeFiTankLand (DFTL). This sport skilled a safety breach in March 2024, resulting in the theft of $20,000 price of cryptocurrency.
Whereas the builders suspected an insider, Kaspersky researchers consider Lazarus Group may be liable for each the theft and the repurposing of the stolen supply code for his or her malicious marketing campaign.
This marketing campaign highlights the evolving techniques of the Lazarus Group. It’s essential to be cautious of unsolicited funding alternatives, particularly these involving downloadable sport shoppers or suspicious social media promotions. Moreover, holding browser software program like Chrome up to date with the newest safety patches is crucial to mitigate the threat of zero-day exploits.
RELATED TOPICS
- How Unhealthy is the North Korean Cyber Menace?
- Feds Bust N. Korean Identification Theft Ring Focusing on US Companies
- North Korean Hackers Deploy Linux FASTCash ATM Malware
- Pretend North Korean IT Staff Infiltrate Companies, Demand Ransom
- Nexera DeFi Protocol Hacked: $1.8M Stolen in Good Contract Exploit