The Iranian state-sponsored hacking group APT34, aka OilRig, has just lately escalated its actions with new campaigns focusing on authorities and important infrastructure entities within the United Arab Emirates and the Gulf area.
In these assaults, noticed by Development Micro researchers, OilRig deployed a novel backdoor, focusing on Microsoft Change servers to steal credentials, and likewise exploited the Home windows CVE-2024-30088 flaw to raise their privileges on compromised gadgets.
Aside from the exercise, Development Micro has additionally made a connection between OilRig and FOX Kitten, one other Iran-based APT group concerned in ransomware assaults.
Newest OilRig assault chain
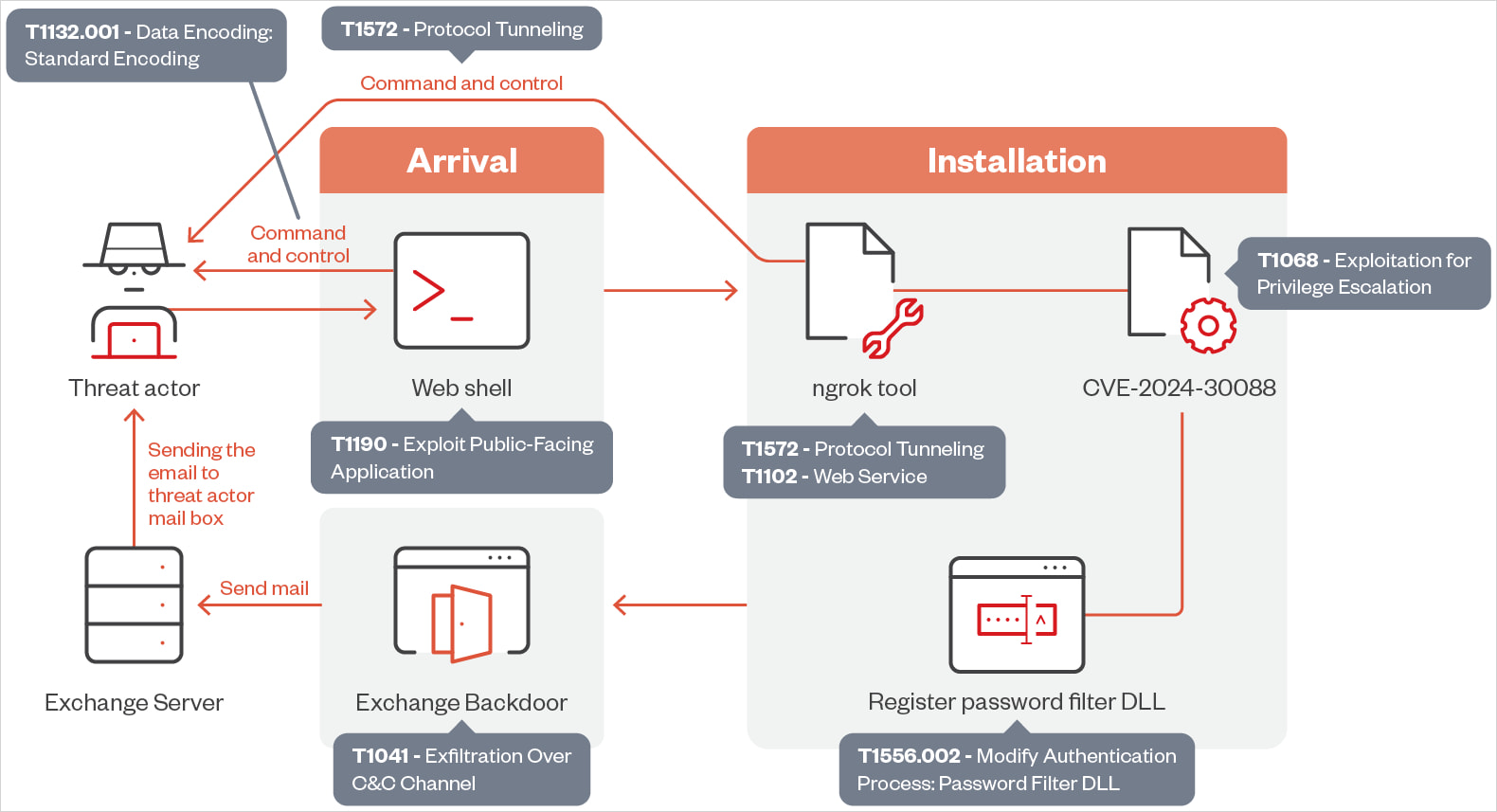
The assaults seen by Development Micro start with the exploitation of a susceptible internet server to add an online shell, giving the attackers the power to execute distant code and PowerShell instructions.
As soon as the online shell is energetic, OilRig leverages it to deploy further instruments, together with a part designed to take advantage of the Home windows CVE-2024-30088 flaw.
CVE-2024-30088 is a high-severity privilege escalation vulnerability Microsoft fastened in June 2024, enabling attackers to escalate their privileges to the SYSTEM degree, giving them important management over the compromised gadgets.
Microsoft has acknowledged a proof-of-concept exploit for CVE-2024-30088 however has not but marked the flaw as actively exploited on its safety portal. CISA has additionally not reported it as beforehand exploited in ts Identified Exploited Vulnerability catalog.
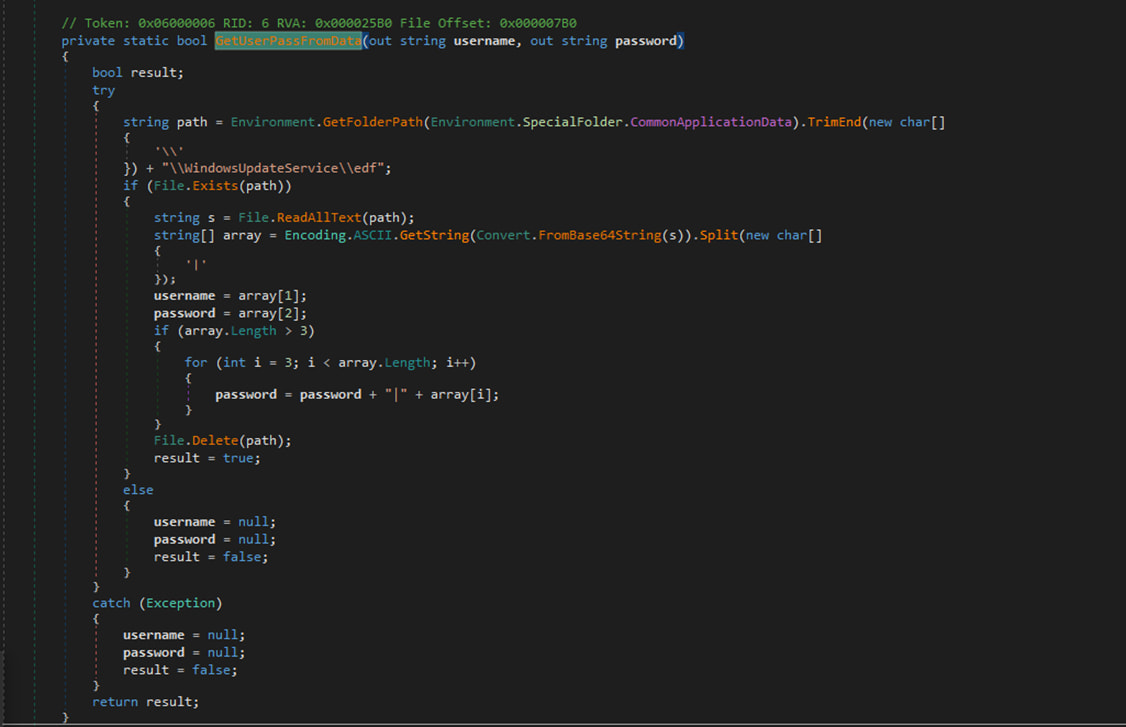
Subsequent, OilRig registers a password filter DLL to intercept plaintext credentials throughout password change occasions after which downloads and installs the distant monitoring and administration instrument ‘ngrok,’ used for stealthy communications by safe tunnels.
One other new tactic by the menace actors is the exploitation of on-premise Microsoft Change servers to steal credentials and exfiltrate delicate information through official electronic mail site visitors that’s exhausting to detect.
Supply: Development Micro
The exfiltration is facilitated by a brand new backdoor named ‘StealHook,’ whereas Development Micro says authorities infrastructure is commonly used as a pivot level to make the method seem official.
“The key objective of this stage is to capture the stolen passwords and transmit them to the attackers as email attachments,” explains Development Micro within the report.
“Additionally, we observed that the threat actors leverage legitimate accounts with stolen passwords to route these emails through government Exchange Servers.”
Supply: Development Micro
TrendMicro says there are code similarities between StealHook and backdoors OilRig utilized in previous campaigns, like Karkoff, so the most recent malware seems to be an evolutionary step quite than a novel creation from scratch.
Additionally, this isn’t the primary time OilRig has used Microsoft Change servers as an energetic part of their assaults. Nearly a yr in the past, Symantec reported that APT34 put in a PowerShell backdoor dubbed ‘PowerExchange’ on on-premise Change servers able to receiving and executing instructions through electronic mail.
The menace actor stays extremely energetic within the Center East area, and its affiliation with FOX Kitten, whereas unclear at the moment, is worrying for the potential of including ransomware to its assault arsenal.
Since many of the focused entities are within the vitality sector, in response to Development Micro, operational disruptions in these organizations may severely impression many individuals.
