A brand new report from IBM X-Drive exposes modifications within the Grandoreiro malware panorama. The banking trojan is now able to focusing on greater than 1,500 world banks in additional than 60 nations, and it has been up to date with new options.
Additionally, Grandoreiro’s focusing on has change into wider, because it initially solely focused Spanish-speaking nations, whereas current assault campaigns focused nations in Europe, Asia and Africa. As well as, the malware is now sending phishing emails instantly from the sufferer’s Microsoft Outlook native consumer to recipients’ e mail addresses discovered within the native system.
What’s Grandoreiro?
In accordance with Interpol, the Grandoreiro banking trojan has been a significant risk throughout Spanish-speaking nations since 2017. The malware’s fundamental functionalities permit cybercriminals to regulate gadgets on the contaminated laptop, allow keylogging, deal with home windows and processes, open a browser and execute JavaScript inside it, add or obtain recordsdata, and ship emails, along with its banking trojan capabilities.
Evaluation of various assault campaigns reveals that many operators are concerned in Grandoreiro assaults, as acknowledged by cybersecurity firm Kaspersky, which wrote in July 2020, “It is still not possible to link this malware to any specific cybercrime group, although it is clear that the campaign is using a MaaS (Malware-as-a-Service) business model.”
SEE: Kaspersky Research: Gadgets Contaminated With Knowledge-Stealing Malware Elevated by 7 Instances Since 2020
Arrests of suspected cybercriminals in relation to Grandoreiro occurred in 2021, with 16 suspects being caught by the Spanish Police on costs of laundering funds stolen via two banking trojans, together with Grandoreiro. Extra not too long ago, Brazilian authorities arrested 5 programmers and directors behind the banking malware, who have been suspected to have defrauded victims of greater than €3.5 million.
But the malware, developed in Brazil, remains to be lively and has began increasing its goal record to different nations, comparable to Japan, Netherlands, Italy and South Africa, as reported within the new analysis from IBM’s X-Drive workforce.
How do Grandoreiro campaigns work?
All Grandoreiro campaigns begin with phishing emails
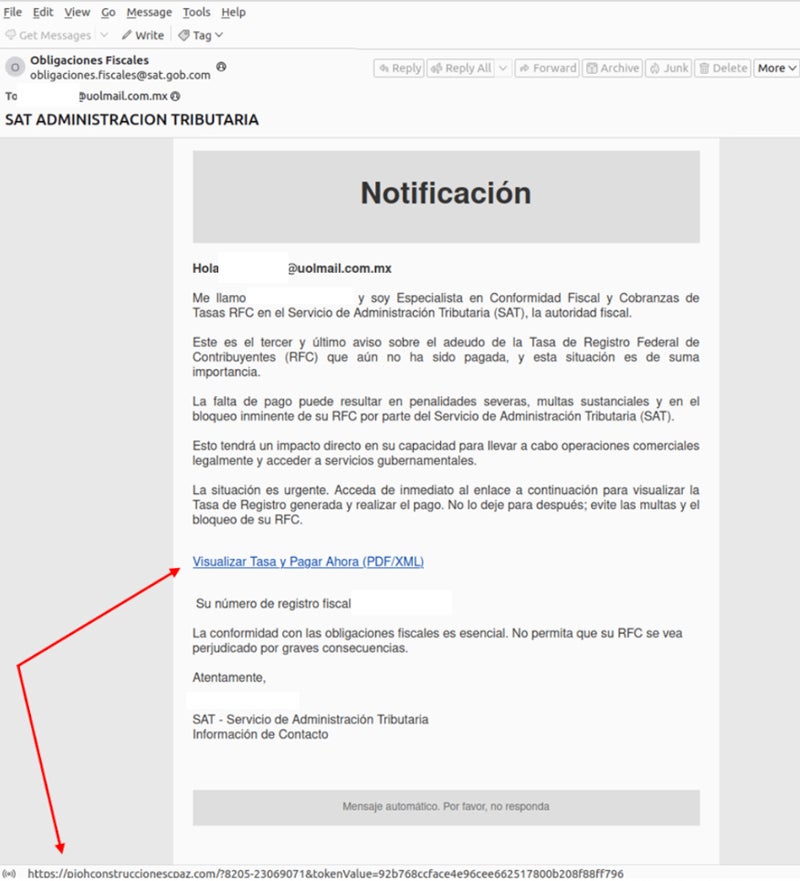
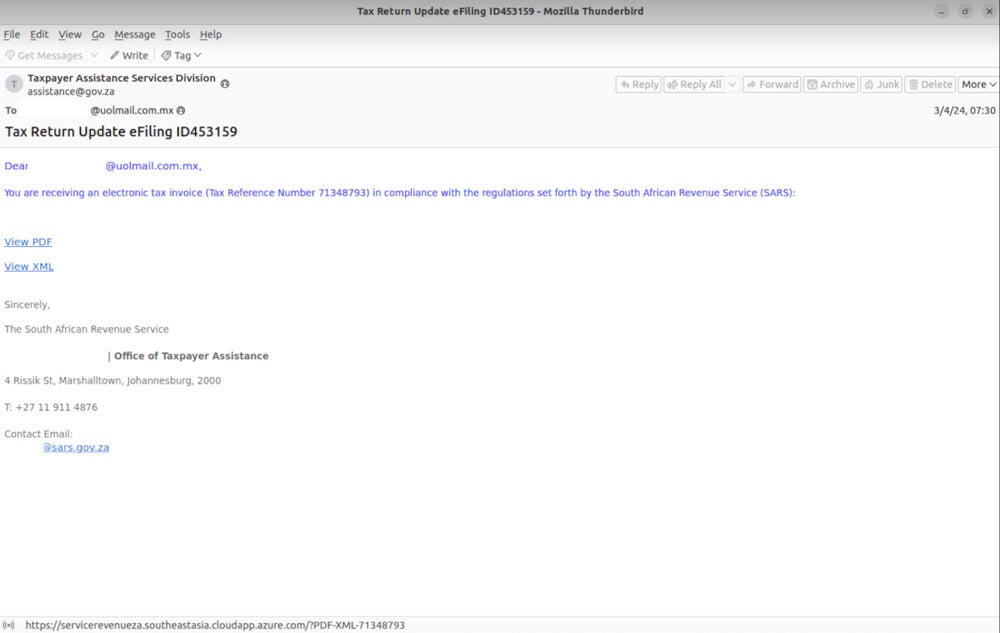
Since March 2024, a number of Grandoreiro phishing campaigns have impersonated entities in Mexico, comparable to Mexico’s Tax Administration Service, Mexico’s Federal Electrical energy Fee or the Income Service of Argentina.
Completely different social engineering methods have been used since March 2024 within the emails to entice the consumer to click on a hyperlink: a remaining discover to pay a debt, a reminder that one can entry their account assertion in PDF or XML format or a reminder to learn particulars on a compliance discover.
In these phishing campaigns, solely customers originating from particular nations — Mexico, Chile, Spain, Costa Rica, Peru, Argentina — are being redirected to a payload when clicking on the hyperlink supplied within the e mail.
Following the current arrests involving Grandoreiro operators, researchers noticed a surge in campaigns focusing on nations past the same old Spanish-speaking ones, together with Japan, the Netherlands, Italy and South Africa, with emails written in English.
Subsequent comes the an infection chain
After the consumer clicks the malicious hyperlink within the phishing e mail, a customized loader is launched, presenting a faux Adobe PDF Reader captcha, which requires a click on to proceed with the execution, most likely to differentiate between actual customers and automatic programs comparable to sandboxes.
Then, the loader collects some sufferer knowledge and sends it to the command&management server utilizing encryption primarily based on AES and base64 algorithms. The information despatched to the C2 consists of the pc and consumer names, the working system model, the antivirus identify, the sufferer’s public IP deal with, and an inventory of operating processes. As well as, the loader checks for the existence of the Microsoft Outlook consumer in addition to crypto wallets and particular banking safety merchandise comparable to IBM Trusteer or Topaz OFD.
The loader might be configured to disallow victims from particular nations primarily based on their IP addresses. One malware pattern discovered by IBM X-Drive stopped if the consumer was situated in Russia, Czech Republic, Poland or Netherlands.
If all circumstances are met, the Grandoreiro banking trojan is downloaded, decrypted by way of an RC4-based algorithm and executed.
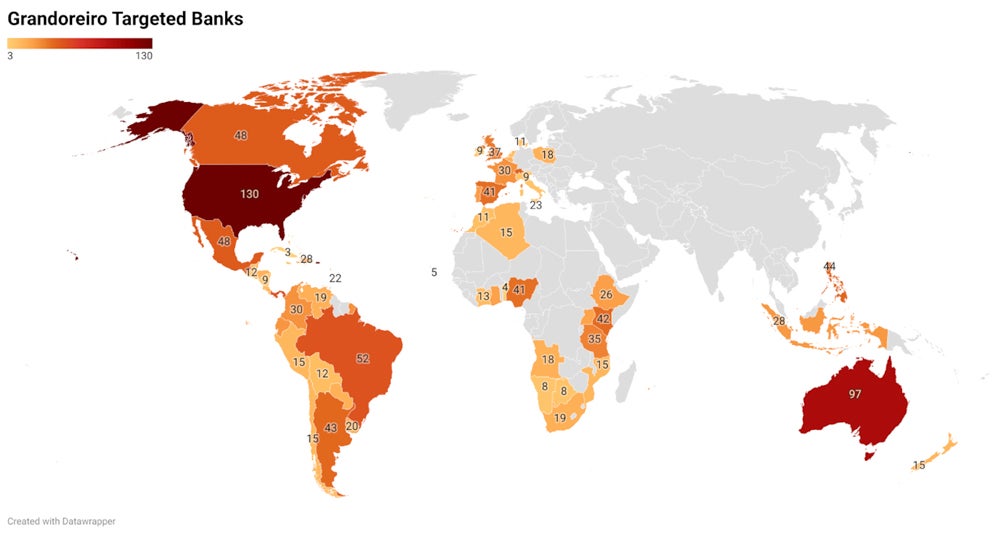
Focusing on greater than 1,500 banks worldwide
Grandoreiro’s record of focused purposes has elevated to greater than 1,500 banks worldwide, in keeping with IBM X-Drive, with financial institution purposes additionally tied to areas. For instance, if the sufferer’s nation is recognized as Belgium, the malware will seek for all focused banking purposes related to the European area.
As well as, 266 distinctive strings are utilized by the malware to establish cryptocurrency wallets.
Current updates in Grandoreiro
New DGA algorithm
Researchers Golo Mühr and Melissa Frydrych analyzed the malware in depth and located the malware, which historically relied on area technology algorithms to seek out its C2 server references, contained a reworked DGA.
The brand new algorithm introduces a number of seeds for its DGA, “used to calculate a different domain for each mode or functionality of the banking trojan, allowing separation of C2 tasks among several operators as part of their Malware-as-a-Service operation” as acknowledged by the researchers.
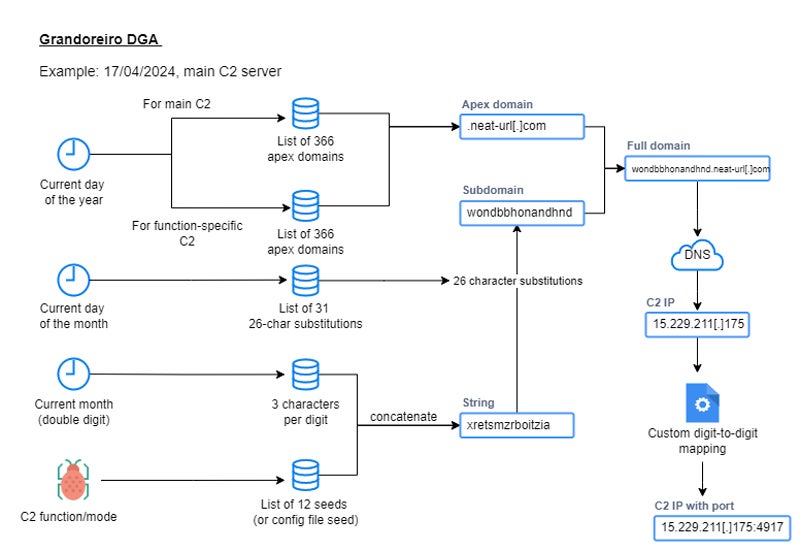
For one analyzed pattern, for a given day, 12 domains could possibly be used as C2 domains, with 4 of them being lively on that day and resulting in Brazilian-based IP addresses.
Microsoft Outlook abuse
Current variations of Grandoreiro abuse the native Microsoft Outlook software program when obtainable on an contaminated laptop.
The malware interacts with the Outlook Safety Supervisor Instrument, a device designed to develop Outlook add-ins. The usage of the device permits the malware to disable alerts inside Outlook earlier than it begins harvesting all sender e mail addresses discovered within the sufferer’s mailbox, filtering the e-mail addresses to keep away from gathering undesirable ones comparable to these containing “noreply,” “feedback” or “newsletter,” to call a number of from the malware’s blocklist.
As well as, the malware scans elements of the sufferer’s folders recursively to hunt for extra e mail addresses, searching for recordsdata with particular extensions, together with .csv, .txt, .xls and .doc.
The malware then begins sending spam primarily based on phishing templates it acquired from its C2 server earlier than deleting all of the despatched emails from the sufferer’s mailbox.
As a way to keep away from being caught by the consumer who may discover suspicious habits from the pc, the malware solely begins sending the emails when the final enter on the machine is no less than 5 minutes previous or longer in some malware variants.
Learn how to defend from this Grandoreiro malware risk
- Do cautious community evaluation. Specifically, a number of consecutive requests to ip-api.com/json should set off alerts and investigations, because it may be an indicator of a Grandoreiro an infection.
- Monitor run keys within the Home windows registry. Any addition exterior of a standard software program set up needs to be investigated intently to detect malware exercise.
- Block pre-calculated DGA domains by way of DNS.
- Deploy endpoint safety software program on each laptop to detect malware.
- Educate customers and employees to detect phishing emails and potential fraud makes an attempt.
- Preserve all {hardware} and software program updated and patched so as to not be contaminated by way of a typical vulnerability.
Disclosure: I work for Development Micro, however the views expressed on this article are mine.