Picture: Midjourney
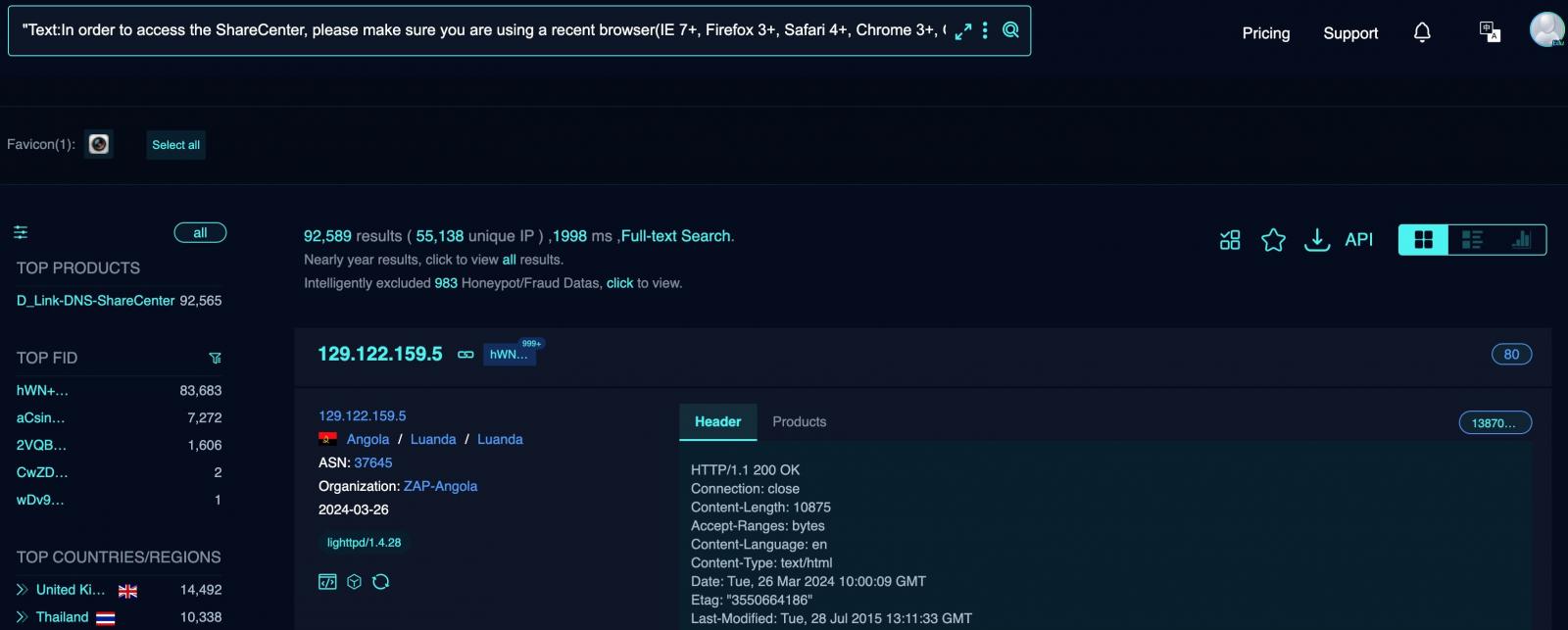
Attackers at the moment are actively focusing on over 92,000 end-of-life D-Hyperlink Community Connected Storage (NAS) gadgets uncovered on-line and unpatched in opposition to a crucial distant code execution (RCE) zero-day flaw.
As BleepingComputer first reported on Saturday, this safety vulnerability (CVE-2024-3273) is the results of a backdoor facilitated by means of a hardcoded account (username “messagebus” with an empty password) and a command injection situation through the “system” parameter.
Risk actors at the moment are chaining these two safety flaws to deploy a variant of the Mirai malware (skid.x86). Mirai variants are often designed so as to add contaminated gadgets to a botnet that can be utilized in large-scale distributed denial-of-service (DDoS) assaults.
These assaults began on Monday, as noticed by cybersecurity agency GreyNoise and risk monitoring platform ShadowServer. Two weeks earlier, safety researcher Netsecfish disclosed the vulnerability after D-Hyperlink knowledgeable them that these end-of-life gadgets wouldn’t be patched.
“The described vulnerability affects multiple D-Link NAS devices, including models DNS-340L, DNS-320L, DNS-327L, and DNS-325, among others,” Netsecfish explains.
“Successful exploitation of this vulnerability could allow an attacker to execute arbitrary commands on the system, potentially leading to unauthorized access to sensitive information, modification of system configurations, or denial of service conditions.”
When requested whether or not safety updates can be launched to patch this zero-day vulnerability, D-Hyperlink additionally informed BleepingComputer that they not supported these end-of-life (EOL) NAS gadgets.
“All D-Link Network Attached storage has been End of Life and of Service Life for many years [and] the resources associated with these products have ceased their development and are no longer supported,” a D-Linkspokesperson informed BleepingComputer.
“D-Link recommends retiring these products and replacing them with products that receive firmware updates.”
| Mannequin | Finish of Service Life | Fastened Firmware | Conclusion |
| DNS-320L | 05/31/2020: Hyperlink | Not Obtainable | Retire & Substitute |
| DNS-325 | 09/01/2017: Hyperlink | Not Obtainable | Retire & Substitute |
| DNS-327L | 05/31/2020: Hyperlink | Not Obtainable | Retire & Substitute |
| DNS-340L | 07/31/2019: Hyperlink | Not Obtainable | Retire & Substitute |
The spokesperson added that these NAS gadgets don’t have computerized on-line updating or alert supply capabilities, making it inconceivable to inform the house owners of those ongoing assaults.
After the disclosure, D-Hyperlink launched a safety advisory on Thursday to inform house owners concerning the safety vulnerability and advise them to retire or change the affected gadgets as quickly as potential.
It additionally created a assist web page for legacy gadgets, warning house owners to use the newest safety and firmware updates obtainable by means of the legacy assist web site, though that would not defend their gadgets from attackers.
“If US consumers continue to use these devices against D-Link’s recommendation, please make sure the device has the last known firmware,” D-Hyperlink warned.
What D-Hyperlink did not say is that NAS gadgets should not be uncovered on-line since they’re generally focused in ransomware assaults to steal or encrypt knowledge.
In current months, different D-Hyperlink gadgets (a few of them additionally end-of-life) have been focused by a number of Mirai-based DDoS botnets (one among them tracked as IZ1H9). Their house owners are constantly engaged on increasing their capabilities, including new exploits and targets to assault.
