Right this moment, Ivanti urged clients to patch a important authentication bypass vulnerability impacting Digital Visitors Supervisor (vTM) home equipment that may let attackers create rogue administrator accounts.
Ivanti vTM is a software-based software supply controller (ADC) that gives app-centric site visitors administration and cargo balancing for internet hosting business-critical companies.
Tracked as CVE-2024-7593, this auth bypass vulnerability is because of an incorrect implementation of an authentication algorithm that permits distant unauthenticated attackers to bypass authentication on Web-exposed vTM admin panels.
“Ivanti released updates for Ivanti Virtual Traffic Manager (vTM) which addressed a critical vulnerability. Successful exploitation could lead to authentication bypass and creation of an administrator user,” the corporate warned on Tuesday.
“We are not aware of any customers being exploited by this vulnerability at the time of disclosure. However, a Proof of Concept is publicly available, and we urge customers to upgrade to the latest patched version. “
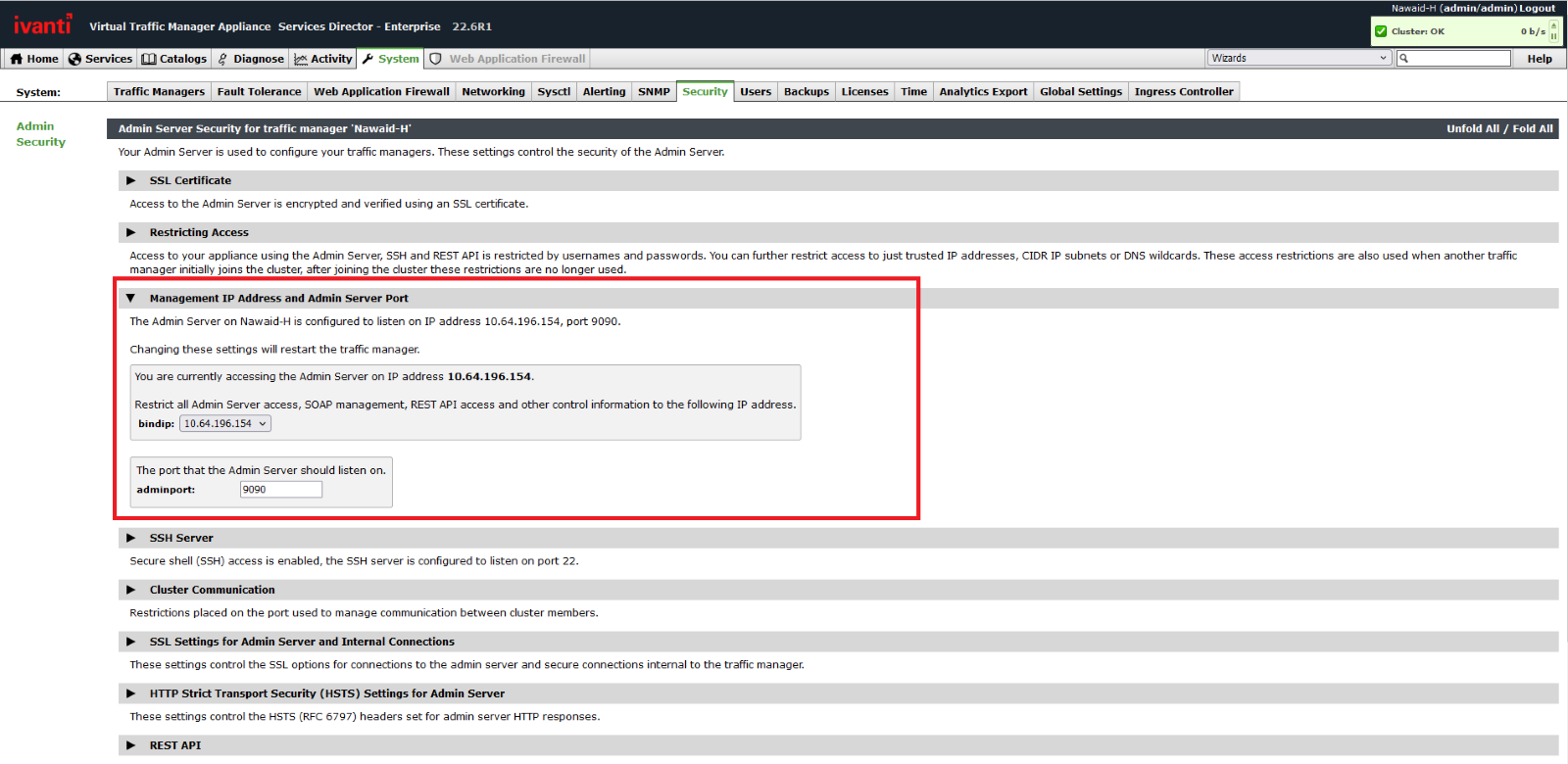
Ivanti advises admins to limit entry to the vTM administration interface by binding it to an inside community or personal IP tackle to scale back the assault floor and block potential exploitation makes an attempt.
To restrict admin entry to the administration interface by way of the personal/company community, admins should:
- Navigate to System > Safety, then click on the drop-down for the Administration IP Tackle and Admin Server Port part of the web page.
- Within the ‘bindip’ drop-down, choose the Administration Interface IP Tackle or use the setting immediately above the “bindip” setting to limit entry to trusted IP addresses, additional limiting who can entry the interface.
The safety flaw has been mounted in Ivanti vTM 22.2R1 and 22.7R2, with patches to be launched for the remaining supported variations over the approaching weeks.
Ivanti says it has no proof that the CVE-2024-7593 auth bypass has been exploited in assaults however suggested admins to test the Audit Logs Output for brand spanking new ‘user1’ or ‘user2’ admin customers added by way of the GUI or utilizing the publicly obtainable exploit code.
Right this moment, Ivanti additionally warned admins to right away patch an info disclosure vulnerability (CVE-2024-7569) in Ivanti ITSM on-prem and Neurons for ITSM variations 2023.4 and earlier. This vulnerability can let unauthenticated attackers acquire the OIDC consumer secret by way of debug info.
The corporate patched one other authentication bypass flaw (CVE-2024-22024) impacting Ivanti Join Safe, Coverage Safe, and ZTA gateways in February when it urged admins to safe weak home equipment instantly.
Ivanti VPN home equipment have been beneath assault since December 2023 utilizing exploits chaining the CVE-2023-46805 authentication bypass and the CVE-2024-21887 command injection flaws as zero days.
The corporate additionally warned of a 3rd zero-day (a server-side request forgery bug tracked as CVE-2024-21893) beneath mass exploitation in February, permitting risk actors to bypass authentication on unpatched ICS, IPS, and ZTA gateways.
