Over 22,000 CyberPanel cases uncovered on-line to a vital distant code execution (RCE) vulnerability have been mass-targeted in a PSAUX ransomware assault that took nearly all cases offline.
This week, safety researcher DreyAnd disclosed that CyberPanel 2.3.6 (and sure 2.3.7) suffers from three distinct safety issues that can lead to an exploit permitting unauthenticated distant root entry with out authentication.
Particularly, the researcher uncovered the next issues on CyberPanel model 2.3.6:
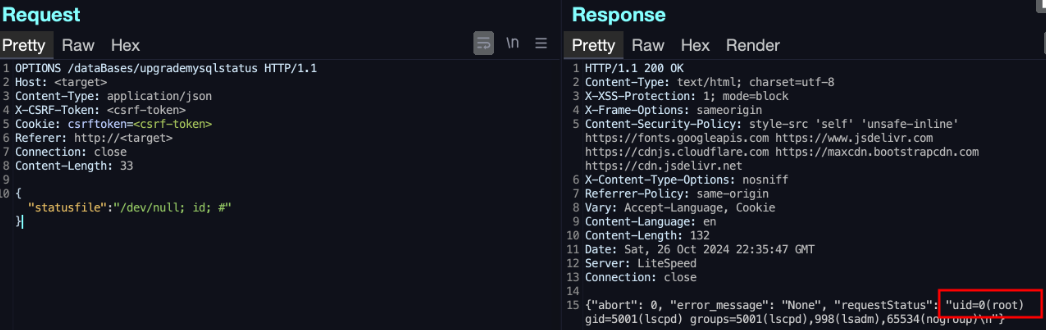
- Faulty authentication: CyberPanel checks for consumer authentication (login) on every web page individually as a substitute of utilizing a central system, leaving sure pages or routes, like ‘upgrademysqlstatus,’ unprotected from unauthorized entry.
- Command injection: Person inputs on unprotected pages aren’t correctly sanitized, enabling attackers to inject and execute arbitrary system instructions.
- Safety filter bypass: The safety middleware solely filters POST requests, permitting attackers to bypass it utilizing different HTTP strategies, like OPTIONS or PUT.
Supply: DreyAnd
The researcher, DreyAnd, developed a proof-of-concept exploit to show root-level distant command execution on the server, permitting him to take full management of the server.
DreyAnd advised BleepingComputer that he may solely take a look at the exploit on model 2.3.6 as he didn’t have entry to the two.3.7 model on the time. Nevertheless, as 2.3.7 was launched on September 19, earlier than the bug was discovered, it was doubtless impacted as nicely.
The researcher mentioned they disclosed the flaw to the CyberPanel builders on October 23, 2024, and a repair for the authentication subject was submitted later that night on GitHub.
Whereas anybody who installs CyberPanel from GitHub or by means of the improve course of will get the safety repair, the builders haven’t launched a brand new model of the software program or issued a CVE.
BleepingComputer has contacted CyberPanel to ask once they plan to launch a brand new model or safety announcement, however we’re nonetheless awaiting their response.
Focused in PSAUX ransomware assault
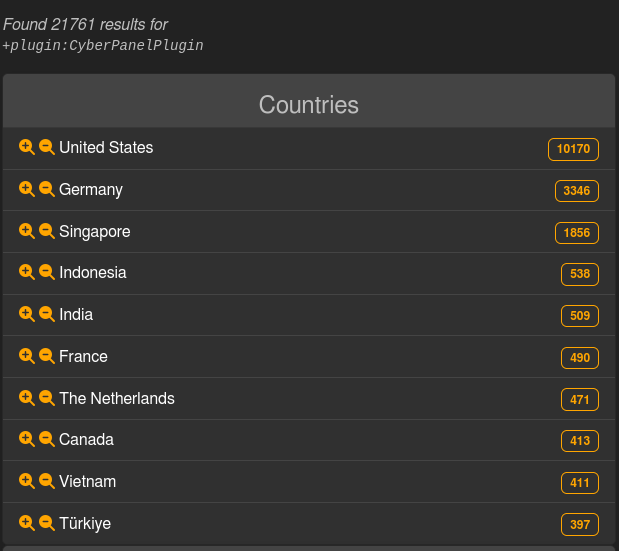
Yesterday, the menace intel search engine LeakIX reported that 21,761 weak CyberPanel cases have been uncovered on-line, and almost half (10,170) have been in america.
Supply: LeakIX | X
Nevertheless, in a single day, the variety of cases mysteriously dropped to solely about 400 cases, with LeakIX telling BleepingComputer the impacted servers are not accessible.
Cybersecurity researcher Gi7w0rm tweeted on X that these cases managed over 152,000 domains and databases, for which CyberPanel acted because the central entry and administration system.
LeakIX has now advised BleepingComputer that menace actors mass-exploited the uncovered CyberPanel servers to put in the PSAUX ransomware.
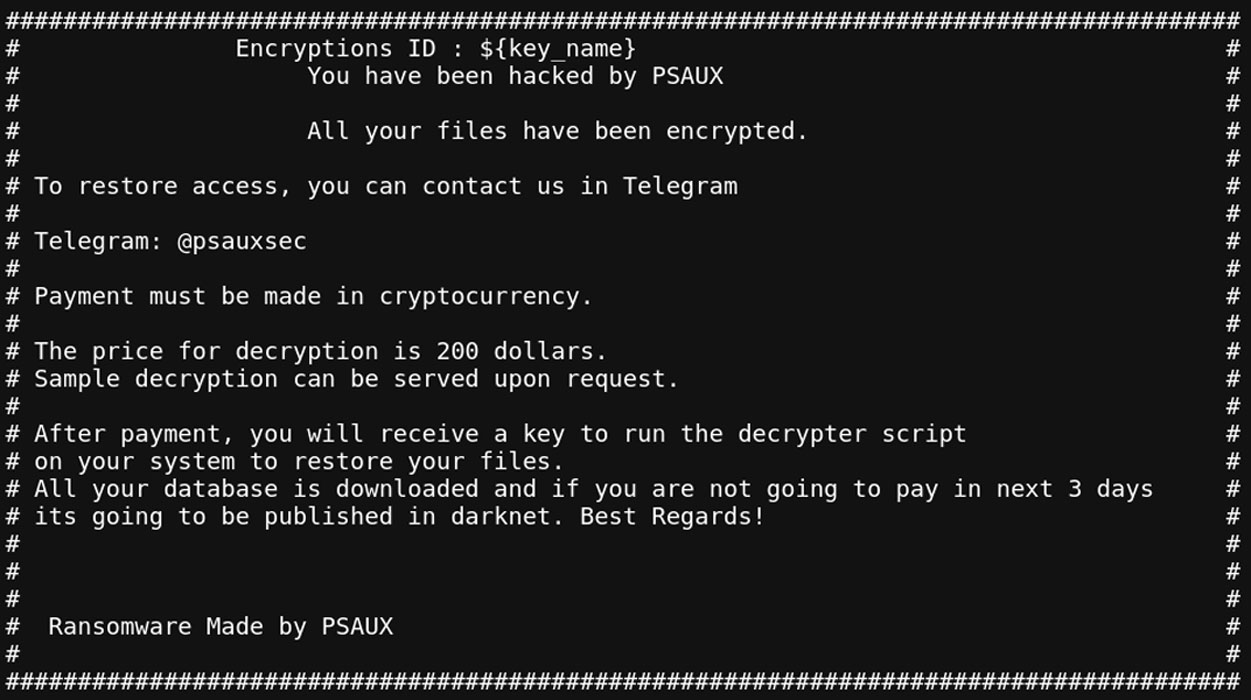
The PSAUX ransomware operation has been round since June 2024 and targets uncovered internet servers by means of vulnerabilities and misconfigurations.
Supply: LeakIX
When launched on a server, the ransomware will create a singular AES key and IV and use them to encrypt the information on a server.
The ransomware can even create ransom notes named index.html in each folder and duplicate the ransom notice to /and so on/motd, so it’s proven when a consumer logs into the system.
When completed, the AES key and IV are encrypted utilizing an enclosed RSA key and saved as /var/key.enc and /var/iv.enc.
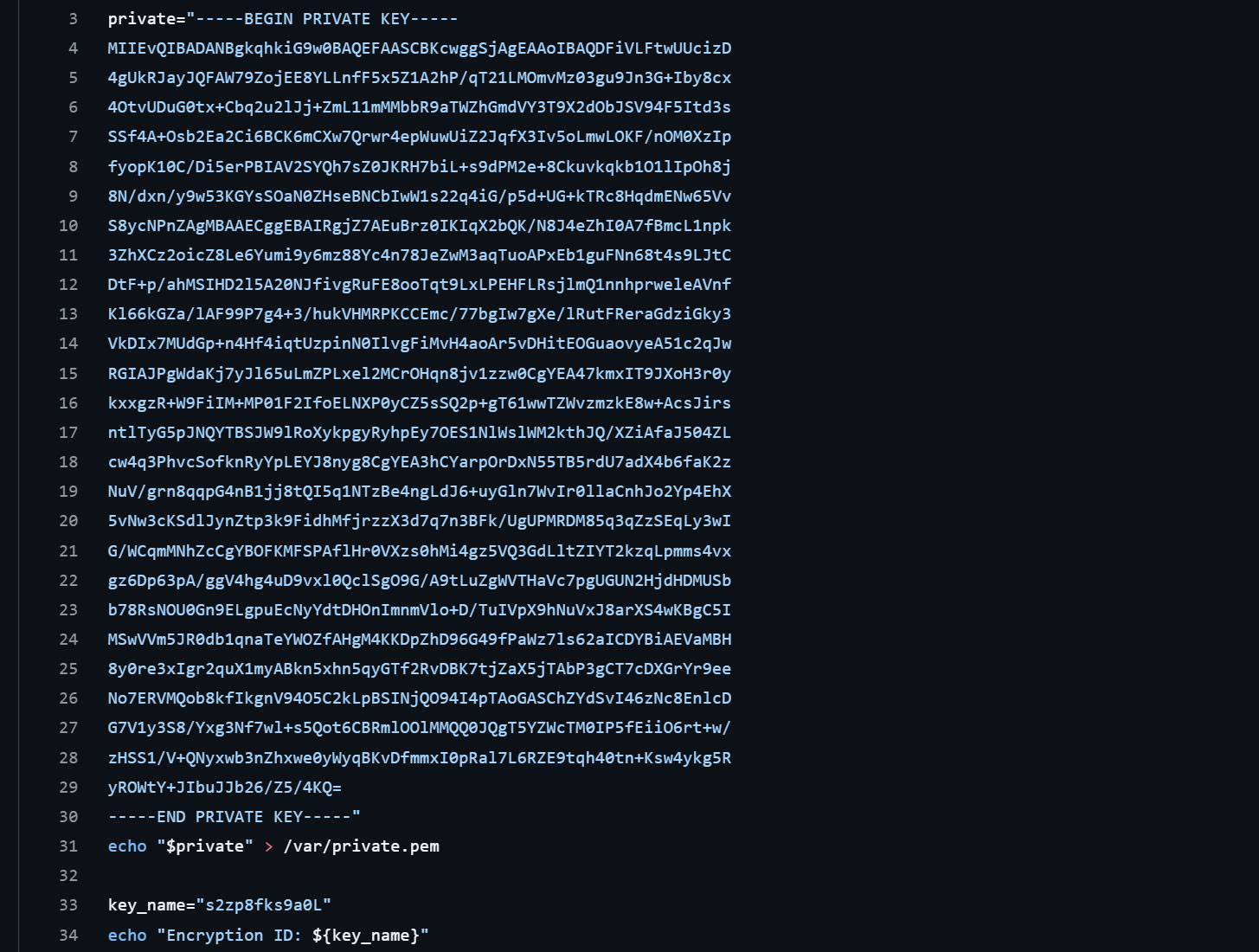
LeakIX and Chocapikk obtained the scripts used on this assault, which embrace an ak47.py script for exploiting the CyberPanel vulnerability and one other script named truly.sh to encrypt the information.
Nevertheless, the ransomware script features a vital mistake and used a personal RSA key as a substitute of a public key to encrypt the AES and IV information.
Supply: BleepingComputer
Ransomware professional Michael Gillespie advised BleepingComputer that this personal RSA will also be used to decrypt the encrypted AES and IV information, which might then be doubtlessly used to get well the information at no cost.
Impacted CyberPanel servers ought to have a decryptor situated in /var/decrypter.sh however it would doubtless should be modified to decrypt servers appropriately. If in case you have this file, please share a pattern with BleepingComputer so we will decide if it may be modified to get well information.
Because of the lively exploitation of the CyberPanel flaw, customers are strongly suggested to improve to the newest model on GitHub as quickly as potential.
