Aftermath of MOVEit vulnerability: Information vigilante ‘Nam3L3ss’ leaks practically 8 million worker data from trade giants like Amazon, 3M, HP, and Delta, exposing cybersecurity flaws throughout main companies.
A “Data Vigilante” utilizing the alias Nam3L3ss has leaked tens of millions of worker data from international trade giants, in reference to the widespread MOVEit vulnerability. To your info, the MOVEit flaw is a safety vulnerability within the MOVEit file switch software program, which many organizations use to share delicate information.
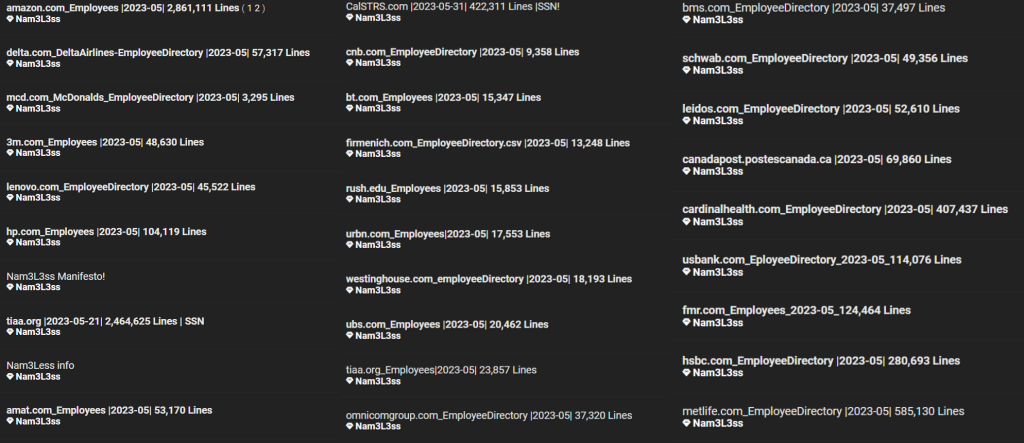
Nam3L3ss, who denies being a hacker, started leaking the information on Friday, November 8, 2024. Up to now, delicate and non-sensitive data from 27 firms, totalling 7,952,414 worker data, have been uncovered. This contains 2,861,111 data from Amazon workers, a breach acknowledged by the corporate.
“Amazon and AWS systems remain secure, and we have not experienced a security event. We were notified about a security event at one of our property management vendors that impacted several of its customers including Amazon,” Amazon spokesperson Adam Montgomery instructed Hackread.com. “The only Amazon information involved was employee work contact information, for example, work email addresses, desk phone numbers, and building locations.”
Information Evaluation
The Hackread.com analysis staff carried out an in-depth evaluation of every file leaked by Nam3L3ss, revealing that the information contains full names, e mail addresses, cellphone numbers, workplace addresses, residential addresses, firm names, location coordinates, and extra.
Listing of Affected Corporations and Worker Counts
3M: 48,630 workers
HP: 104,119 workers
Delta: 57,317 workers
MetLife: 585,130 workers
Amazon: 2,861,111 workers
McDonald's: 3,295 workers
Lenovo: 45,522 workers
TIAA: 2,464,625 workers
CalSTRS: 422,311 workers
BT: 15,347 workers
URBN: 17,553 workers
Leidos: 52,610 workers
UBS: 20,462 workers
HSBC: 280,693 workers
Firmenich: 13,248 workers
U.S. Financial institution: 114,076 workers
Canada Submit: 69,860 workers
Westinghouse: 18,193 workers
Rush College: 15,853 workers
Omnicom Group: 37,320 workers
Charles Schwab: 49,356 workers
Metropolis Nationwide Financial institution: 9,358 workers
Utilized Supplies: 53,170 workers
Cardinal Well being: 407,437 workers
Bristol-Myers Squibb: 37,497 workers
TIAA (extra itemizing): 23,857 workers
Constancy Investments: 124,464 workersNam3L3ss’s Manifesto: Motivation and Methodology
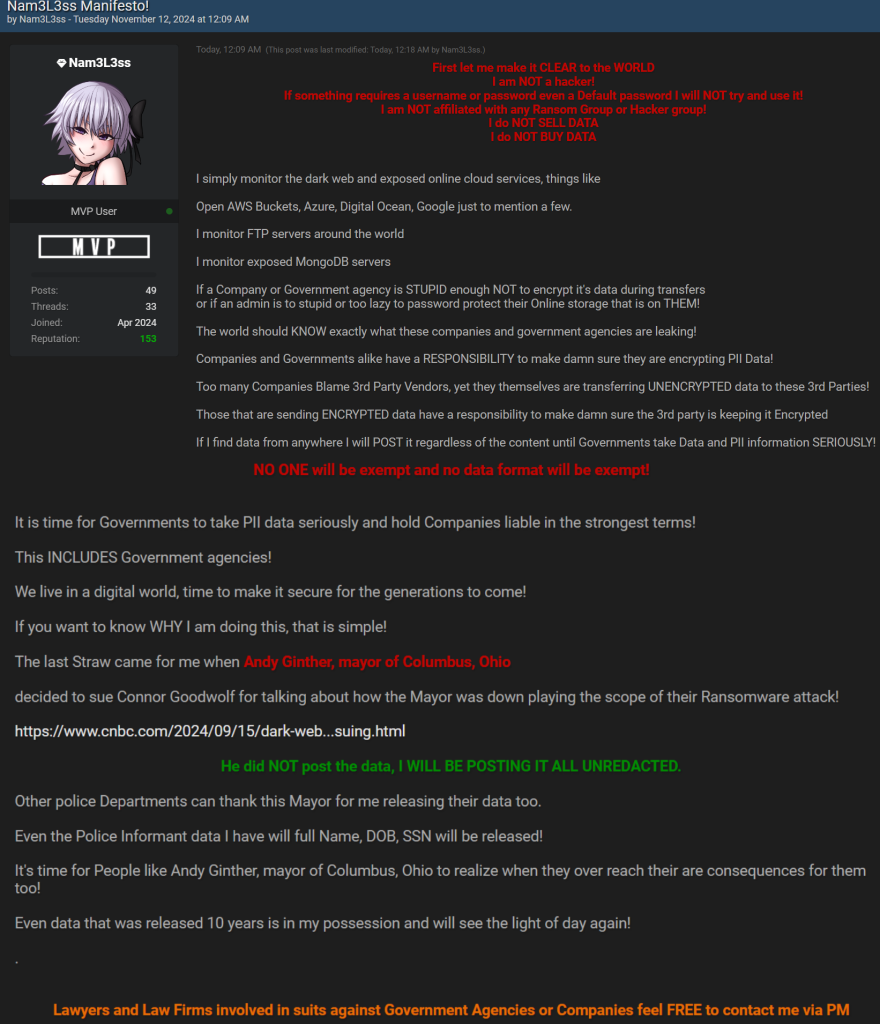
In a submit on Breach Boards, Nam3L3ss outlined their “manifesto” to clarify who they’re and why they’re leaking information. Based on the submit, they monitor misconfigured and unsecured cloud databases throughout varied providers, together with AWS Buckets, Azure, Digital Ocean, Google, and FTP and MongoDB servers, to extract and make this information public.
Nam3L3ss additionally claims to observe ransomware teams, analyze stolen information, clear it by eradicating duplicates and irrelevant info, after which launch it on-line. For instance, the leaked MetLife worker listing originated from MetLife, a world monetary providers agency that suffered a ransomware assault in 2023.
The Cl0p ransomware gang exploited MOVEit extensively, focusing on a whole bunch of organizations worldwide. They even created clear internet web sites to leak the stolen information in July 2024.
Ferhat Dikbiyik, chief analysis and intelligence officer at Black Kite, weighed in on the latest Amazon information breach, explaining, that Amazon’s latest information breach traced again to a third-party vendor’s use of the MOVEit instrument, is one other wake-up name for the availability chain’s hidden vulnerabilities.
“Amazon’s recent data breach traced back to a third-party vendor’s use of the MOVEit tool, is another wake-up call for the supply chain’s hidden vulnerabilities. The MOVEit flaw initially hit hundreds, but the shockwave extended across 2,700+ organizations as the ripple effects reached third and even fourth-party vendors,” Ferhat mentioned.
“We’ve identified over 600 MOVEit servers that were likely caught in this “spray” assault—leaving an enormous discipline of potential targets,” he defined. “CL0P ransomware, the group exploiting this flaw, named 270 victims within three months, and the count is still rising.”
“With 200 to 400 organizations speculated to have paid ransoms, the real impact stretches far beyond these numbers. This breach emphasizes that ransomware risk doesn’t stop at your company’s doorstep. In today’s ecosystem, exposure management must extend across the entire supply chain to truly defend against the next big attack.”
Information Vigilante?
Though the time period Information Vigilante is debatable, Nam3L3ss expresses frustration with firms and authorities establishments for failing to safe their networks. By leaking this information, they purpose to lift consciousness about information safety and encourage higher cybersecurity practices.
Implications of the Information Leak and Recommendation to Workers
Though passwords and monetary particulars weren’t included within the leaked information, the publicity poses important dangers to firms and workers. Risk actors, particularly state-sponsored teams like North Korea’s Lazarus Group, are recognized to take advantage of such information to provoke phishing scams, steal cryptocurrency, and entry monetary info that might support their nation’s financial system.
If you happen to work for one of many affected firms, be looking out for phishing scams through e mail, SMS phishing (smishing), and voice phishing (vishing) makes an attempt, as attackers could attempt to exploit this information for additional scams.
RELATED TOPICS
- Hacker Leaks Hundreds of Microsoft and Nokia Worker Particulars
- Hackers Calling Workers to Steal VPN Credentials from US Companies
- Hacker Leaks Information of 33K Accenture Workers in Third-Get together Breach
- Shadow IT: Private GitHub Repos Expose Worker Cloud Secrets and techniques
- Indian Ex-Worker Jailed for Wiping 180 Digital Servers in Singapore