Japan’s Pc Emergency Response Heart (JPCERT/CC) has shared tips about detecting completely different ransomware gang’s assaults primarily based on entries in Home windows Occasion Logs, offering well timed detection of ongoing assaults earlier than they unfold too far right into a community.
JPCERT/CC says the method will be worthwhile when responding to ransomware assaults, and figuring out the assault vector amongst varied potentialities is essential for well timed mitigation.
Discovering ransomware traces in Occasion Logs
The investigation technique proposed by JPCERT/CC covers 4 kinds of Home windows Occasion Logs: Utility, Safety, System, and Setup logs.
These logs usually include traces left behind by ransomware assaults that might reveal the entry factors utilized by the attackers and their “digital identity.”
Listed here are some examples of ransomware traces highlighted within the company’s report:
- Conti: Recognized by many logs associated to the Home windows Restart Supervisor (occasion IDs: 10000, 10001).
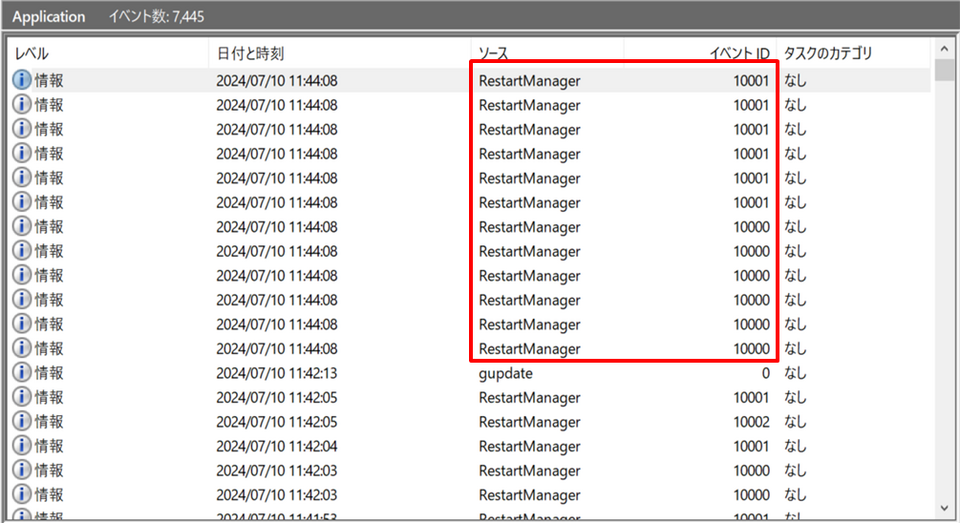
RestartManage notifications from Conti-based encryptors
Supply: JPCERT/CCRelated occasions are generated by Akira, Lockbit3.0, HelloKitty, Abysslocker, Avaddon, Bablock, and different malware created from Lockbit’s and Conti’s leaked encryptor.
- Phobos: Leaves traces when deleting system backups (occasion IDs: 612, 524, 753). Related logs are generated by 8base and Elbie.
- Midas: Modifications community settings to unfold an infection, leaving occasion ID 7040 in logs.
- BadRabbit: Information occasion ID 7045 when putting in an encryption element.
- Bisamware: Logs a Home windows Installer transaction’s begin (1040) and finish (1042).
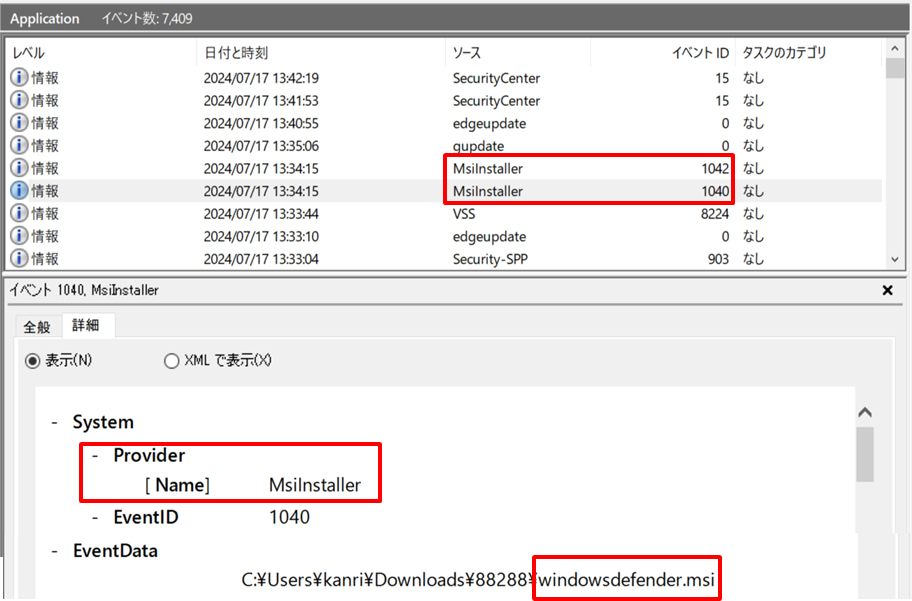
Supply: JPCERT/CC
JPCERT/CC additionally notes that seemingly unrelated ransomware variants comparable to Shade, GandCrab, AKO, AvosLocker, BLACKBASTA, and Vice Society, go away behind very comparable traces (occasion IDs: 13, 10016).
Each errors are induced by an absence of permissions when accessing COM functions to delete Quantity Shadow Copies, which ransomware sometimes deletes to forestall straightforward restoration of encrypted information.
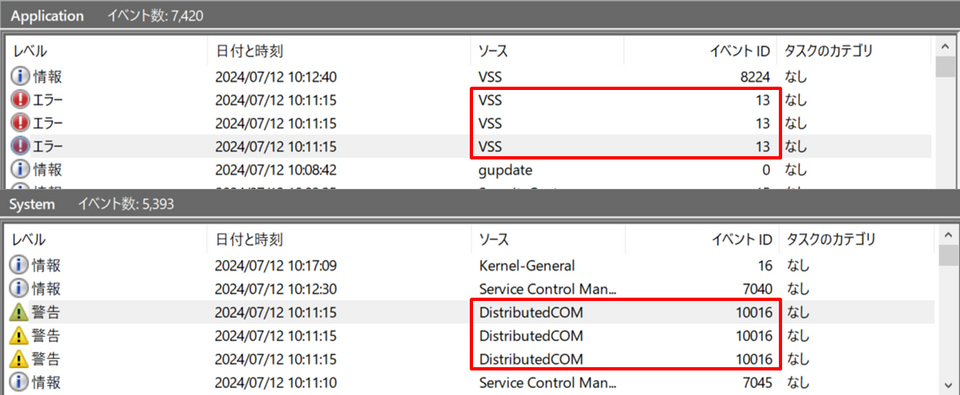
Supply: JPCERT/CC
It is necessary to notice that no detection methodology ought to be taken as a assure for satisfactory safety towards ransomware, however monitoring for particular logs can show game-changing when mixed with different measures to detect assaults earlier than they unfold too far right into a community.
JPCERT/CC notes that older ransomware strains comparable to WannaCry and Petya didn’t go away traces in Home windows logs, however the state of affairs has modified on fashionable malware, so the method is now thought-about efficient.
In 2022, SANS additionally shared a information on detecting completely different ransomware households utilizing Home windows Occasion Logs.
