Whereas the usage of Infrastructure as Code (IaC) has gained important reputation as organizations embrace cloud computing and DevOps practices, the velocity and suppleness that IaC offers may also introduce the potential for misconfigurations and safety vulnerabilities.
IaC permits organizations to outline and handle their infrastructure utilizing machine-readable configuration information, that are usually version-controlled and handled as code. IaC misconfigurations are errors, or oversights, within the configuration of infrastructure assets and environments that occur when utilizing IaC instruments and frameworks.
Misconfigurations in IaC can result in safety vulnerabilities, operational points, and even potential breaches.
Widespread kinds of misconfigurations
Widespread misconfigurations embrace weak entry controls, improperly uncovered ports, insecure community configurations, or mismanaged encryption settings. A number of the commonest kinds of IaC Safety misconfigurations are:
- Entry Controls: Misconfigurations associated to entry controls may end up in unauthorized entry to assets. This contains points corresponding to overly permissive entry permissions, misconfigured role-based entry management (RBAC), or incorrect safety group guidelines. Attackers can exploit these misconfigurations to realize unauthorized entry to delicate knowledge, or programs.
- Community Configuration: Misconfigurations in community settings can expose companies or purposes to pointless dangers. For instance, improperly configured firewall guidelines, open ports, or lack of community segmentation can result in unauthorized entry, community assaults, or knowledge exfiltration.
- Encryption and Information Safety: Failure to implement correct encryption and knowledge safety measures may end up in knowledge breaches. Misconfigurations could embrace not encrypting knowledge at relaxation or in transit, utilizing weak encryption algorithms or keys, or storing delicate knowledge in insecure areas.
- Logging and Monitoring: Misconfigurations associated to logging and monitoring can hinder the flexibility to detect and reply to safety incidents. This contains improper configuration of log assortment, aggregation, and retention, or misconfigured monitoring guidelines, resulting in missed alerts and delayed incident response.
- Secret Administration: IaC misconfigurations can expose delicate credentials or secrets and techniques, corresponding to API keys, database passwords, or encryption keys. Storing secrets and techniques in plaintext, checking them into model management programs, or together with them in IaC templates can result in unauthorized entry or misuse.
- Useful resource Permissions: Misconfigurations in useful resource permissions may end up in extreme or inadequate privileges. Overly permissive permissions could permit unauthorized actions, whereas overly restrictive permissions can impede correct performance or result in operational disruptions.
- Cloud Supplier-specific Misconfigurations: IaC misconfigurations can differ relying on the cloud supplier getting used. Every supplier has its personal set of companies, configuration choices, and safety controls. Misconfigurations could contain misusing or misconfiguring particular companies, not following finest practices, or overlooking provider-specific safety suggestions.
- Compliance and Governance: Misconfigurations may end up in non-compliance with trade laws, knowledge safety legal guidelines, or inner governance necessities. Failure to configure assets in accordance with these tips can result in authorized and regulatory penalties.
IaC misconfigurations can, in fact, result in safety vulnerabilities, however they’ll additionally make infrastructure administration and upkeep more difficult for AppSec managers and improvement groups. When misconfigurations are pervasive, it turns into tougher to establish and rectify them throughout updates, scaling, or altering infrastructure necessities. This may end up in longer deployment cycles, elevated threat of errors throughout updates, and better operational complexity.
Past the challenges confronted by the group when misconfigurations are current, misconfigurations are sometimes difficult for builders to troubleshoot. Figuring out the basis reason behind misconfigurations can grow to be more and more time-consuming and complicated if not addressed instantly, and builders don’t at all times know precisely learn how to resolve misconfigurations, which may go away a improvement group annoyed and overwhelmed as they attempt to resolve the problem.
Introducing AI Guided Remediation for IaC / KICS
To make it simpler for improvement groups to deal with the varied kinds of IaC misconfigurations, Checkmarx is happy to introduce AI Guided Remediation for IaC Safety and KICS.
Safety Platform, with KICS (Maintaining Infrastructure as Code Safe) is a free, open supply resolution for static evaluation of IaC information. KICS routinely parses frequent IaC information of any kind to detect insecure configurations that might expose your purposes, knowledge, or companies to assault.evaluation of IaC information. KICS routinely parses frequent IaC information of any kind to detect insecure configurations that might expose your purposes, knowledge, or companies to assault.information. KICS routinely parses frequent IaC information of any kind to detect insecure configurations that might expose your purposes, knowledge, or companies to assault.information. KICS routinely parses frequent IaC information of any kind to detect insecure configurations that might expose your purposes, knowledge, or companies to assault.
Powered by GPT4, AI Guided Remediation offers actionable remediation steps and recommendation to information groups by the method of remediating IaC misconfigurations recognized by Checkmarx IaC Safety and KICS. This helps organizations handle points of their IaC information and deploy their purposes quicker and safer.
IaC Safety and AI Guided Remediation is a strong mixture that makes it quicker and simpler for builders to extra deeply perceive and shortly remediate misconfigurations.
The way it works
Persevering with the Checkmarx promise to make utility safety as straightforward and environment friendly as attainable for builders and AppSec groups, the brand new AI Guided Remediation performance is easy and easy-to-use, all throughout the built-in improvement environments (IDEs) the place improvement groups are spending their time.
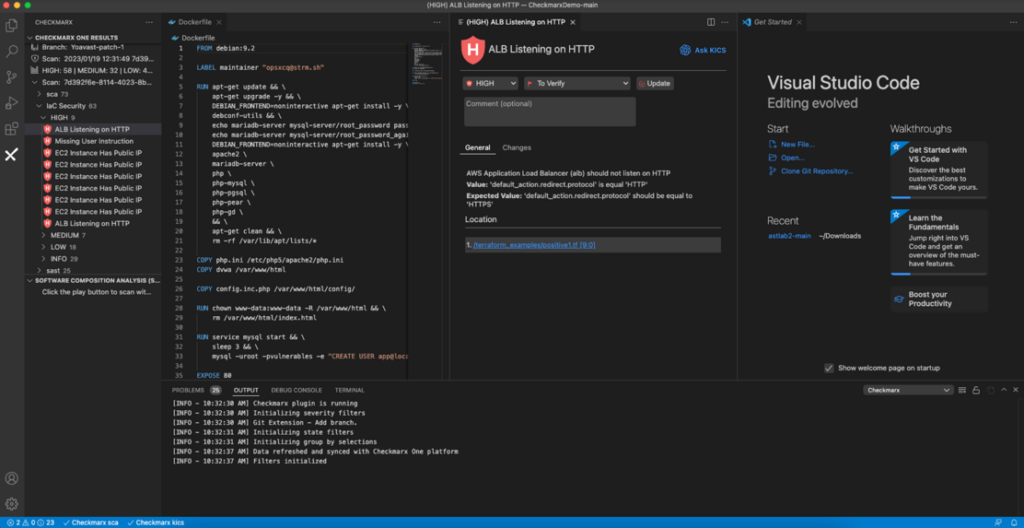
When a given vulnerability is recognized by Checkmarx IaC Safety / KICS, an “Ask KICS” possibility is displayed on display screen. Builders can merely click on on the button to open a panel, the place they’ve a few choices.
Builders can first choose from frequent questions, with out-of-the-box prompts displayed on-screen.
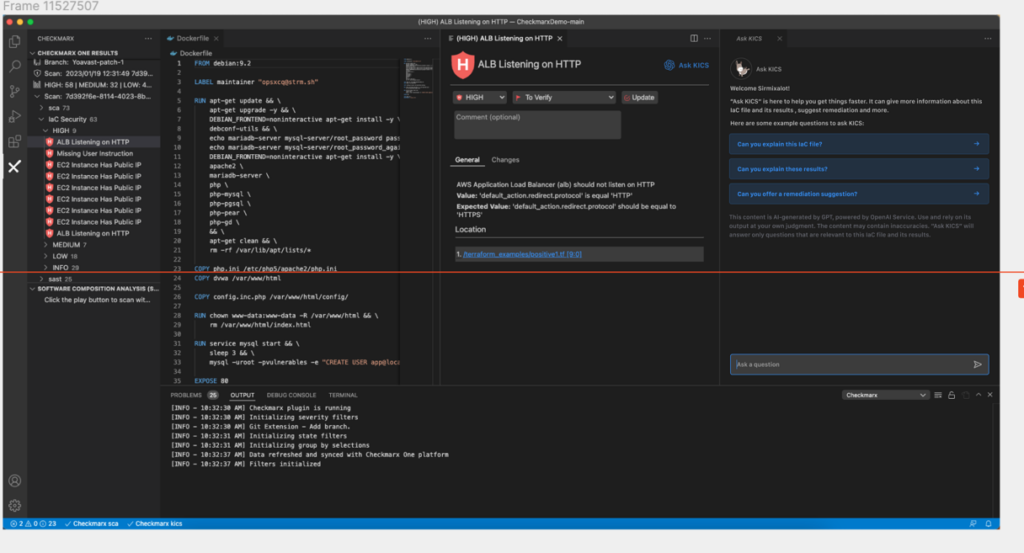
Alternatively, customers can use the free-text area to ask particular questions.
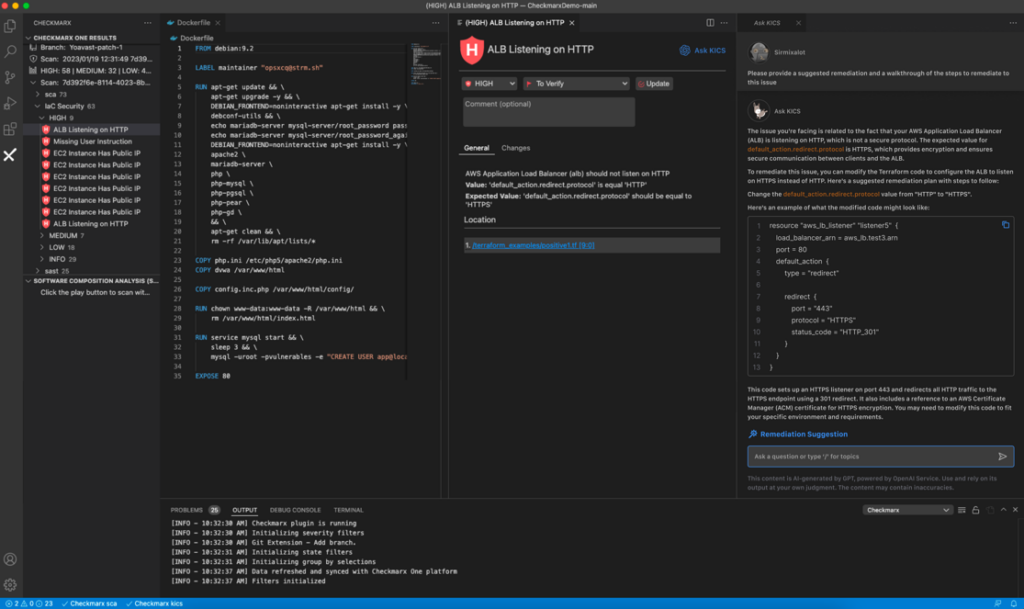
The software will then ship an AI-generated response, giving builders and AppSec managers actionable steps to remediate the misconfiguration.
Offering actionable steps, AI Guided Remediation helps builders higher perceive IaC and API misconfigurations with out extra assets. Builders don’t must know the small print of precisely learn how to remediate all the numerous kinds of misconfigurations; as a substitute, they’ll lean on the ability of AI to shortly harvest the plethora of assets, documentation, and neighborhood data helps improvement groups establish actionable steps to shortly and simply remediate misconfigurations.
With AI Guided Remediation, organizations can handle points of their IaC templates quicker, cut back administration overhead, enhance developer adoption, and ship safer purposes quicker.
Organizations eager to leverage this performance can relaxation assured realizing that their proprietary code is safe. Importantly, the group’s code just isn’t shared with AI tooling.
Moreover, AI Guided Remediation detects and removes secrets and techniques earlier than sending the code to the chat. Secrets and techniques, corresponding to API keys, database passwords, or encryption keys, are delicate items of knowledge that ought to by no means be uncovered or shared inadvertently. By integrating secret detection and elimination into AI Guided Remediation, organizations can considerably improve the safety of their infrastructure as code (IaC) and shield in opposition to unauthorized entry or misuse
For Checkmarx customers that wish to discover Checkmarx IaC Safety / KICS, the addition of AI Guided remediation offers an thrilling new alternative to simply evaluation and motion vulnerabilities recognized by Checkmarx IaC Safety / KICS, all throughout the Checkmarx One™ Utility Safety Platform.
It’s straightforward to get began
For current Checkmarx IaC / KICS customers who wish to discover the ability of AI Guided Remediation, particularly to see the way it can create a greater developer expertise, the Checkmarx AI early entry program is now obtainable.
Enroll now to be among the many first to leverage AI Guided Remediation for IaC Safety / KICS.
Not already utilizing Checkmarx IaC or KICS? Current Checkmarx SAST customers who wish to discover the ability of leveraging Checkmarx IaC / KICS and the AI Guided remediation are inspired to study extra about all the powerfully easy AI-driven options obtainable throughout the Checkmarx One™ Utility Safety Platform, the trade’s most complete platform for lowering threat inside at present’s complicated, cloud-native purposes.
Contact your Checkmarx account supervisor, or contact Checkmarx at present.