Simply as a house owner would possibly grapple with looking for the supply of a water leak, the problem of figuring out and plugging a leak in code, particularly one involving ‘secrets and techniques’ like login credentials, SSH Keys, API Keys, and AWS tokens will be simply as irritating for builders and cybersecurity professionals.
There was a latest uptick in leaks, most notably Mercedes-Benz and Soccer Australia, who discovered themselves as victims in incidents that spotlight the necessity for strong knowledge safety methods.
The Mercedes-Benz Supply Code Publicity
Mercedes-Benz confronted a big breach when an worker inadvertently printed a non-public authentication token on a public GitHub repository, granting unfettered entry to the corporate’s supply code. This error was found by RedHunt Labs throughout a routine scan in January, revealing that the uncovered token offered full entry to Mercedes’s GitHub Enterprise Server. This entry degree meant that anybody with the token might obtain non-public repositories containing delicate knowledge, together with mental property, cloud entry keys for Microsoft Azure and Amazon Internet Providers (AWS), database connection strings, and different crucial inner data.
The Incident at Soccer Australia
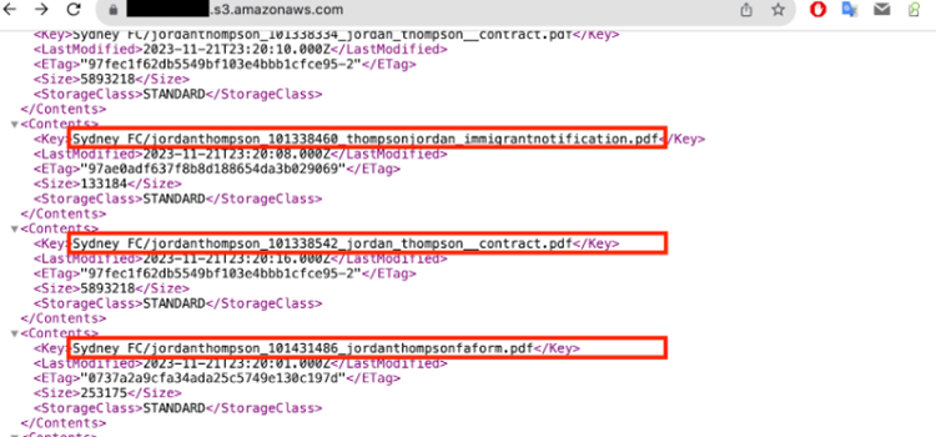
Cybernews researchers reported a big knowledge leak at Soccer Australia, the place private data of Australian soccer gamers (together with passports and contracts), in addition to buyer buy particulars, have been uncovered on-line. The safety breach lasted for no less than 681 days and will doubtlessly impression many native clients, with over 100 buckets of information uncovered. The uncovered knowledge poses a extreme menace, with potential for identification theft and fraud.
This cybersecurity incident, attributed to human error, resulted from a leak of secrets and techniques from plain-text Amazon Internet Providers (AWS) keys. This allowed public entry to 127 digital storage containers containing delicate knowledge.
Pattern of the uncovered knowledge. Picture by Cybernews.
Classes Discovered
These incidents function potent reminders of the vulnerabilities inherent in digital infrastructures throughout all sectors. They spotlight the necessity for:
- Enhanced Secret Administration: Using instruments and practices that make sure the safe dealing with of keys and tokens is non-negotiable.
- Common Safety Audits: Proactively scanning for vulnerabilities and exposures can stop potential breaches.
- Training and Consciousness: Human error being a typical consider each instances, underscores the significance of steady schooling on finest practices for all personnel concerned in dealing with delicate data.
- Incident Response Planning: Each organizations acted swiftly upon discovery, a testomony to the significance of getting an efficient incident response technique in place.
The cybersecurity incidents confronted by Soccer Australia and Mercedes-Benz illuminate the crucial want for heightened safety measures and vigilant administration of digital property. Let these tales be a rallying cry for a unified strategy to defending our digital world—from the pitch to the pavement.
Sustaining the Sanctity of Secrets and techniques
To avert the leakage of secrets and techniques, think about implementing these methods:
- Atmosphere Variables for Secrets and techniques: Retailer secrets and techniques in setting variables somewhat than embedding them instantly in code to facilitate simpler administration and forestall their unintentional inclusion in model management.
- .gitignore for Delicate Recordsdata: Make the most of a .gitignore file to exclude recordsdata containing secrets and techniques from Git monitoring. This ensures that these particulars don’t inadvertently enter model management techniques. If utilizing setting variables for secrets and techniques, guarantee their related recordsdata are additionally ignored.
- Secrets and techniques Administration Instruments: Make use of secrets and techniques administration instruments for the safe dealing with and storage of system or utility secrets and techniques. This ensures encryption and entry solely to licensed people.
- Encryption of Secrets and techniques: Encrypt secrets and techniques previous to their storage in code repositories so as to add a safety layer, making it difficult for attackers to acquire delicate data.
- Two-Issue Authentication (2FA): Activate 2FA for entry to code repositories, enhancing safety and complicating unauthorized repository entry efforts.
These practices can considerably mitigate the chance of inadvertently exposing delicate data throughout varied platforms, together with code repositories, content material administration techniques, emails, and different digital property not contained inside a repository.
Stopping secrets and techniques from leaking on exterior instruments with Secrets and techniques Detection by Checkmarx
Secrets and techniques Detection integrates and expands deeper scanning capabilities of Too many secrets and techniques 2MS, a command line device written in Go language and constructed over gitleaks, instantly into Checkmarx One. 2MS is likely one of the hottest open-source instruments for secret detection, with over 2 million downloads. Secrets and techniques Detection in Checkmarx One finds secrets and techniques similar to login credentials, API keys, SSH keys and extra hidden in code, content material techniques, chat purposes and extra.
- Supported instruments embrace Confluence, Discord, filesystem, git, paligo, Slack, Git Hooks, GitHub Actions
- Scan historical past to make sure secrets and techniques will not be leaked in any earlier variations
- Detect secrets and techniques which might be particular to your organization with secret customization
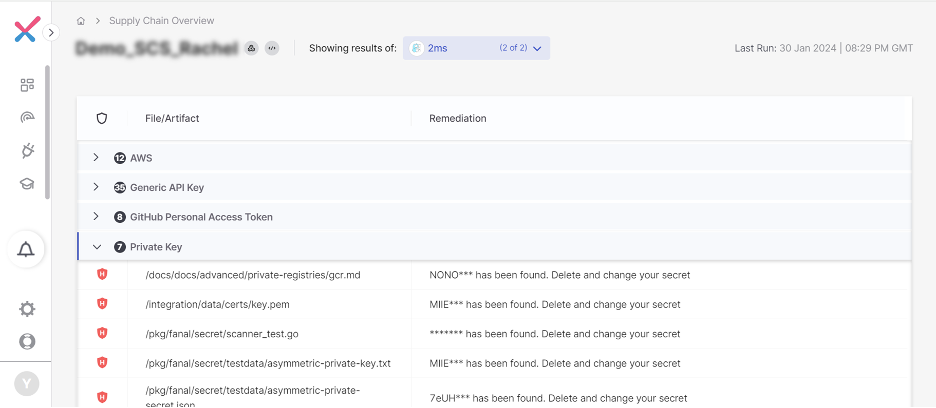
Study extra about lowering the chance of leaked secrets and techniques throughout the provision chain