A cybercriminal utilizing the identify “salfetka” claims to be promoting the supply code of INC Ransom, a ransomware-as-a-service (RaaS) operation launched in August 2023.
INC has beforehand focused the U.S. division of Xerox Enterprise Options (XBS), Yamaha Motor Philippines, and, extra just lately, Scotland’s Nationwide Well being Service (NHS).
Concurrently with the alleged sale, the INC Ransom operation is present process adjustments that may recommend a rift between its core staff members or plans to maneuver to a brand new chapter that may contain utilizing a brand new encryptor.
Supply code sale
The risk actor introduced the sale of each the Home windows and Linux/ESXi variations of INC on the Exploit and XSS hacking boards, asking for $300,000 and limiting the variety of potential consumers to only three.
Based on info offered to BleepingComputer by risk intelligence specialists at KELA, who noticed the sale, the technical particulars talked about within the discussion board submit, akin to using AES-128 in CTR mode and Curve25519 Donna algorithms, align with public evaluation of INC Ransom samples.
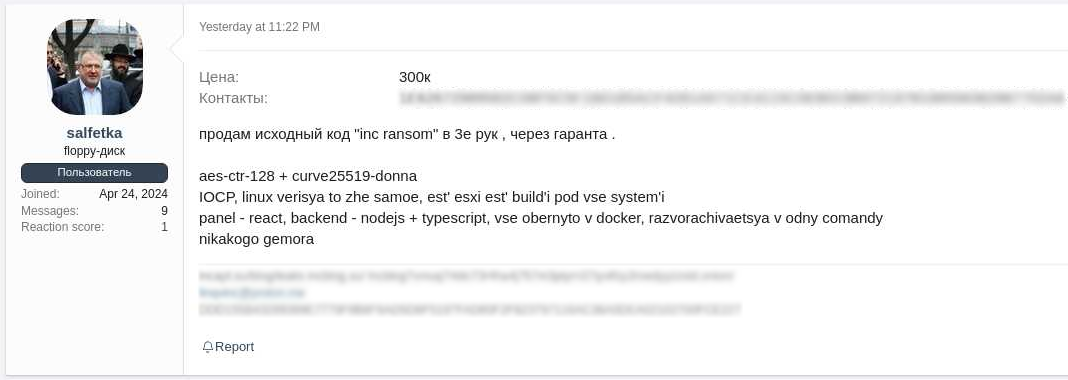
Supply: KELA
KELA additionally informed BleepingComputer that “salfetka” has been lively on the hacking boards since March 2024. The risk actor was beforehand seeking to purchase community entry for as much as $7,000 and provided a minimize to preliminary entry brokers from ransomware assault proceeds.
One other level that provides legitimacy to the sale is “salfetka” together with each the previous and new INC Ransom web page URLs on their signature, indicating they are affiliated with the ransomware operation.
Nonetheless, the sale may very well be a rip-off, with the risk actor rigorously curating the “salfetka” account over the previous few months, declaring curiosity in shopping for community entry, and setting a excessive price ticket to make the provide appear legit.
At the moment, there aren’t any public bulletins on INC’s previous or new web site about promoting the venture’s supply code.
INC Ransom shifting to a brand new web site
On Might 1, 2024, INC Ransom introduced on its previous leak web site that it could transfer to a brand new information leak extortion “blog” and shared a brand new TOR tackle, stating the previous web site could be closed in two to 3 months.
.png)
Supply: BleepingComputer
The brand new web site is already up, and there is some overlap on the victims lists with the previous portal, and twelve new victims not seen on the previous web site.
In complete, the brand new web site lists 64 victims (12 new), whereas the previous has 91 posts, so roughly half of INC’s previous victims are lacking.
“The discrepancies between the two sites may suggest that an operation may have experienced a leadership change or splitting into different groups,” commented KELA’s analysts.
“However, the fact that “salfetka” has referenced both sites as his alleged projects suggests the actor is not related to just one part of the operation.”
“In this case, it is possible that the new blog was created in an attempt to gain more profits from the sale.”
It is usually value noting that INC’s new extortion web page design visually resembles that of Hunters Worldwide, which may point out a reference to the opposite RaaS operation.
Supply: BleepingComputer
Versus a public leak that permits safety analysts to crack the encryption of a ransomware pressure, non-public supply code gross sales of strains for which there is not any out there decryptor have the potential to create extra bother for organizations worldwide.
These ransomware builders are purchased by extremely motivated risk actors simply getting into the area or semi-established teams seeking to up their sport utilizing a extra strong and well-tested encryptor.
That’s very true when a Linux/ESXi model is on provide, which is usually more difficult to develop and costlier to amass.
When ransomware gangs rebrand, they generally reuse a lot of the supply code from their previous encryptors, permitting researchers to hyperlink older gangs to new operations.
Utilizing different ransomware operation’s encryptors may also assist rebrand because it muddies the path for legislation enforcement and researchers.
