Infostealer malware builders launched updates claiming to bypass Google Chrome’s just lately launched function App-Certain Encryption to guard delicate knowledge reminiscent of cookies.
App-Certain Encryption was launched in Chrome 127 and is designed to encrypt cookies and saved passwords utilizing a Home windows service that runs with system privileges.
This mannequin doesn’t enable infostealer malware, which runs with the permissions of the logged person, to steal secrets and techniques saved in Chrome browser.
To bypass this safety, the malware would want system privileges or to inject code into Chrome, each noisy actions which are more likely to set off warnings from safety instruments, mentioned Will Harris of the Chrome safety crew.
Nevertheless, safety researchers g0njxa and likewise RussianPanda9xx obseerved a number of infostealer builders boasting that they’ve carried out a working bypass for his or her instruments (MeduzaStealer, Whitesnake, Lumma Stealer, Lumar (PovertyStealer), Vidar Stealer, StealC).
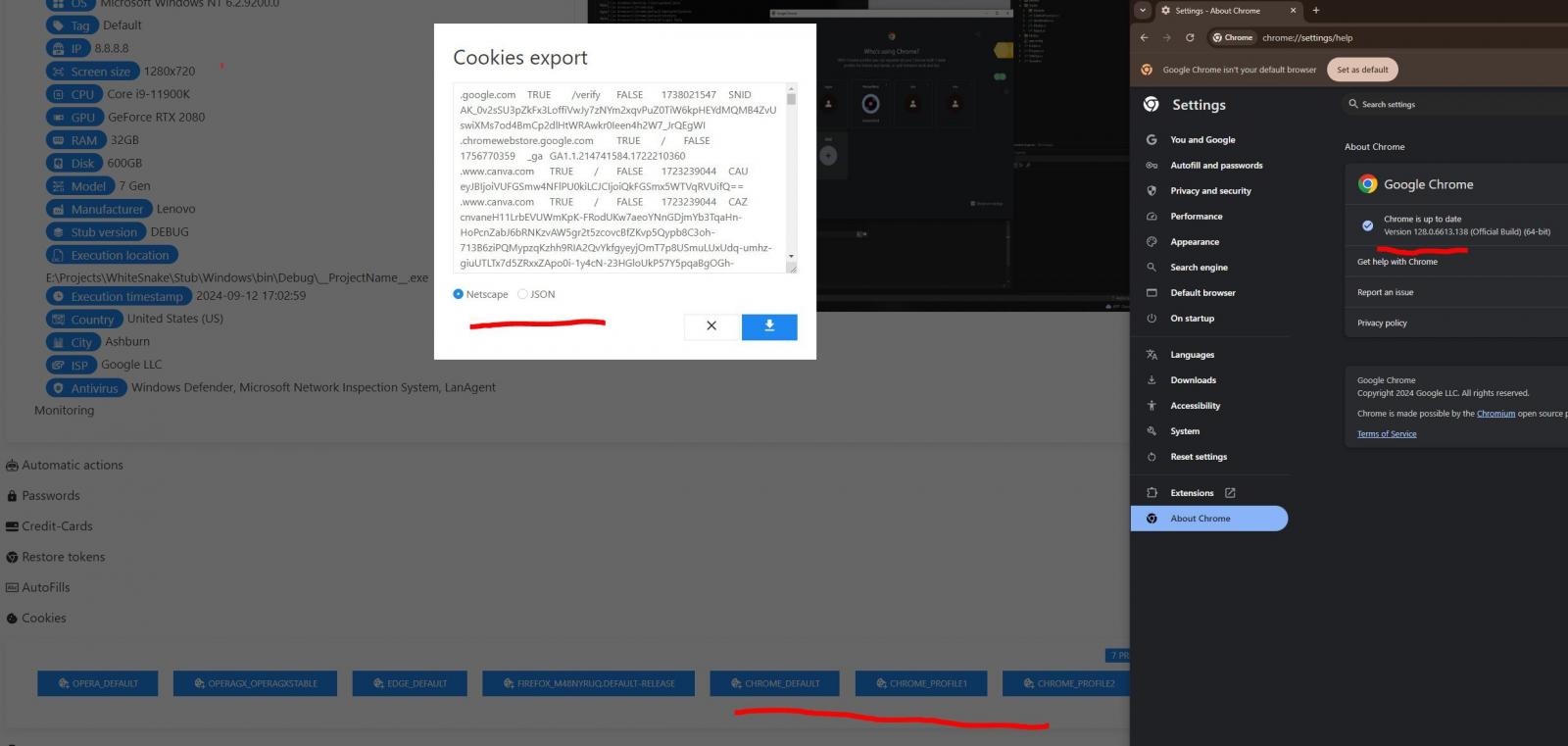
Supply: @g0njxa
It seems that at the very least among the claims are actual, as g0njxa confirmed for BleepingComputer that the most recent variant of Lumma Stealer can bypass the encryption function in Chrome 129, the presently the latest model of the browser.
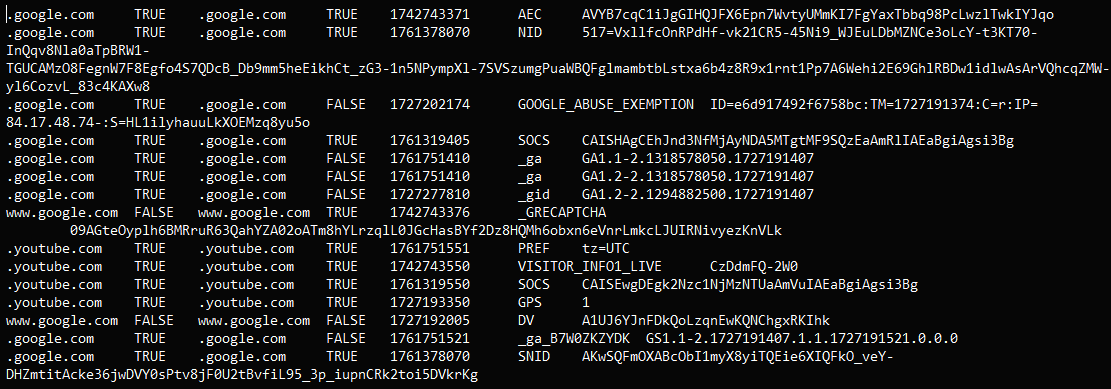
Supply: @g0njxa
The researcher examined the malware on a Home windows 10 Professional system in a sandbox atmosphere.
By way of timing, Meduza, and WhiteSnake carried out their bypassing mechanisms over two weeks in the past, Lumma final week, and Vidar and StealC this week.
Lumar initially responded to App-Certain Encryption by implementing a momentary resolution that required launching the malware with admin rights, however adopted with a bypass mechanism that works with the privileges of the logged-in person.
The builders of Lumma Stealer assured its buyer that they do not must execute the malware with admin privileges for the cookie theft to work.
“Added a new method of collecting Chrome cookies. The new method does not require admin rights and/or restart, which simplifies the crypt build and reduces the chances of detection, and thus increase the knock rate.” – builders of Lumma Stealer
How precisely the bypass of App-Certain Encryption is achieved stays undisclosed, however the authors of Rhadamanthys malware commented that it took them 10 minutes to reverse the encryption.
BleepingComputer contacted the tech big for a remark in regards to the malware developer’s response to App-Certain Encryption in Chrome however we’re nonetheless ready for a reply.
