Threat administration is a vital a part of securing any digital transformation effort. The expansion in use of cloud-native purposes and microservices structure is driving a broader business development towards extra purposes. For AppSec groups, the motion to completely different dev groups working concurrently on completely different launch schedules has prompted a marked development in complexity. Or, put extra merely: issues are getting actually exhausting on the market for AppSec groups.
In response, extra firms are buying extra instruments to position safety controls at a number of factors throughout the software program improvement lifecycle (SDLC). Nevertheless, the variety of instruments in locations doesn’t essentially equate to a lower in improvement time or efficiencies in different assets. Extra instruments usually simply imply extra vulnerabilities, and AppSec groups are notoriously understaffed and under-resourced to handle dangers successfully.
Threat administration: No ache, no achieve?
AppSec groups don’t all the time know the place to start out when assessing and managing threat. Most groups have a number of instruments that present completely different outputs in numerous codecs. Orchestrating numerous knowledge units reminiscent of these could be a daunting job; however figuring out, assessing, and mitigating the largest dangers is crucial to defending your enterprise.
How do organizations start assessing their threat? Step one is often to conduct a complete threat evaluation. As soon as the dangers are recognized, they must be evaluated primarily based on their chance of being exploited and potential influence of that exploitation. This analysis is usually a extremely handbook course of, nevertheless it permits organizations to prioritize dangers and allocate assets accordingly to create a threat mitigation technique.
The method usually entails implementing new controls and safeguards, transferring dangers by insurance coverage, or accepting sure dangers inside predefined tolerance ranges. Deciding on an acceptable threat mitigation technique depends upon the particular threat and the group’s threat urge for food.
This course of might be tedious, and because it’s not only a one-time course of, it’s usually a big ache level for AppSec managers, builders, and organizations. It requires many shifting elements, and if there is no such thing as a centralized place to maintain and share the findings, dangers can go “detected,” however unnoticed.
Don’t Neglect to Optimize the “Developer Experience”
Along with their threat administration obligations, AppSec groups want to keep up a robust relationship with one among their most vital inner clients and companions: improvement groups. To construct a profitable AppSec program, the builders have to be introduced onboard.
Builders are pressured to prioritize time to market. Whereas creating safe code is changing into a extra vital a part of their obligations, it’s not their major focus. In keeping with our latest Pulse Survey, 35% of builders are experiencing growing calls for and shorter timelines to launch new software program, and 86% of respondents have launched known-vulnerable code to fulfill launches.
Everyone knows that builders don’t essentially wish to use further safety instruments, and definitely don’t wish to use the person dashboards in these safety instruments. Supporting builders by sturdy developer expertise is crucial not simply to the success of software safety applications, but in addition to the general processes and instruments that enable organizations to shift safety in all places.
For AppSec groups, the “developer experience” means offering builders the chance to have a greater safety expertise. When working with AppSec instruments, builders usually change into overwhelmed with the fixed “noise versus signal” determination making that’s usually placed on their plate as a result of it’s unclear what dangers they should prioritize. Sorting by the noise and making an attempt to prioritize rapidly can change into an enormous waste of time for every particular person developer – resulting in massive drops in productiveness. This in flip may cause a rift between builders and AppSec groups that would take further time and assets to aim to repair. When working with safety instruments, builders have to belief the outcomes they get and see an important issues for them to repair first.
At Checkmarx, we’ve particularly developed instruments to assist:
Introducing: Software Threat Administration as a part of Fusion 2.0
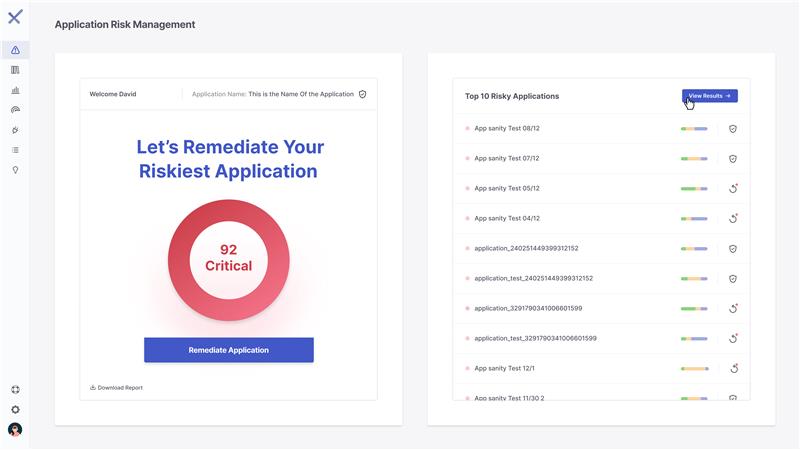
Final 12 months we launched Fusion, which correlated and prioritized vulnerabilities throughout each AST engine on Checkmarx One. Now, Fusion 2.0 provides Software Threat Administration – a module that may assist you to view the applying safety posture of your total software portfolio and footprint.
Customers will be capable to begin with a complete threat rating for all their purposes, so AppSec managers can see rapidly what must be addressed first. With this answer, AppSec managers can effectively handle and prioritize vulnerabilities by offering a centralized and consolidated view of safety dangers. This immediately removes the complexity {that a} disorganized threat administration course of can carry with it. As soon as AppSec managers can zero in on the riskiest purposes, groups can level builders to vital vulnerabilities that want remediation (like you could possibly in Fusion 1.0).
This new function permits AppSec groups to really prioritize and triage probably the most vital vulnerabilities on the riskiest purposes. It permits us to create a greater developer expertise, since we now are giving clear indicators as to the place the very best influence areas are, as an alternative of getting them waste their time wading by the noise.
Profitable threat administration requires fixed vigilance. Common monitoring permits organizations to determine modifications within the threat panorama, whereas additionally permitting for well timed remediation in opposition to rising vital dangers. Unnoticed and unmediated vulnerabilities can open a proverbial Pandora’s field in relation to exploits – the longer a vital threat stays unaddressed, the larger the potential for malicious customers to reap the benefits of it. Everyone knows that point is cash, and nobody is aware of this higher than unhealthy actors. Our threat administration function additionally consists of an unaddressed vital threat timer, which can let AppSec managers and builders know the time elapsed on unaddressed vital dangers.
Most vital although, is {that a} sturdy threat administration system may help create a tradition of resilience inside organizations and AppSec groups. When companies are conscious of what dangers they’re going through, they will proactively make higher choices in a regard to how they will navigate sure challenges and capitalize on different alternatives. Software threat administration is a elementary a part of a strong threat administration observe because it helps your AppSec groups do it higher.
Able to be taught extra? Try the brand new Software Threat Administration module for Checkmarx One!