A brand new joint cybersecurity advisory from the Federal Bureau of Investigation, the Cybersecurity and Infrastructure Safety Company, and the Division of Protection Cyber Crime Middle uncovered new details about the notorious Iran-based risk actor referred to as Fox Kitten.
The group sells the company entry they receive in cybercriminal’s underground boards and collaborates actively with ransomware associates to help in ransoming victims. The risk actor has set their sights on infiltrating the U.S. and different international organizations in current weeks.
Who’s Fox Kitten?
Fox Kitten — also called Pioneer Kitten, UNC757, Parasite, Rubidium, and Lemon Sandworm — is a risk actor that has actively dedicated cyberespionage since at the very least 2017.
The FBI stated that the group is related to the Iranian authorities and helps the theft of delicate technical knowledge towards varied organizations, per the advisory. The risk actor has focused firms within the middle-east comparable to Israel and Azerbaijan, but additionally firms in Australia, Finland, Eire, France, Germany, Algeria, Turkey, the U.S., and probably extra.
In keeping with the advisory, Fox Kitten has carried out a excessive quantity of pc community intrusion makes an attempt towards U.S. organizations since 2017. Their targets have included U.S.-based colleges, municipal governments, monetary establishments, and healthcare services, with incidents as current as August 2024.
OT cybersecurity firm Dragos famous that the risk actor additionally focused ICS-related entities by exploiting vulnerabilities in Digital Non-public Community home equipment.
The advisory additionally revealed that the group makes use of “the Iranian company name Danesh Novin Sahand (identification number 14007585836), likely as a cover IT entity for the group’s malicious cyber activities.”
Extra than simply cyberespionage
In 2020, operation “Pay2Key,” led by Fox Kitten, confirmed that the risk actor might comply with different targets moderately than simply facilitating cyberespionage.
In keeping with Israeli-based firm ClearSky Cyber Security, ransomware assaults focused Israeli organizations with beforehand unreported ransomware, but the assault marketing campaign was seemingly propaganda to trigger concern and create panic in Israel. Knowledge stolen throughout the assaults was uncovered publicly on a leak web site that talked about “Pay2Key, Israel cyberspace nightmare!” as proven within the report.
One other report, printed by cybersecurity firm CrowdStrike in 2020, revealed that the risk actor additionally marketed to promote entry to compromised networks on an underground discussion board. Researchers take into account this exercise as a possible try at income stream diversification, alongside the focused intrusions in assist of the Iranian authorities.
Collaboration with ransomware associates
As soon as Fox Kitten has obtained entry to sufferer networks, the group collaborates with a couple of ransomware associates from the NoEscape, RansomHouse, and ALPHV/BlackCat. The risk actor supplies full entry to ransomware associates in trade for a proportion of the ransom funds.
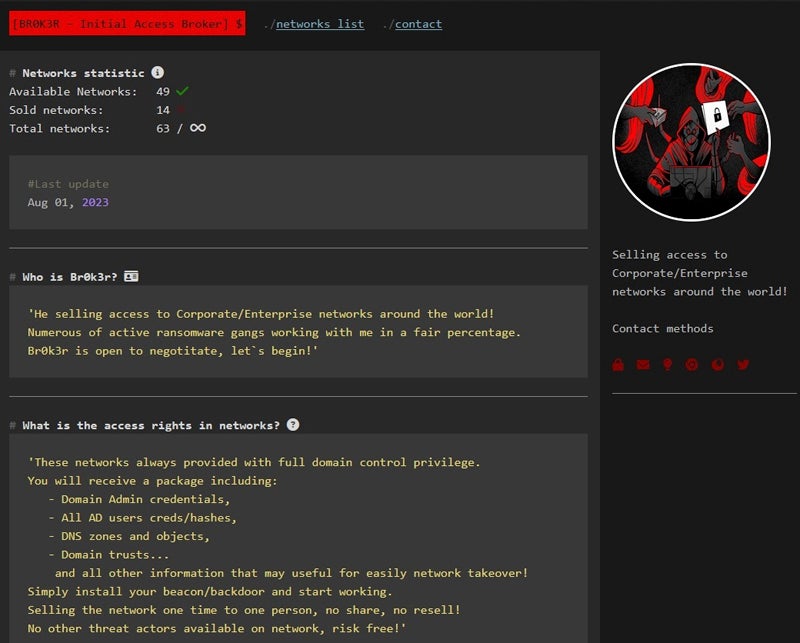
Fox Kitten supplies extra than simply entry to compromised networks, in line with the FBI. The group works intently with the ransomware associates to lock sufferer networks and strategize approaches to extort victims. But the group doesn’t reveal its Iran-based location to their ransomware affiliate contacts and stays obscure as to their origin.
The joint advisory reveals that the group refers to themselves by the moniker “Br0k3r” and has used “xplfinder” of their channels in 2024.
Technical particulars
Fox Kitten makes use of the Shodan search engine to establish IP addresses internet hosting gadgets susceptible to particular exploits, comparable to Citrix Netscaler, F5 Massive-IP, Pulse Safe/Ivanti VPNs, or PanOS firewalls.
As soon as the vulnerabilities are exploited, the risk actor:
- Crops webshells and captures login credentials earlier than creating malicious duties so as to add backdoor malware and proceed compromising the system.
- Makes use of compromised credentials to create new accounts on victims’ networks utilizing discreet names comparable to “IIS_Admin” or “sqladmin$.”
- Positive aspects management of admin credentials to log into area controllers and different components of the infrastructure. Current safety software program and antivirus are additionally disabled.
‘Br0k3r’ has been energetic for greater than a 12 months
The joint advisory supplies a number of indicators of compromise but additionally lists the TOX identifiers for the moniker “Br0k3r.” TOX is a peer-to-peer on the spot messaging software program designed to supply safe communications and makes use of distinctive keys to establish customers.
The distinctive TOX ID for “Br0k3r” has already been uncovered in 2023 by the SANS Institute as an Preliminary Entry Dealer promoting entry to company networks in numerous international locations, together with the U.S., Canada, China, the U.Ok., France, Italy, Norway, Spain, India, Taiwan, and Switzerland.
It’s no shock to see the risk actor goal the U.S., as it’s the most ransomware-impacted nation in accordance to cybersecurity firm MalwareBytes.
Leveraging cybercriminal boards
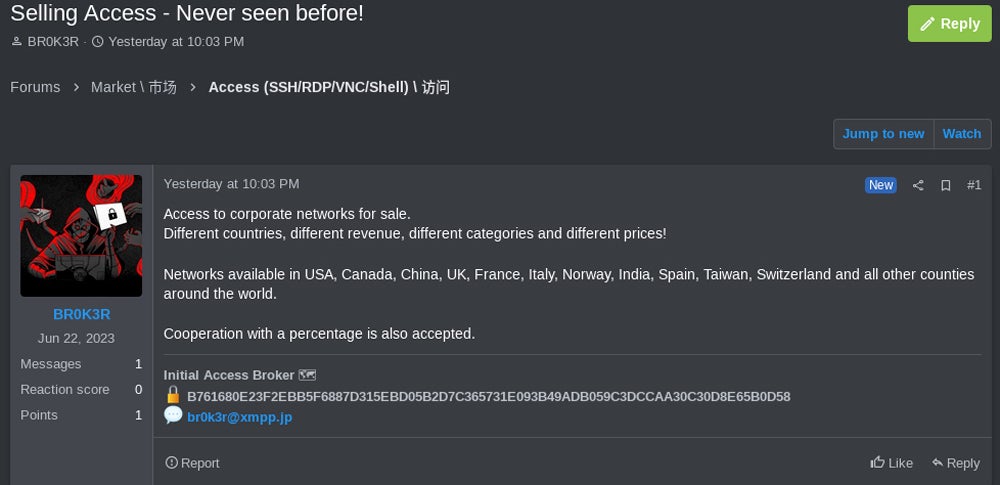
The risk actor supplied a novel Tor-hosted web site to promote their entry on a number of completely different cybercriminal’s boards.
A primary model of Br0k3r’s web site signifies that each sale incorporates full-domain management, together with area admin credentials, Lively Listing person credentials, DNS zones and objects, and Home windows Area trusts.
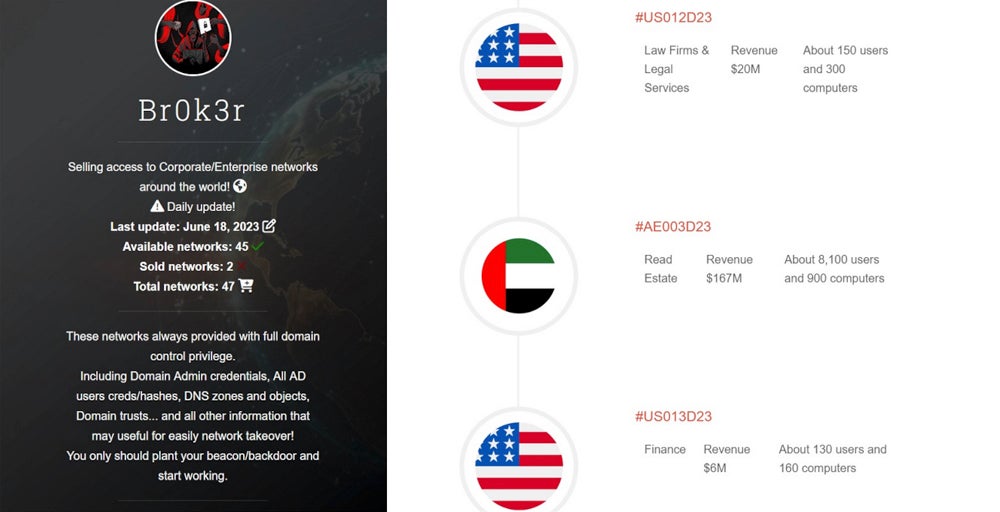
A second model of the web site launched round August 2023 signifies “Numerous active ransomware gangs working with me in a fair percentage.”
shield your corporation from this risk
The preliminary compromise methodology deployed by Fox Kitten consists of exploiting recognized vulnerabilities in a number of completely different Web-facing home equipment, particularly company VPNs or firewall home equipment. To guard from this cyber risk, firms ought to:
- Replace and patch VPN and firewall home equipment to keep away from falling for such vulnerabilities.
- Replace and patch all working programs, and software program have to be up-to-date and patched.
- Monitor who has entry to VPNs for any suspicious connection or connection try. Filtering on the VPN home equipment also needs to be used, so workers can solely join from their traditional Web connection when essential.
- Examine and analyze log recordsdata. Any discovery of an indicator of compromise supplied within the joint report should result in fast investigation.
- Deploy safety options on each endpoint and server in an effort to detect suspicious exercise.
Lastly, the FBI and the CISA don’t advocate paying the ransom, as there isn’t a assure that victims will recuperate their encrypted recordsdata, and people funds may also fund different legal actions.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.