SUMMARY
- Cybersecurity agency watchTowr found over 4,000 energetic hacker backdoors counting on expired domains.
- These backdoors are pre-existing entry factors on already compromised methods, permitting new actors to use earlier breaches.
- By registering these expired domains, watchTowr noticed compromised methods “phoning home,” together with authorities hosts in a number of international locations.
- The analysis highlights a regarding pattern of attackers exploiting deserted backdoors left by different hackers, making a “hacking-on-autopilot” state of affairs.
- Many older net shells, instruments used for distant entry, comprise built-in mechanisms that unintentionally expose compromised methods by way of callbacks to now-expired domains.
Cybersecurity researchers at watchTowr have recognized over 4,000 stay hacker backdoors, exploiting deserted infrastructure and expired domains. These backdoors, hidden in compromised methods worldwide, have uncovered an enormous community of weak authorities and academic establishments.
The investigation started when watchTowr registered over 40 expired domains, beforehand utilized by hackers, and arrange logging servers to trace incoming requests. The workforce collected 300MB of knowledge, revealing a community of compromised hosts, together with government-owned methods in Bangladesh, China, Nigeria, and extra.
The researchers found that hackers had been utilizing these deserted backdoors to realize entry to hundreds of methods, with out investing effort in figuring out and compromising them. This method has been termed by researchers as a “mass-hacking-on-autopilot” method, permitting hackers to commandeer and management compromised hosts, doubtlessly resulting in devastating penalties.
One notable instance, in accordance with watchTowr’s technical report shared with Hackread.com, is a backdoor linked to the Lazarus Group, a infamous hacking collective related to North Korea. The researchers discovered over 3,900 distinctive compromised domains utilizing this backdoor, which was designed to load a .gif picture from the logging server, leaking the situation of the compromised system.
Easy Rationalization
To grasp this higher, take into account the idea of a “web shell.” These are primarily small snippets of code secretly positioned on an internet server after a profitable breach. They act as distant management panels, permitting attackers to execute instructions, handle recordsdata, and even deploy additional malicious instruments.
Traditionally, these net shells usually included mechanisms that “phoned home” to a particular area or server managed by the attacker. When that area expires and is re-registered by another person, these “phone calls” at the moment are answered by an sudden recipient.
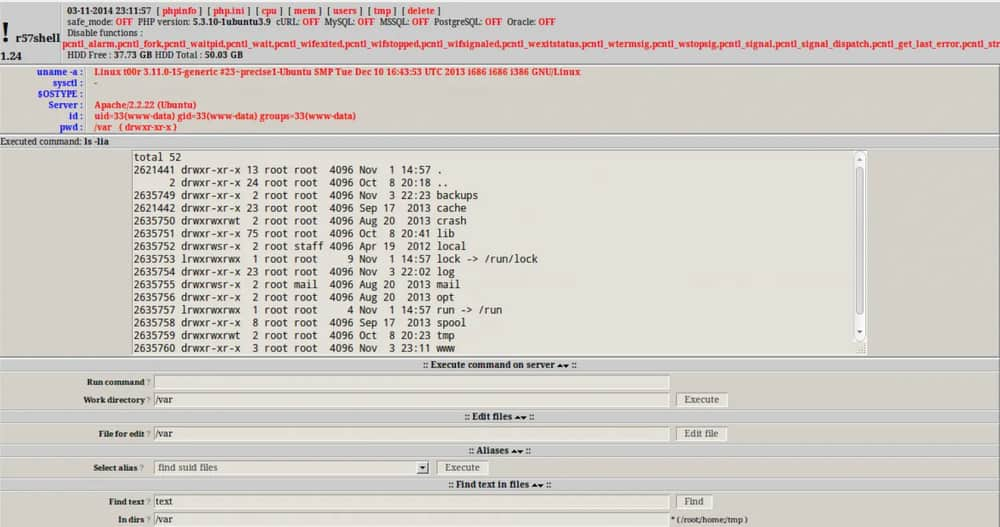
Older net shells, just like the notorious “r57shell” and “c99shell,” whereas outdated, nonetheless seem like in use. Apparently, a few of these older shells even contained built-in backdoors for the shell’s creator. This meant that even when the preliminary attacker secured their entry with a password, the unique writer may nonetheless achieve entry utilizing a secret “master key.” This highlights a historical past of the hacking group itself having a considerably chaotic method to safety.
In a single instance, researchers noticed an internet shell continually sending the login credentials (in plain textual content!) to a website that watchTowr now managed. The attacker believed that they had secured their entry, however the very device they have been utilizing was betraying them.
The report additionally highlights the vulnerability of presidency establishments, with compromised methods discovered within the Federal Excessive Courtroom of Nigeria and different authorities entities. The researchers emphasize that these findings exhibit the significance of accountable infrastructure administration and the necessity for elevated consciousness in regards to the dangers of deserted and expired domains.
Harmful State of affairs
The watchTowr workforce warns that issues like it will persist, with penalties for software program updates, cloud infrastructure, and SSLVPN home equipment. The report additionally highlights that even attackers could make errors, as demonstrated by one other analysis from researchers at vpnMentor. They recognized high-profile teams, comparable to ShinyHunters and Nemesis, that exploited AWS buckets to steal over 2 terabytes of delicate knowledge. Within the course of, these teams inadvertently uncovered their very own S3 buckets.
The excellent news is that The Shadowserver Basis has agreed to take possession of the implicated domains and sinkhole them, stopping additional exploitation. The watchTowr workforce’s analysis serves as a vital reminder of the significance of accountable infrastructure administration and the necessity for elevated consciousness in regards to the dangers of deserted and expired domains.
RELATED TOPICS
- 99% of UAE’s .ae Domains Uncovered to Phishing and Spoofing
- Controller flaws let hackers bodily harm transferring bridges
- US and Europe Account for 73% of World Uncovered ICS Methods
- Hundreds of Uncovered ICSs in US and UK Threaten Water Provides
- “Revolver Rabbit” Hacker Makes use of RDGA to Register 500,000 Domains