The idea of containerization has modified how purposes are deployed and managed, providing flexibility and scalability. These modifications have made compliance with safety requirements in containerized environments an necessary space of focus.
Sustaining visibility into container hosts, guaranteeing adherence to greatest practices, and conducting vulnerability assessments are some issues in guaranteeing efficient safety.
This text will discover how Wazuh helps implement greatest safety practices for containerized environments.
What are containers? They’re light-weight, transportable models that package deal an software and its dependencies, enabling constant operation throughout totally different computing environments.
Examples of container applied sciences embrace Docker, Kubernetes Pods, LXC, and Home windows containers.
Container safety challenges
The elevated adoption of containerized applied sciences presents challenges stemming from the dynamic nature and scale of containerized workloads. Key points in attaining regulatory compliance for container environments embrace:
- Container visibility: Attaining compliance requires enterprises to have visibility throughout all their workloads, however understanding what container workloads are working, the place they’re working, and the way they’re configured could also be difficult, particularly at massive scale. In some environments, workloads are unfold throughout private and non-private clouds, and pictures might come from a number of sources. These points, together with various configurations, make visibility harder.
- Implementing granular entry controls: Many regulatory requirements require enterprises to implement granular entry controls to forestall unauthorized entry to delicate information or system compromise. For instance, PCI DSS requires enterprises to limit entry to cardholder information in a way that’s in response to the precept of least privilege. Such a requirement solidifies the necessity for compliance even inside containerized environments
- Managing vulnerabilities in exterior libraries and pictures: Container photos pulled from untrusted repositories or third-party libraries and dependencies can introduce vulnerabilities to containerized environments. Enterprises want a plan to mitigate this danger and stay compliant.
Wazuh for container safety
Wazuh is a free, open supply safety platform that gives unified XDR and SIEM capabilities throughout workloads in cloud and on-premises environments. The Wazuh platform affords capabilities like log information evaluation, file integrity monitoring, menace detection, real-time alerting, and incident response.
Wazuh helps to satisfy regulatory compliance necessities like PCI DSS 4.0 necessities 10.2.4 and 10.2.5, and NIST SP 800-190 for Docker containers within the following methods:
- File integrity monitoring (FIM): Wazuh gives FIM to watch the integrity of container photos and different vital information, guaranteeing that unauthorized modifications are promptly detected and reported.
- Configuration auditing: Wazuh audits container host configurations to satisfy compliance requirements, establish misconfigurations, and be sure that safety requirements are adopted.
- Vulnerability scanning: Wazuh integrates with vulnerability evaluation instruments to scan container photos for recognized vulnerabilities, serving to organizations mitigate dangers and keep compliance with safety requirements.
- Log evaluation: Wazuh analyzes container logs for safety occasions and anomalies, enabling organizations to establish threats and take acceptable motion to deal with them.
- Malware detection: Wazuh contains malware detection capabilities, enhancing container safety by figuring out and mitigating threats from malicious software program.
- Lively response: Wazuh gives lively response capabilities to execute actions like firewall blocking or account lockouts in response to safety incidents. Wazuh ensures regulatory compliance by swiftly addressing safety occasions in container hosts and imposing safety controls towards evolving threats.
Monitoring Docker containers
Wazuh facilitates Docker container monitoring by putting in the Wazuh agent on the Docker server and enabling the Wazuh Docker listener. This setup permits for gathering Docker-related logs and safety occasions, guaranteeing efficient container exercise monitoring and incident detection.
Wazuh actively displays the runtime, software logs, and useful resource utilization in containerized environments. Wazuh gives real-time insights into container useful resource consumption, for example, when container CPU and reminiscence utilization exceeds predefined thresholds.
This complete monitoring with Wazuh allows immediate problem decision, enhances safety, and optimizes operational effectivity in Docker environments.
The picture under exhibits when Wazuh detects Docker CPU and reminiscence utilization exceeding the outlined threshold, as seen on the Wazuh dashboard.
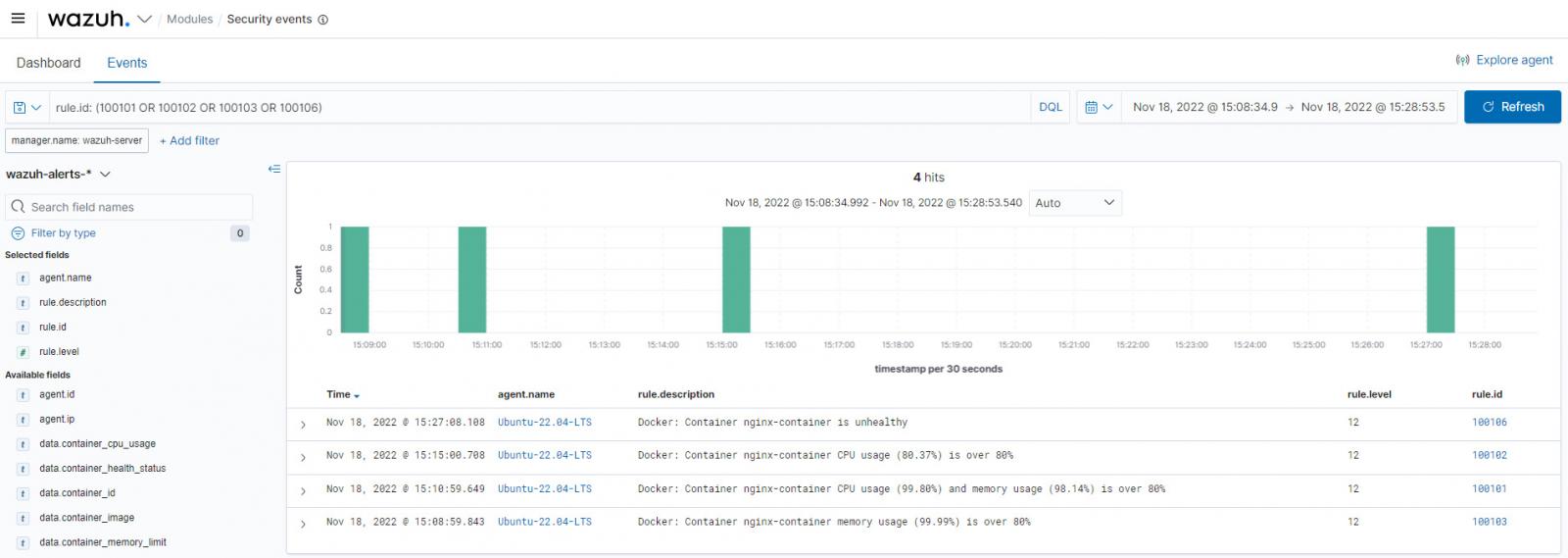
Auditing Kubernetes
Wazuh displays Kubernetes utilizing a webhook listener arrange on the Wazuh server to obtain logs from the Kubernetes cluster. Auditing Kubernetes with Wazuh ensures real-time monitoring, storage, and indexing of Kubernetes audit logs.
This gives information search and analytics capabilities for detecting safety threats.
The picture under exhibits alerts triggered when sources had been created and deleted on a Kubernetes cluster monitored by Wazuh.
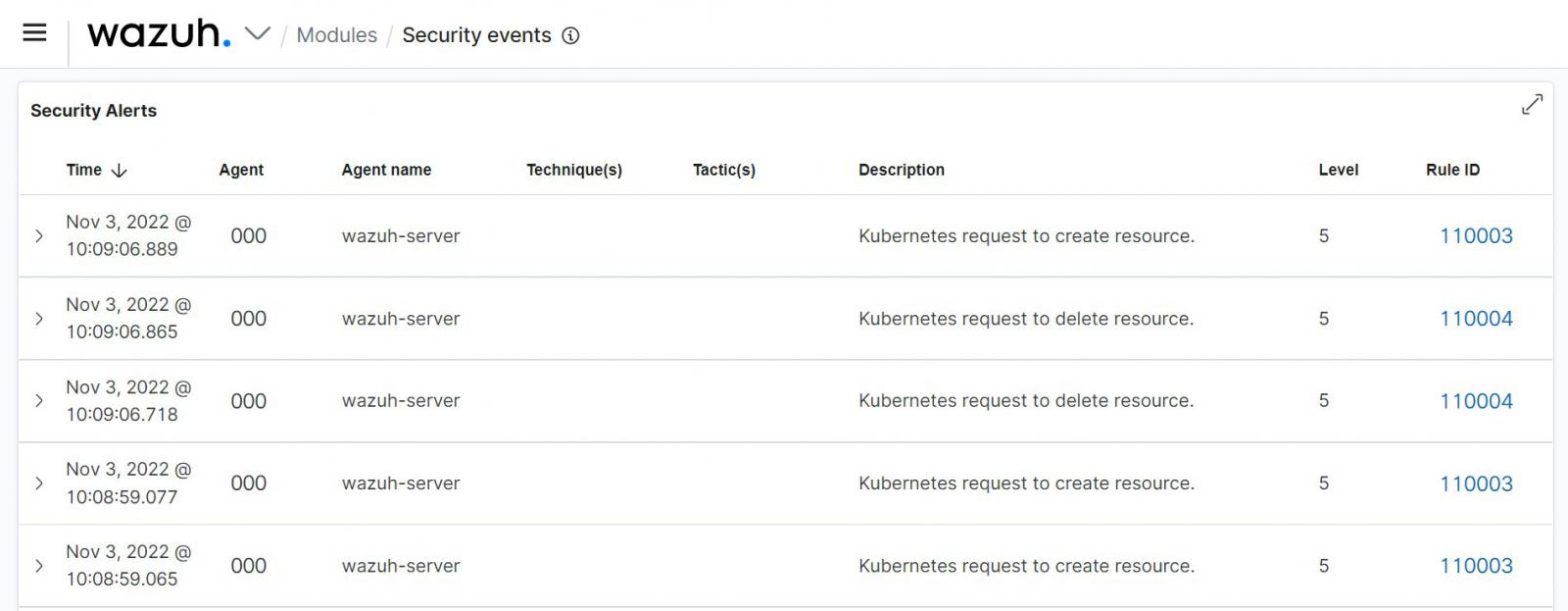
Container vulnerability scanning
Wazuh allows container vulnerability scanning by integrating with a vulnerability evaluation software to conduct scans inside container environments. This course of contains executing customized bash scripts through the Wazuh command functionality to set off the vulnerability evaluation instruments for scans.
Customized guidelines are configured on the Wazuh server to watch the end result of the scan carried out on the endpoint.
The Wazuh agent displays and forwards the vulnerability scan logs to the Wazuh server, enabling organizations to promptly establish and remediate vulnerabilities inside their container environments.
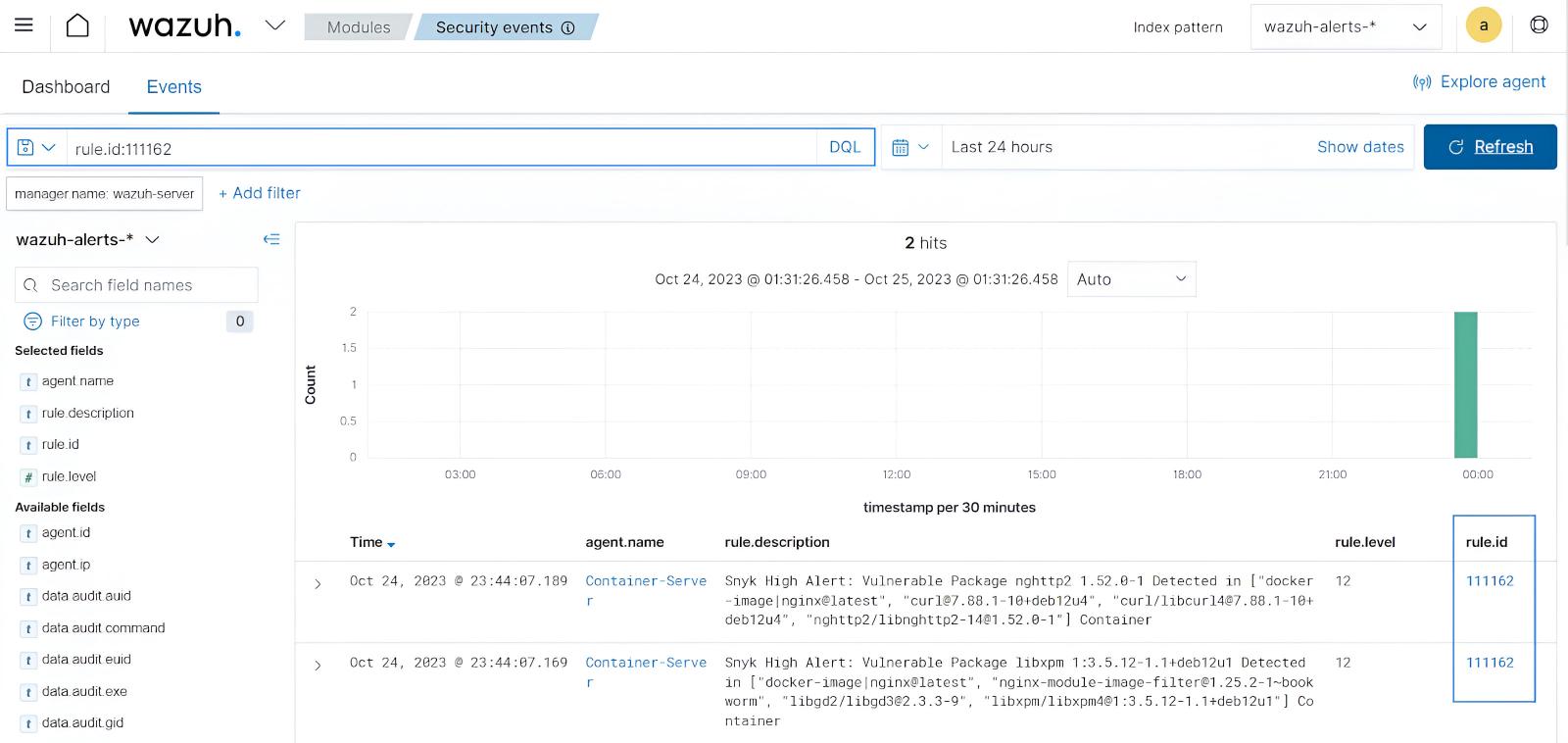
Conclusion
Sustaining safety compliance is necessary for mitigating dangers and guaranteeing greatest practices inside containerized environments.
Wazuh aids this effort by offering visibility into container safety, menace detection and response, and insights into numerous requirements and frameworks.
Wazuh is an open supply and easy-to-deploy resolution that simplifies regulatory compliance, making it a necessary asset for organizations striving to take care of a safe and compliant setting.
Compliance with container greatest practices is a shared accountability, and Wazuh streamlines the method, guaranteeing companies keep protected and resilient.
Be part of the Wazuh group to get began.
Sponsored and written by Wazuh.
