The most recent generations of Intel processors, together with Xeon chips, and AMD’s older microarchitectures on Linux are weak to new speculative execution assaults that bypass present ‘Spectre’ mitigations.
The vulnerabilities influence Intel’s twelfth, thirteenth, and 14th chip generations for customers and the fifth and sixth era of Xeon processors for servers, together with AMD’s Zen 1, Zen 1+, and Zen 2 processors.
The assaults undermine the Oblique Department Predictor Barrier (IBPB) on x86 processors, a core protection mechanism in opposition to speculative execution assaults.
Speculative execution is a efficiency optimization function on trendy CPUs that executes directions earlier than realizing if they’re wanted by future duties, thus dashing up the method when the prediction is right. Directions executed primarily based on the misprediction are known as transient and are squashed.
This mechanism has been a supply of side-channel dangers, resembling Spectre, as a result of the hypothesis course of calls delicate information that might be retrieved from the CPU cache.
New Spectre-like assaults
ETH Zurich researchers Johannes Wikner and Kaveh Razavi clarify that regardless of the multi-year mitigation effort to include Spectre-like assaults, there have been quite a few variants that bypass present defenses.
Their contribution is a cross-process assault (on Intel) and PB-inception assault (on AMD) that permits hijacking speculative return targets even after IBPB has been utilized, thus bypassing present protections and leaking delicate info.
Within the first case, the assault exploits a flaw in Intel’s microcode the place the IBPB doesn’t totally invalidate return predictions after a context change.
The attacker manipulates the speculative execution of return directions, permitting stale predictions to leak delicate info, just like the hash of the basis password, from a suid course of.
On AMD processors, IBPB-on-entry within the Linux kernel is wrongly utilized, permitting the return predictor to retain stale predictions even after IBPB.
The attacker mistrains the return predictor earlier than IBPB is triggered, hijacking it to leak privileged kernel reminiscence after the barrier.
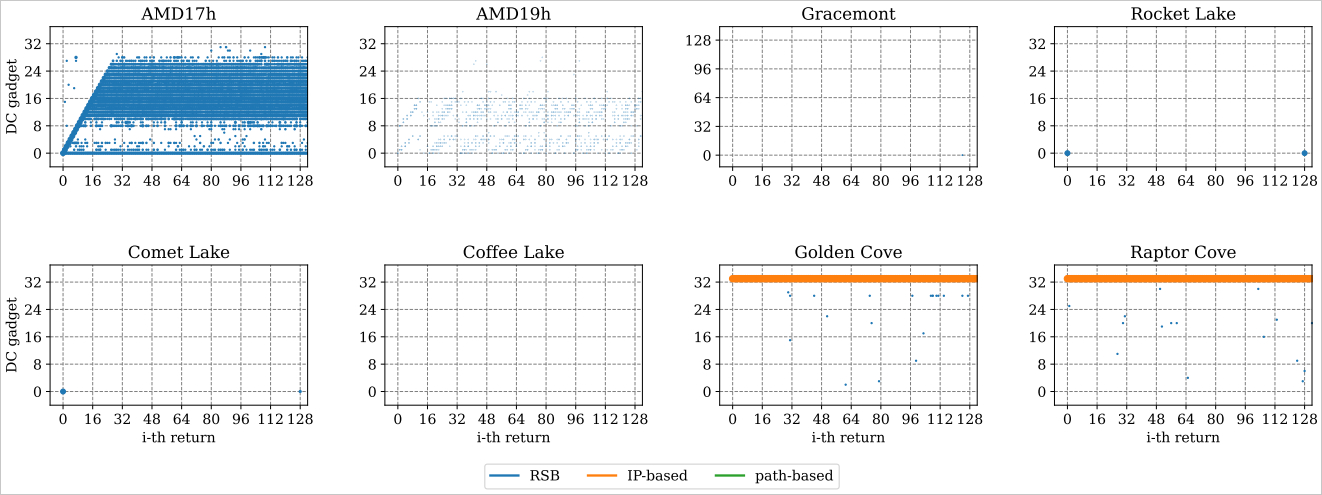
Supply: ETH Zurich
Response and mitigations
The researchers knowledgeable each Intel and AMD of those points in June 2024.
Intel responded saying that they’d already found the difficulty internally and assigned it the CVE-2023-38575 identifier.
The corporate launched in March a microcode repair obtainable by a firmware replace however the researchers notice that the code has not reached all working methods, Ubuntu being amongst them.
AMD additionally confirmed the vulnerability and stated that the flaw had already been documented and tracked as CVE-2022-23824. It’s price noting that AMD’s advisory contains Zen 3 merchandise as beeing affected, which aren’t listed in ETH Zurich’s paper.
Nonetheless, AMD classifies the difficulty as a software program bug, not a {hardware} flaw. The older architectures affected and the truth that AMD discovered in regards to the bug a very long time in the past could clarify the corporate’s choice to not situation corrective microcode.
Though the 2 CPU distributors knew in regards to the Spectre bypass, the businesses marked them within the advisories as having a possible influence. With their work, the ETH Zurich researchers have been capable of reveal that the assault works even on Linux 6.5, which comes with IBPB-on-entry defenses which are thought of the strongest in opposition to Spctre exploitation.
The ETH Zurich staff is working with Linux kernel maintainers to develop a patch for AMD processors, which will likely be obtainable right here when prepared.