South Korean VPN supplier IPany was breached in a provide chain assault by the “PlushDaemon” China-aligned hacking group, who compromised the corporate’s VPN installer to deploy the customized ‘SlowStepper’ malware.
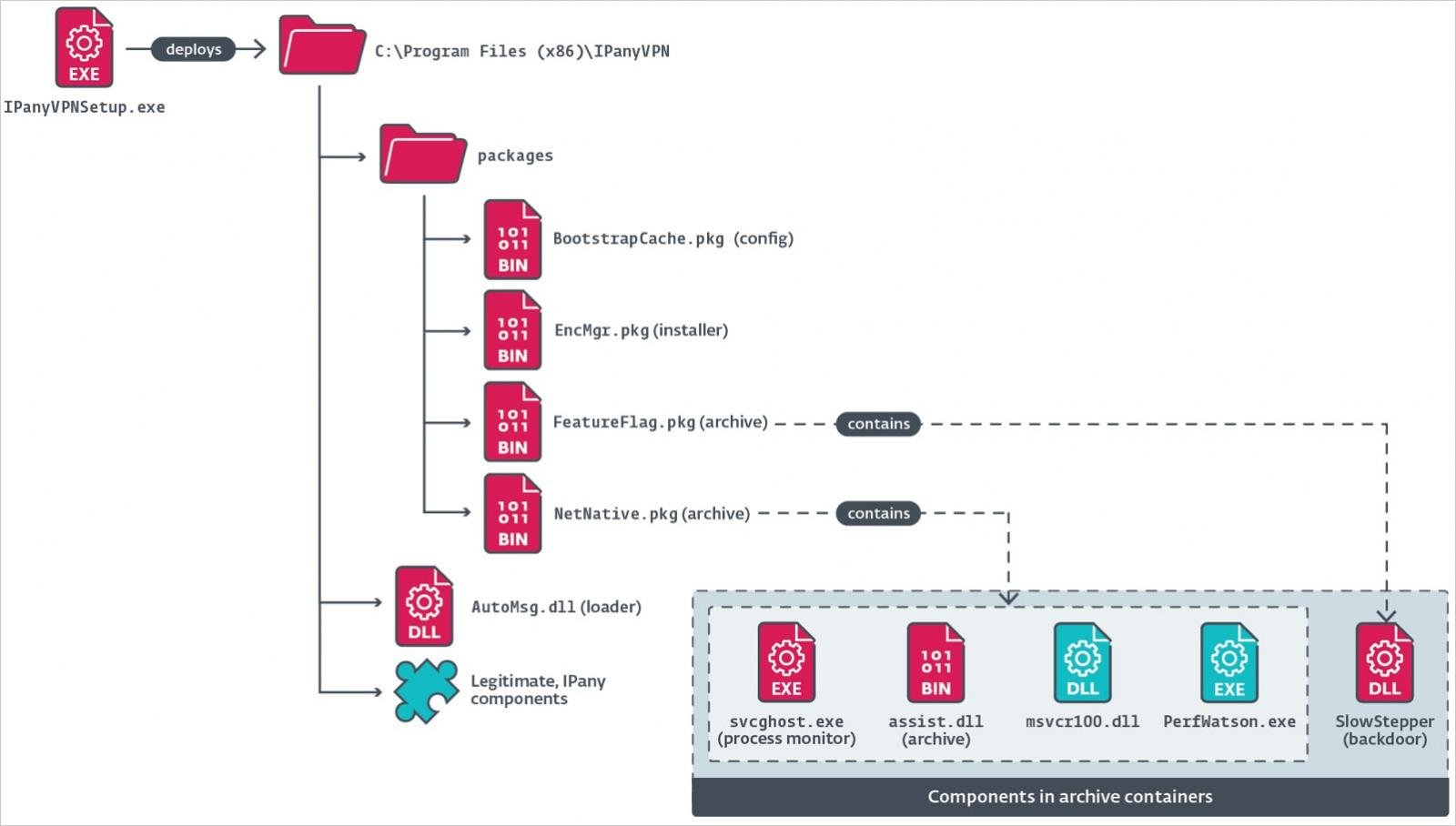
The hackers managed to infiltrate IPany’s growth platform and insert its customized ‘SlowStepper’ backdoor on its installer (‘IPanyVPNsetup.exe’), which contaminated buyer techniques when the VPN was put in.
In accordance with ESET researchers who uncovered the provision chain assault, firms impacted by the assault embody a South Korean semiconductor agency and a software program growth firm. Nevertheless, the primary indicators of contaminated victims date again to November 2023 in Japan.
SlowStepper exercise
IPany clients turn into contaminated after downloading this system’s ZIP installer (‘IPanyVPNsetup.zip’) from the corporate’s web site.
As soon as the installer is executed, it installs the authentic VPN product in addition to malicious information (‘svcghost.exe’), for which a Run secret is added within the Registry for persistence.
Supply: ESET
The SlowStepper payload is loaded from a picture file (‘winlogin.gif’) by way of a malicious DLL (‘lregdll.dll’) that’s sideloaded right into a ‘PerfWatson.exe’ course of. The svcghost executable screens the method to make sure it’s at all times operating.
ESET says the actual model of SlowStepper utilized in these assaults is 0.2.10 Lite, which isn’t as fully-featured as the usual model however might be stealthier as a result of its smaller footprint and continues to be a potent software.
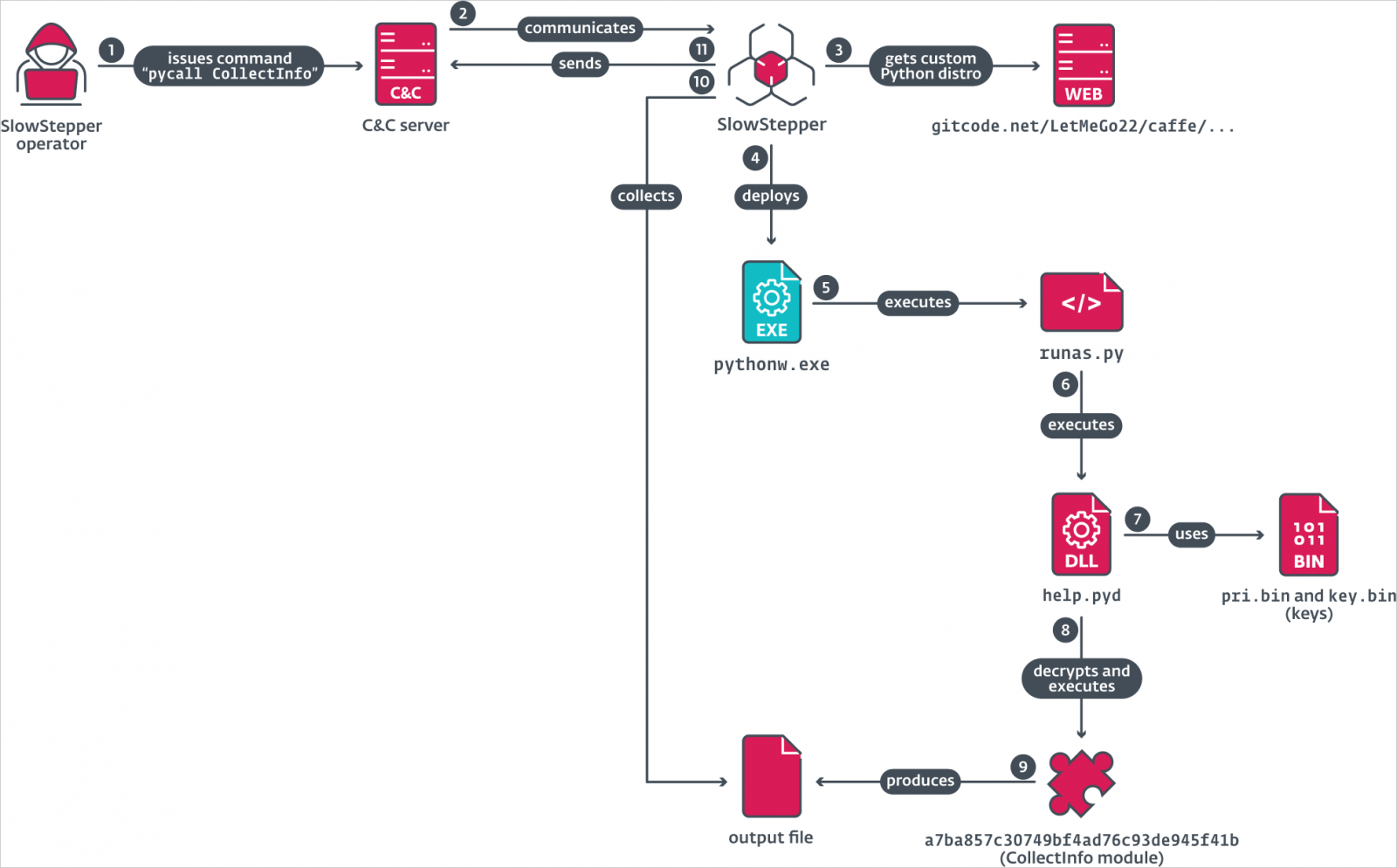
“Both the full and Lite versions make use of an array of tools programmed in Python and Go, which include capabilities for extensive collection of data, and spying through recording of audio and videos,” explains ESET.
Crucial instructions supported by SlowStepper are:
- 0x32 – Gathers quite a lot of system particulars, together with CPU model, HDD serial numbers, pc and hostname, public IP handle, operating processes, put in purposes, community interfaces, system reminiscence, webcam, and microphone standing, and whether or not the OS is operating in a digital machine.
- 0x5A – Fetch and run information from the C&C server, enabling the set up of further payloads.
- 0x3F – Enumerate information and directories on the compromised system.
- 0x38 – Run Python-based adware instruments designed for numerous espionage features, reminiscent of browser knowledge theft, keylogging, and credential harvesting.
- 0x3A – (Shell mode activation) Allows direct execution of system instructions, offering attackers with an interactive atmosphere for controlling the compromised machine.
- 0x39 – Delete particular information or directories, which can be utilized to erase traces of the malware or disrupt system performance.
- pycall <module_name> – Masses and runs particular Python adware modules, reminiscent of “Browser” for stealing browser knowledge, “WeChat, Telegram, DingTalk” for extracting chat logs, “ScreenRecord” for capturing display exercise, “Camera” for taking footage utilizing the webcam, and “CollectInfo” for scanning the disk for delicate paperwork.
Supply: ESET
The researchers contacted the VPN vendor to tell them of the compromise, and the malicious installer was faraway from the web site. Nevertheless, those that are already contaminated have to take motion to wash their techniques.
ESET underlines that the obtain web page didn’t characteristic geo-fencing mechanisms or every other instruments to point particular focusing on, so anybody who downloaded IPanyVPN from November 2023 (and probably earlier) till Might 2024 has been contaminated by SlowStepper.
The entire record of the symptoms of compromise (IoCs) related to this marketing campaign could be discovered right here.
