In recent times, virtually each main cloud breach has been marked by overly permissive credentials, adopted by lateral motion and privilege escalation. These vulnerabilities have allowed attackers to navigate by way of programs with ease, escalating their privileges to trigger important hurt. It’s essential for cloud risk responders to concentrate on threats as they happen and to have the ability to include these assaults swiftly and successfully.
Id performs a important position because the connective tissue in investigations, offering the required context to grasp and hint the actions of customers. Sysdig stands on the forefront of this want by providing options to handle your identification safety. With Sysdig, organizations can forestall assaults by strengthening their identification posture, and detect anomalous or suspicious actions executed by customers, making certain a strong protection in opposition to potential threats. This proactive method not solely fortifies safety, but in addition enhances the flexibility to reply to incidents in actual time, making it an indispensable device in trendy cybersecurity.
What’s new: Cloud Id Insights
Cloud Id Insights gives the context organizations have to get forward of assaults and take motion earlier than risk actors abuse compromised consumer accounts. This new addition enhances Sysdig’s cloud detection and response (CDR) capabilities, making it easy to correlate identification conduct with occasions and detect and reply to probably compromised customers. It additionally helps groups forestall related assaults sooner or later. Armed with these new capabilities, safety groups can reply instantly to include assaults in movement and strengthen identification posture to implement zero belief within the cloud.
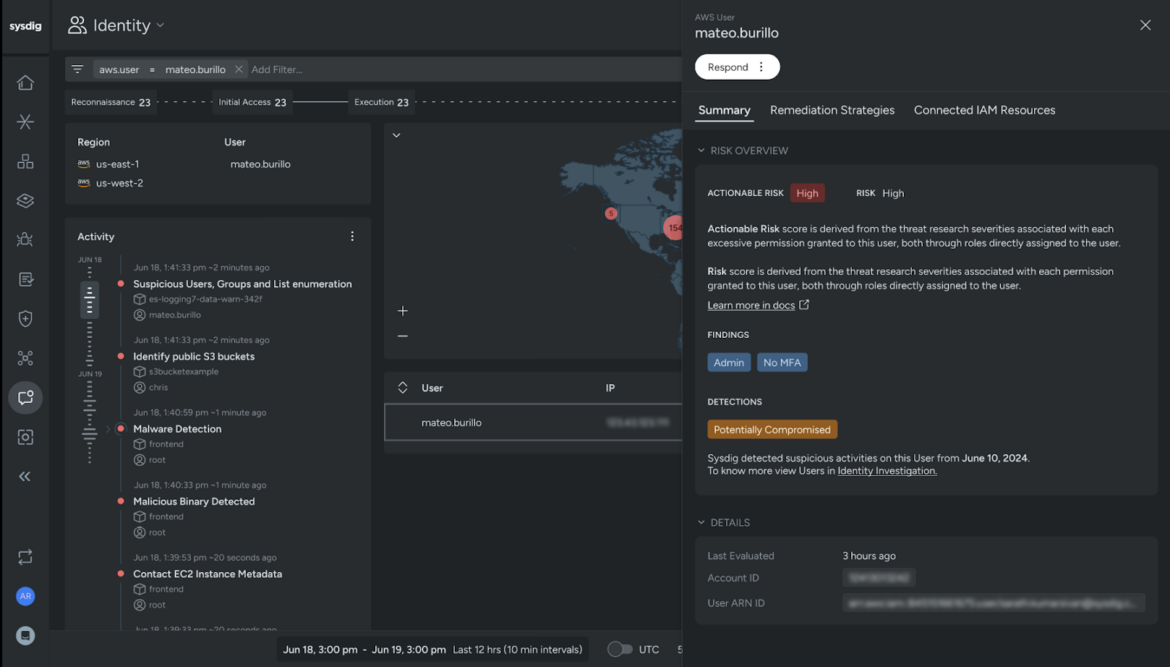
Doubtlessly compromised customers
Misconfigured identities and secrets and techniques usually function the preliminary entry factors for attackers, making them important vulnerabilities in any safety technique. Sysdig addresses this subject by detecting irregular exercise, together with patterns of actions generally noticed throughout varied phases of a breach. This proactive detection is significant for incident responders, who should be notified when a consumer is probably compromised to allow them to promptly begin investigating the incident. By figuring out and addressing these early indicators of compromise, Sysdig helps to fortify safety defenses and allow faster, more practical responses to potential threats.
Compromised customers
Incident responders want the flexibility to rapidly verify whether or not or not a consumer is genuinely compromised to allow them to appropriately escalate or deescalate the scenario. The potential to flag a consumer as confirmed compromised creates a transparent sign to the group that the incident has been completely triaged and isn’t a false optimistic. This ensures a centered and environment friendly response, permitting the group to prioritize and tackle precise threats with out being sidetracked by false alarms.
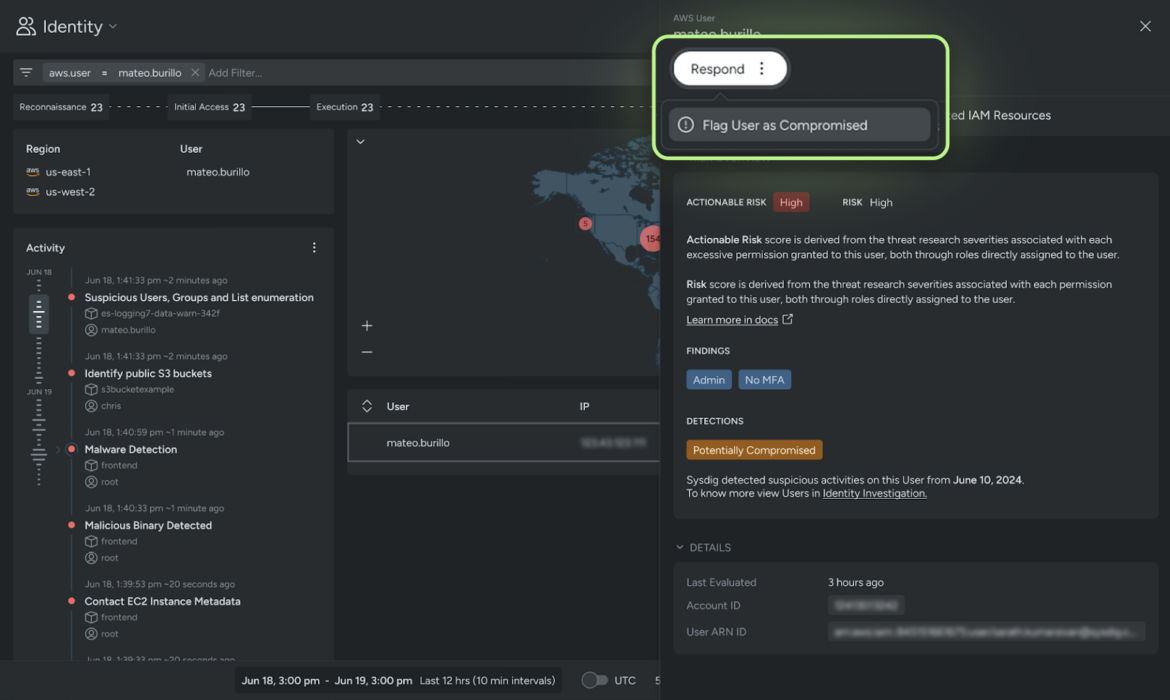
Include compromise
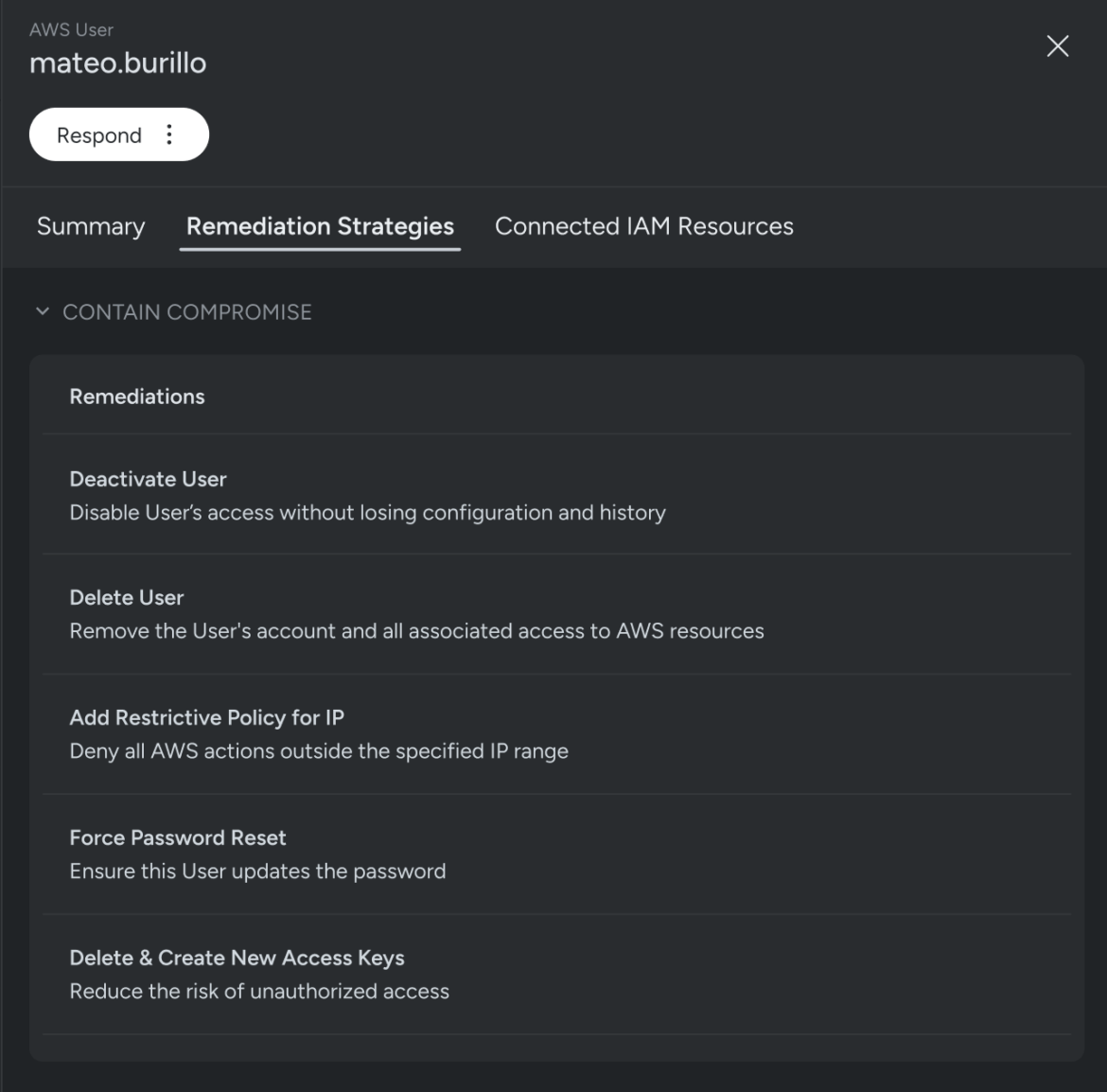
Cloud risk responders have to be geared up with the data and instruments to halt an assault that’s actively in progress to allow them to include the risk and defend their enterprise. When a consumer is flagged as probably compromised, Sysdig steps in to supply a spread of choices, every with various ranges of depth, to include the compromise successfully. Potential actions can vary from deleting and creating new entry keys all the best way to deactivating or deleting a consumer.
Sysdig gives detailed playbooks for every choice, guiding responders by way of the steps essential to include the compromise. This structured method permits responders to behave swiftly and decisively, minimizing the impression of the assault and safeguarding their group’s property.
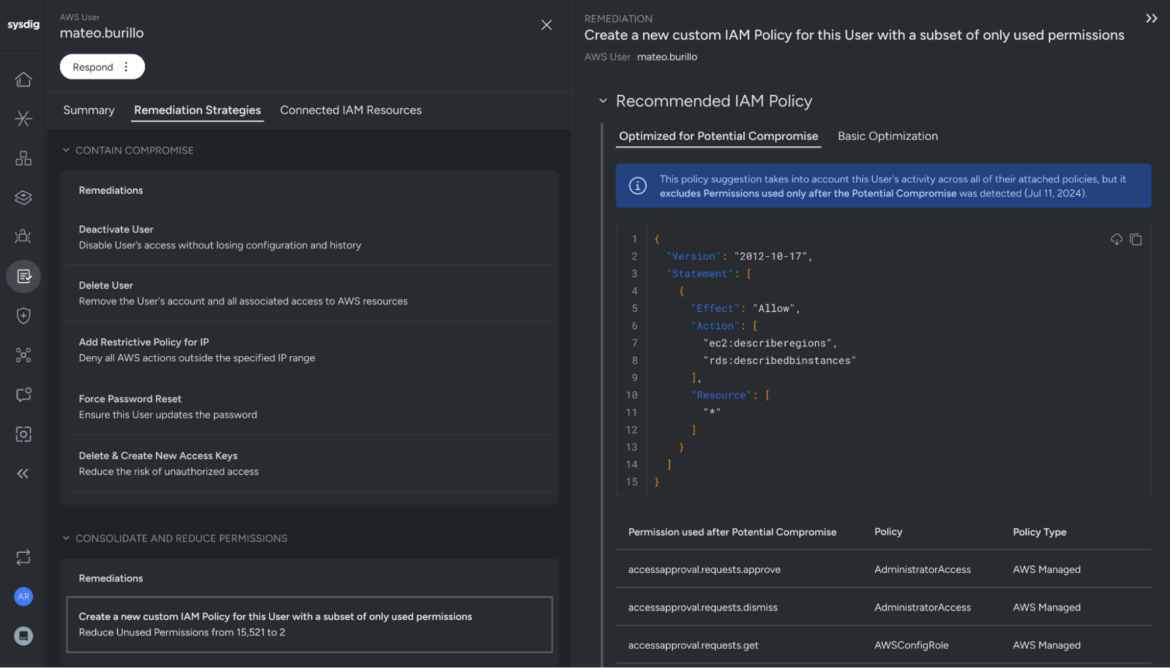
Obtain zero belief by way of least permissive coverage optimization
Attaining zero belief within the cloud basically depends on reaching a state of least permissive entry. The Sysdig Menace Analysis group has found that, on common, solely two p.c of all granted permissions are literally used. To handle this, Sysdig generates Least Permissive Coverage Optimization solutions by analyzing cloud logs and together with solely the permissions which are actively used.
To make sure that these optimizations are usually not compromised by malicious actions, Sysdig takes a proactive method. It tracks all permissions used solely after a consumer is flagged as probably compromised and, by default, excludes these permissions from coverage optimizations. This cautious scrutiny helps preserve the integrity of safety insurance policies, making certain that solely respectable permissions are granted and decreasing the danger of privilege escalation and lateral motion by risk actors.
Goal your riskiest identities for posture hardening
Since attackers usually goal identities to realize preliminary entry to environments, safety groups ought to concentrate on hardening their posture round these entry factors. Sysdig assists on this effort by providing opinionated suggestions on which customers and roles to focus on first. On the Dangers web page, Sysdig highlights the identities that current the best danger, enabling safety groups to prioritize their efforts and strengthen their defenses successfully.
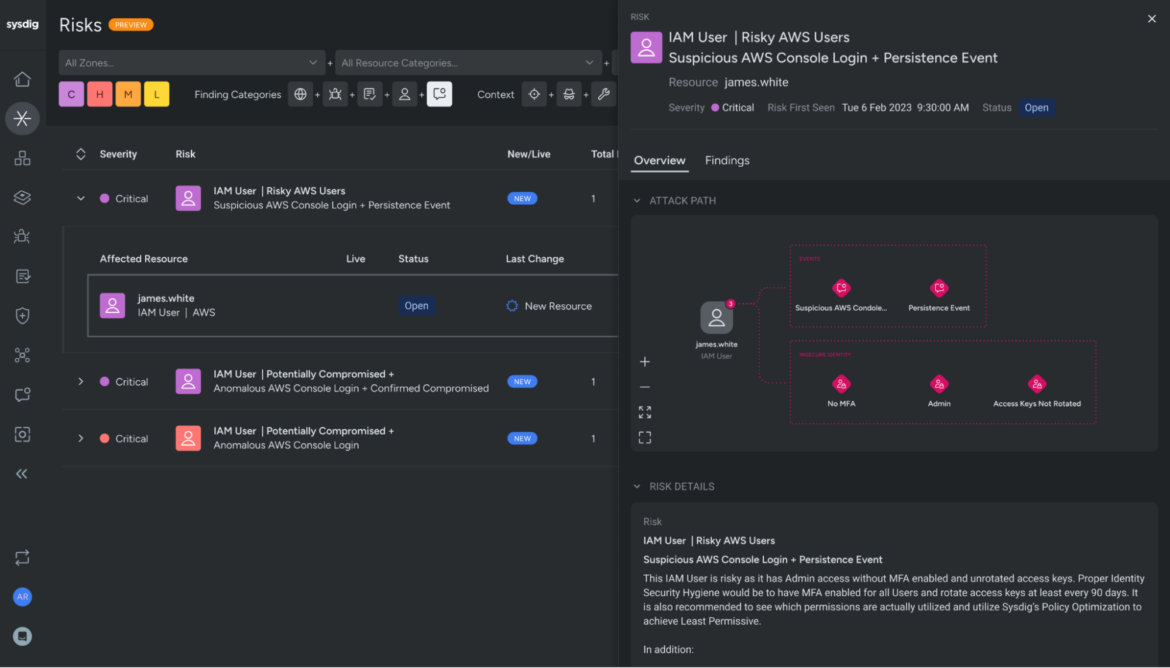
Cease assaults on the first signal of compromise with Cloud Id Insights
The velocity of cloud assaults warrants having real-time risk detection. Id is a key piece of understanding breaches with a purpose to correlate malicious exercise. Flagging customers as probably compromised lets your safety response groups know they should examine. Sysdig’s Cloud Id Insights takes into consideration real-time detection of malicious consumer exercise, and the best way to harden identification safety posture to forestall breaches within the first place.
Be a part of our upcoming deminar, Cloud Id Insights: Cease Compromised Identities in Minutes, for an interactive showcase of those options.