93% of final yr’s information breaches started with compromised credentials. Earlier than the cloud, safety perimeters have been outlined by bodily partitions and community boundaries, however within the cloud, that perimeter has all however dissolved.
Think about what occurred in November 2023, when a cloud observability vendor discovered proof of unauthorized entry to its staging atmosphere — an atmosphere that housed buyer information and PII. Throughout the course of the investigation, it was found that the attacker used stolen credentials in reference to a single worker’s account that gave them entry and the power to escalate privileges.
Sadly, such examples are a lot. Attackers’ modus operandi will fluctuate, however all of them depend on consumer or machine credentials to some extent — acquiring entry to cloud purposes or companies, after which elevating their permissions or privileges to exfiltrate information.
Assaults involving misused or exploited identities can price organizations thousands and thousands of {dollars}. When attackers get previous your proactive safety defenses, you will need to discover and cease them earlier than they get too deep. To that finish, Sysdig has prioritized id safety by means of bulletins, like Cloud Id Insights, and partnerships, like that with Netskope.
Netskope is a worldwide safe entry service edge (SASE) chief that enhances clients’ preventive and reactive id safety with cross-domain id administration. With Sysdig and Netskope, safety groups can reduce overly permissive and dangerous customers, and work extra effectively. Compliance is simplified with automated prevention.
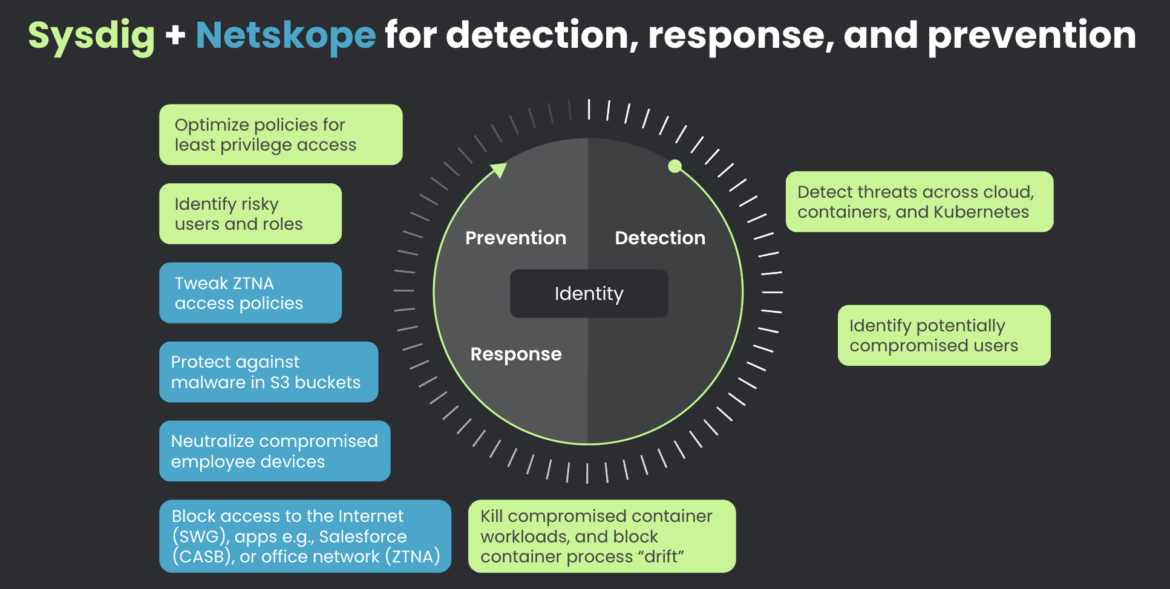
Sysdig detects, Netskope blocks
Safety groups want to care in regards to the cloud, no matter whether or not or not their group is cloud-first, cloud-native, or cloud-last; by means of trendy provide chains, each group touches the cloud in a technique or one other. This requirement is amplified by the elevated variety of lateral motion assaults from and to the cloud. Attackers can transfer throughout machines within the cloud, decoupling id habits from workload exercise and making it tough to reconstruct the complete historical past of an assault even after preliminary detection. The explosion of non-human/machine identities provides much more complexity, as cloud infrastructure has expanded to embody an unlimited array of identities and roles.
Leveraging runtime insights to your cloud environments is the most effective protection for the cloud, regardless of how your group units up the cloud — public, non-public, on-prem, or hybrid. The Sysdig and Netskope partnership improves visibility throughout networks, clouds, and edge, accelerating risk detection and response to cease assaults in actual time. It’s as straightforward as making a webhook in Sysdig to ahead safety occasion alerts and customizing real-time block/limit guidelines in Netskope.
By this partnership, Sysdig is extending the facility of Netskope to the cloud to reinforce identity-infused cloud detection and response (CDR) and likewise comprise the breaches that transfer past the cloud:
- Forestall breaches from occurring with the power to tweak a number of zero belief community entry (ZTNA) insurance policies, letting you optimize your Least Permissive Coverage. 98% of permissions granted go unused, however you are able to do higher.
- Defend workers from utilizing malware-laden S3 buckets or contaminated cloud belongings.
- Detect doubtlessly compromised customers and non-human identities in seconds.
- Reply quicker to dangerous customers and roles by monitoring and neutralizing compromised worker gadgets.
- Include the risk and compromised consumer by blocking entry to the web, purposes, or enterprise networks.
Actual-life use case
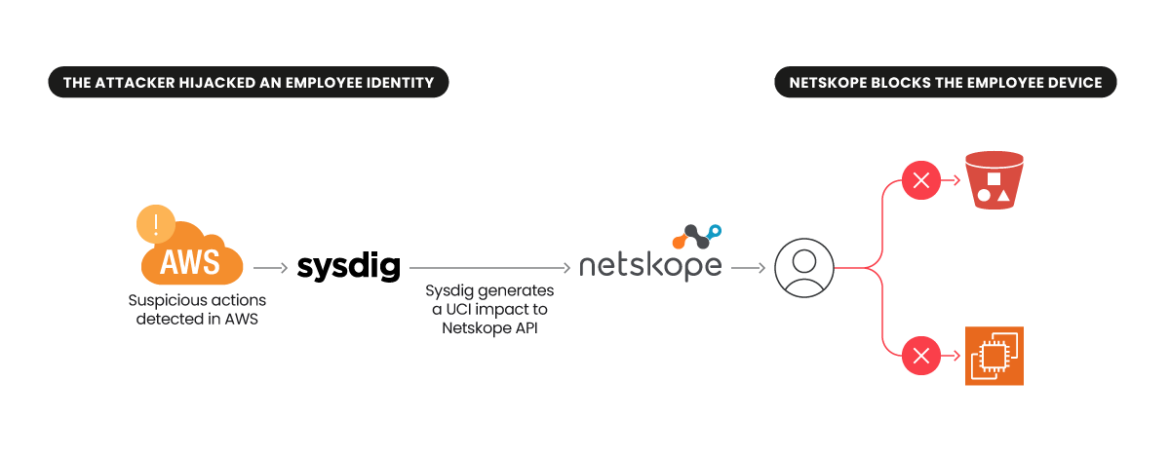
The story:
A malicious actor obtains entry to an organization’s AWS console by means of a stolen id bought on the Darkish Internet. The id belongs to a developer or community administrator who wants entry to AWS for day-to-day actions. The actor, like many, is acutely aware of evading detection, and subsequently navigates to CloudTrail logs and deletes their logged actions, erasing proof of preliminary entry.
- In Sysdig, a “CloudTrail Trail Deleted” occasion is taken into account excessive severity. The occasion context contains the account, area, consumer, danger tags, and extra.
- By the partnership integration, the occasion particulars are mechanically translated into Netskope’s consumer confidence index (UCI) primarily based on the occasion kind, severity, danger ranking, and a mix of what Netskope already is aware of in regards to the consumer’s prior habits, together with what Sysdig is aware of in regards to the consumer’s machine danger.
- Netskope maintains and tracks all customers’ UCI scores inside the consumer and entity habits analytics (UEBA) dashboard. After receiving a Sysdig alert, the consumer’s UCI rating is up to date (it decreases) within the Netskope UEBA.
- Anomalous consumer behaviors immediate a Netskope non-compliance motion popup on the consumer’s enterprise machine by which the consumer should justify their actions or report a false constructive. This response and correlated incident data is shipped to the group’s Netskope directors for evaluate.
- Sysdig helps/permits investigations by monitoring the actor’s behaviors and motion, together with the deleted CloudTrail logs. Within the case of a false constructive, Netskope directors can restore the UCI.
- Following an investigation, safety groups can tag an id as “compromised” in Sysdig and embrace it in blocklists. Going ahead, this triggers automated restrictions primarily based on the predetermined parameters.
Conclusion
This integration will increase the scope of the preventive actions clients can take past the cloud. When Sysdig detects suspicious exercise within the cloud, you’ll be able to block the related identities and roles past the cloud using Netskope. This proactively protects the organizational community, edge gadgets, and any SaaS purposes that the account had been given entry to up to now.
Visibility restrictions now not exist as a result of Sysdig and Netskope mean you can observe an id’s lifecycle throughout bodily or community gadgets and the cloud. With the recognized scale and velocity of cloud assaults, this integration permits safety groups to answer potential threats in minutes, tremendously decreasing an attacker’s alternative to inflict ache.